MITRE introduces D3FEND framework
The US National Security Agency (NSA) has announced it will fund the development of a knowledge base of defensive countermeasures for the most common techniques used by malicious threat actors.
The project will be made available through MITRE and will be called D3FEND as it complements MITRE’s existing ATT&CK framework.
MITRE ATT&CK
The MITRE Corporation is a non-profit organization with the mission to “solve problems for a safer world”. It wants to bring security focused communities together to develop more effective cybersecurity. Where most people may have heard of MITRE because it runs the CVE database of known vulnerabilities, another widely respected resource is its MITRE ATT&CK framework.
MITRE ATT&CK framework is a knowledge base of offensive tactics and techniques based on real-world observations. It contains information about malicious groups and techniques, and it’s open and available to any person or organization for use at no charge. It’s used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.
An ATT&CK example
The MITRE ATT&CK framework is divided into a number of groups that reflect different stages of an ongoing attack.
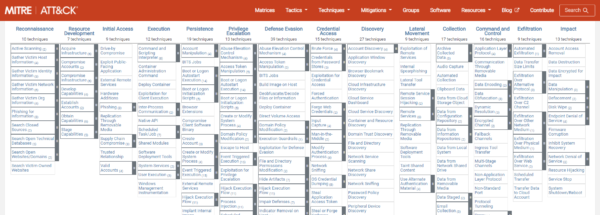
As an example, let’s look at the entry “Phishing for information” in the “Reconnaissance” stage.
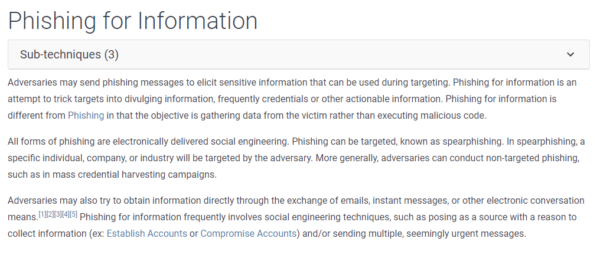
Users will find a description of the attack vector and some real-world examples, with links to articles or blogs about them. If you look under “Spearphishing” > “Higaisa” you will find a link to our own blogpost about Higaisa, for example. Further down below the description of the attack vector you can find “Mitigations” and “Detection” techniques against the attack vector.
MITRE D3FEND
So, now MITRE has started to build a similar framework for network defense, with NSA funding. The goal is to help security architects quickly understand the specific capabilities of a wide variety of defensive technologies. This framework will be shared publicly so everyone can use it, and benefit from it in the same way they use the ATT&CK framework.
The main entry to the knowledge base can be found at d3fend.mitre.org.
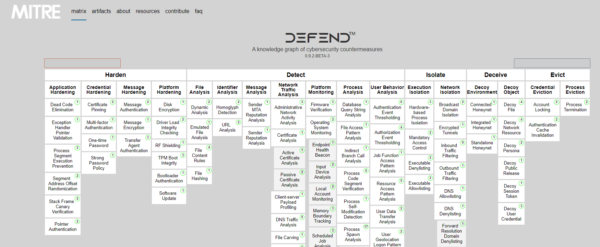
As you can tell from the layout the defensive techniques have been grouped into a similar linear arrangement to Harden, Detect, Isolate, Deceive and Evict.
Let’s look at an example in the new knowledge base, I’ll grab one that we happen to know a lot about: “File Content Rules“, under “Detect” > “File Analysis”.
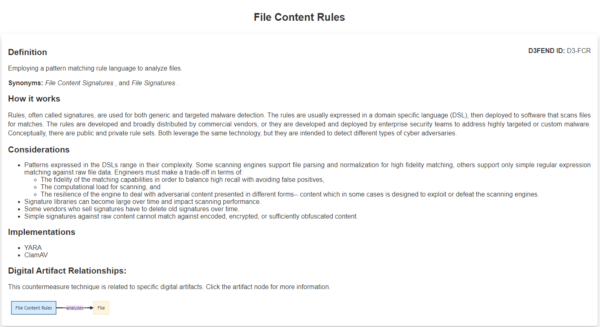
The entry for “File Content Rules” explains how this simple method of pattern matching works and what some use-cases are. But lower down is the more interesting part. The knowledge bases ATT&CK and D3FEND are tied together by highlighting the ATT&CK techniques related to this D3FEND entry.
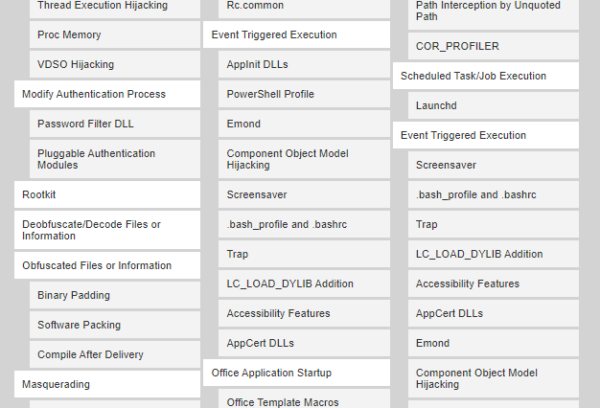
Conclusion
I must say that one of the sentences in the NSA announcement trying to explain the mission of D3FEND put me on the wrong foot.
“D3FEND enables cybersecurity professionals to tailor defenses against specific cyber threats, thereby reducing a system’s potential attack surface.”
The “tailor defenses against specific cyber threats” immediately gave me the mental image of a game of whack-a-mole. But looking at what has been established so far I think the following sentence describes the project a lot better.
“Our goal is to make it easier for architects to better understand how countermeasures work, so that they can more effectively design, deploy, and ultimately better defend networked systems.”
As explained by Peter Kaloroumakis, a principal cybersecurity engineer at MITRE who leads the work on D3FEND.
It’s about being able to make an assessment whether you have all the bases covered that you feel are worth covering in your case. Many organizations have a special threat model and need stronger defenses in one area and not so much in others. This gives them a tool to check whether they missed something or where improvements are possible.
Implementation
MITRE and the NSA have urged organizations today to start implementing the D3FEND framework into their security plans as soon as possible. The MITRE Corporation has also released a technical whitepaper (PDF) describing the basic principles and the design of this new framework.
The post MITRE introduces D3FEND framework appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



![Cobalt Strike Beacon Detected - 47[.]106[.]229[.]212:443 10 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)