Multinational tech firm ABB hit by Black Basta ransomware attack

Swiss multinational company ABB, a leading electrification and automation technology provider, has suffered a Black Basta ransomware attack, reportedly impacting business operations.
Headquartered in Zurich, Switzerland, ABB employs approximately 105,000 employees and has $29.4 billion in revenue for 2022. As part of its services, the company develops industrial control systems (ICS) and SCADA systems for manufacturing and energy suppliers.
The company works with a wide range of customers and local governments, including Volvo, Hitachi, DS Smith, the City of Nashville, and the City of Zaragoza.
“ABB operates more than 40 U.S.-based engineering, manufacturing, research and service facilities with a proven track record serving a diversity of federal agencies including the Department of Defense, such as U.S. Army Corps of Engineers, and Federal Civilian agencies such as the Departments of Interior, Transportation, Energy, United States Coast Guard, as well as the U.S. Postal Service,” reads the ABB web site.
On May 7th, the company fell victim to a ransomware attack conducted by Black Basta, a cybercrime group that surfaced in April 2022.
BleepingComputer has learned from multiple employees that the ransomware attack has affected the company’s Windows Active Directory, affecting hundreds of devices.
In response to the attack, ABB terminated VPN connections with its customers to prevent the spread of the ransomware to other networks.
BleepingComputer independently confirmed the attack from a source familiar with the situation and who asked to remain anonymous.
The attack reportedly disrupts the company’s operations, delaying projects and impacting the factories.
BleepingComputer contacted ABB about the attack, but they declined to comment.
Who is Black Basta?
The Black Basta ransomware gang launched its Ransomware-as-a-Service (RaaS) operation in April 2022 and quickly began amassing corporate victims in double-extortion attacks.
By June 2022, Black Basta had partnered with the QBot malware operation (QakBot), which dropped Cobalt Strike on infected devices. Black Basta would then use Cobalt Strike to gain initial access to the corporate network and spread laterally to other devices.
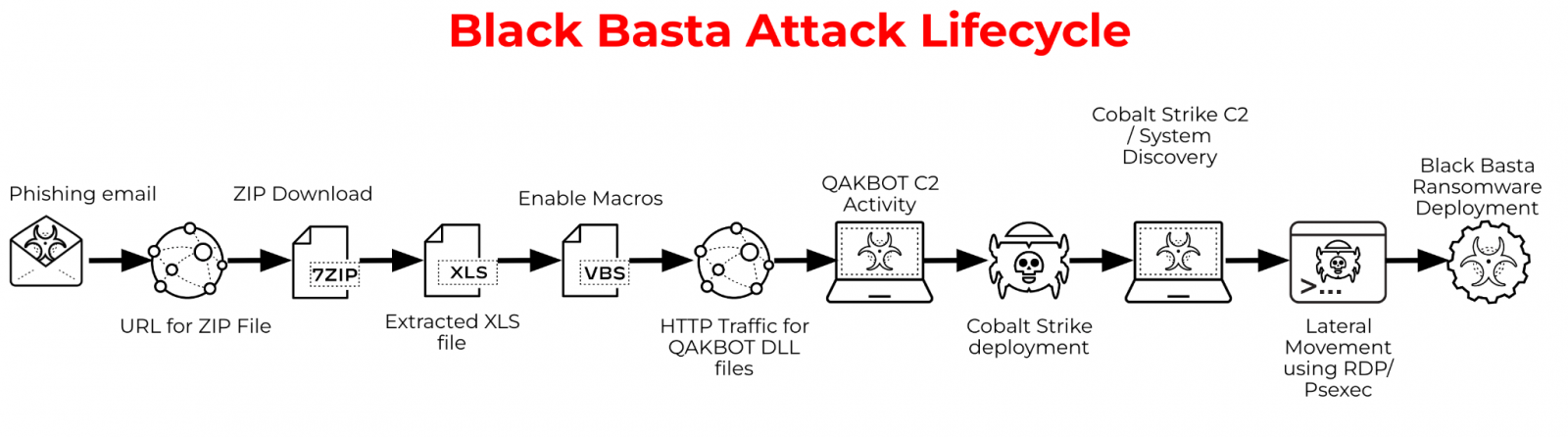
Source: Palo Alto Networks Unit 42
Like other enterprise-targeting ransomware operations, Black Basta created a Linux encryptor to target VMware ESXi virtual machines running on Linux servers.
Researchers have also linked the ransomware gang to the FIN7 hacking group, a financially motivated cybercrime gang also known as Carbanak.
Since its launch, the threat actors have been responsible for a stream of attacks, including those on the American Dental Association, Sobeys, Knauf, and Yellow Pages Canada.
Recently, the ransomware operation attacked Capita, the UK’s largest outsourcing company, and began to leak stolen data.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.





![Cobalt Strike Beacon Detected - 15[.]229[.]22[.]115:443 9 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
