NameCheap’s email hacked to send Metamask, DHL phishing emails

Domain registrar Namecheap had their email account breached Sunday night, causing a flood of MetaMask and DHL phishing emails that attempted to steal recipients’ personal information and cryptocurrency wallets.
The phishing campaigns started around 4:30 PM ET and originated from SendGrid, an email platform used historically by Namecheap to send renewal notices and marketing emails.
After recipients began complaining on Twitter, Namecheap CEO Richard Kirkendall confirmed that the account was compromised and that they disabled email through SendGrid while they investigated the issue.
Kirkendall also said that they believe the breach may be related to a December CloudSek report on the API keys of Mailgun, MailChimp, and SendGrid being exposed in mobile apps.
A flood of emails
The phishing emails sent in this campaign are impersonating either DHL or MetaMask.
The DHL phishing email pretends to be a bill for a delivery fee required to complete the delivery of a package. While BleepingComputer has not received this email, we were told that the embedded links lead to a phishing page attempting to steal the target’s information.
Beware of phishing emails coming out of @Namecheap’s @SendGrid account. DHL, MetaMask, digitally signed with DKIM. Looks like low level hackers were able to get into their systems. PII looks to be exposed. pic.twitter.com/IuLE8mo2w6
— Kathy Zant (@kathyzant) February 12, 2023
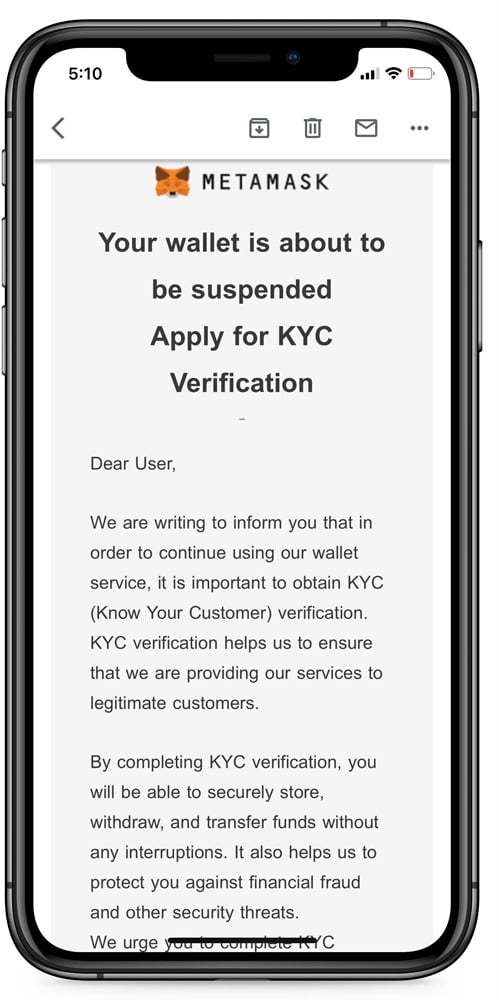
BleepingComputer did receive the MetaMask phishing email, which pretends to be a required KYC (Know Your Customer) verification to prevent the wallet from being suspended.
Source: BleepingComputer.com
“We are writing to inform you that in order to continue using our wallet service, it is important to obtain KYC (Know Your Customer) verification. KYC verification helps us to ensure that we are providing our services to legitimate customers,” reads the MetaMask phishing email.
“By completing KYC verification, you will be able to securely store, withdraw, and transfer funds without any interruptions. It also helps us to protect you against financial fraud and other security threats.”
“We urge you to complete KYC verification as soon as possible to avoid suspension of your wallet.”
This email contains a marketing link from Namecheap (https://links.namecheap.com/) that redirects the user to a phishing page pretending to be MetaMask.
