Microsoft shares script to fix WinRE BitLocker bypass flaw

Microsoft has released a script to make it easier to patch a BitLocker bypass security vulnerability in the Windows Recovery Environment (WinRE).
This PowerShell script simplifies the process of securing WinRE images against attempts to exploit the CVE-2022-41099 flaw that enables attackers to bypass the BitLocker Device Encryption feature system storage devices.
Successful exploitation of this enables threat actors with physical access to access encrypted data in low-complexity attacks.

According to Microsoft, the vulnerability cannot be exploited if the user has enabled BitLocker TPM+PIN protection.
“The sample PowerShell script was developed by the Microsoft product team to help automate the updating of WinRE images on Windows 10 and Windows 11 devices,” Microsoft says in a support document published on Thursday.
“Run the script with Administrator credentials in PowerShell on the affected devices. There are two scripts available—which script you should use depends on the version of Windows you are running.”
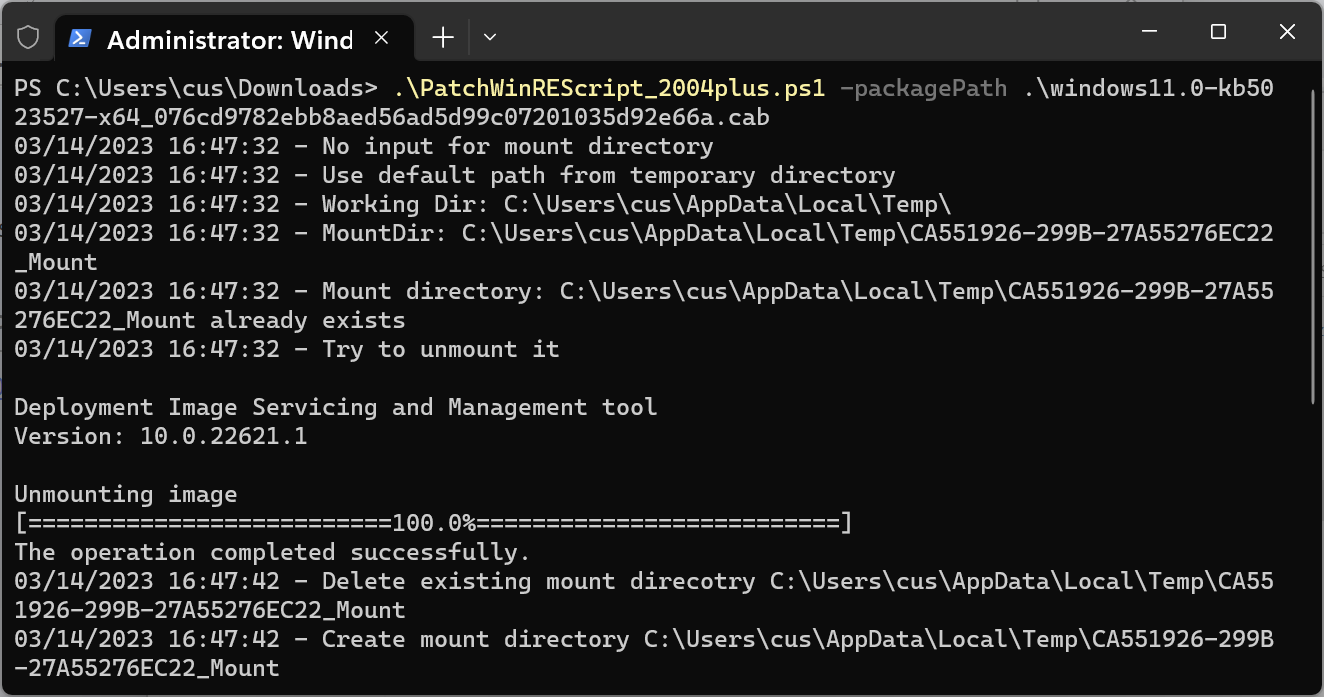
The recommended script version is PatchWinREScript_2004plus.ps1 which helps apply the security updates on systems running Windows 10 2004 and later (including Windows 11).
The other PowerShell script (PatchWinREScript_General.ps1) is less robust and should be used on Windows 10 1909 and earlier versions (although it will run on all Windows 10 and Windows 11 systems).

How to use the WinRE patch script
The CVE-2022-41099 patch scripts can be run from a Windows PowerShell and allow admins to specify the path and name of the Safe OS Dynamic update package that should be used to update the WinRE image.
These update packages are OS-version-specific and processor architecture-specific and have to be downloaded from the Microsoft Update Catalog beforehand.
The scrips also allow passing a workDir parameter to select the scratch space to be used during the patching process (if not specified, the script will use the default Windows temp folder).
Once started, the script will go through the following steps:
- Mount the existing WinRE image (WINRE.WIM).
- Update the WinRE image with the specified Safe OS Dynamic Update (Compatibility Update) package available from the Windows Update Catalog (the latest update available for the version of Windows installed on the device is recommended)
- Unmount the WinRE image.
- If the BitLocker TPM protector is present, it reconfigures WinRE for BitLocker service.
After running the script, you will not be required to reboot the system to complete the WinRE image patching process.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below




To keep up to date follow us on the below channels.