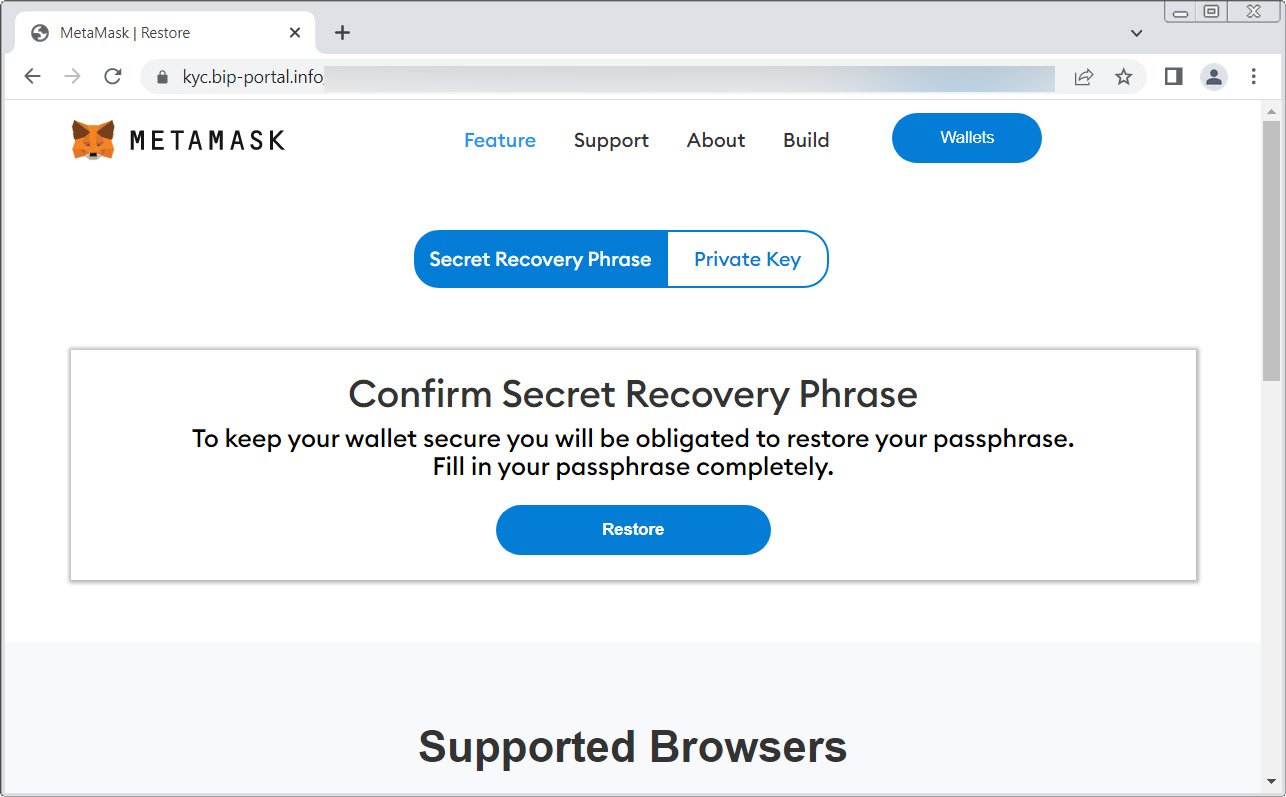
This page prompts the user to enter their ‘Secret Recovery Phrase’ or ‘Private key,’ as shown below.
Source: BleepingComputer
Once a user provides either the recovery phrase or private key, the threat actors can use them to import the wallet to their own devices and steal all the funds and assets.
If you received either a DHL or MetaMask phishing email tonight from Namecheap, immediately delete it and do not click on any links.
Namecheap blames “upstream system”
Namecheap published a statement Sunday night stating that their systems were not breached but rather it was an issue at an upstream system that they use for email.
“We have evidence that the upstream system we use for sending emails (third-party) is involved in the mailing of unsolicited emails to our clients. As a result, some unauthorized emails might have been received by you,” reads a statement issued by Namecheap.
“We would like to assure you that Namecheap’s own systems were not breached, and your products, accounts, and personal information remain secure.”
After the phishing incident, Namecheap says they stopped all emails, including two-factor authentication code delivery, trusted devices’ verification, and password reset emails, and began investigating the attack with their upstream provider. Services were restored later that night at 7:08 PM EST.
While Namecheap did not state the name of this upstream system, the CEO of Namecheap previously tweeted that they were using SendGrid, which is also confirmed in the phishing emails’ mail headers.
However, Twilio SendGrid told BleepingComputer that Namecheap’s incident was not the result of a hack or compromise of the email service provider’s systems, adding more confusion as to what happened.
“Twilio SendGrid takes fraud and abuse very seriously and invests heavily in technology and people focused on combating fraudulent and illegal communications. We are aware of the situation regarding the use of our platform to launch phishing email and our fraud, compliance and cyber security teams are engaged in the matter. This situation is not the result of a hack or compromise of Twilio’s network. We encourage all end users and entities to take a multi-pronged approach to combat phishing attacks, deploying security precautions such as two factor authentication, IP access management, and using domain-based messaging. We are still investigating the situation and have no additional information to provide at this time.” Twilio Corp.
BleepingComputer contacted Twilio with further questions about the incident, but an answer was not immediately available.
We also contacted Namecheap earlier this evening with questions about the incident but did not receive a response.
Update 2/12/23 11:54 PM ET: Added Namecheap’s statement.
A big thanks to our reader Isaac for sharing the news.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.






