Nearly 2,000 Citrix NetScaler Instances Hacked via Critical Vulnerability
Nearly 2,000 Citrix NetScaler instances have been compromised with a backdoor by weaponizing a recently disclosed critical security vulnerability as part of a large-scale attack.
“An adversary appears to have exploited CVE-2023-3519 in an automated fashion, placing web shells on vulnerable NetScalers to gain persistent access,” NCC Group said in an advisory released Tuesday.
“The adversary can execute arbitrary commands with this webshell, even when a NetScaler is patched and/or rebooted.”
CVE-2023-3519 refers to a critical code injection vulnerability impacting NetScaler ADC and Gateway servers that could lead to unauthenticated remote code execution. It was patched by Citrix last month.
The development comes a week after the Shadowserver Foundation said it identified close to 7,000 vulnerable, unpatched NetScaler ADC and Gateway instances online and the flaw is being abused to drop PHP web shells on vulnerable servers for remote access.
A follow-up analysis by NCC Group has now revealed that 1,828 NetScaler servers remain backdoored, out of which roughly 1,248 are already patched against the flaw.
“This indicates that while most administrators were aware of the vulnerability and have since patched their NetScalers to a non-vulnerable version, they have not been (properly) checked for signs of successful exploitation,” the company said.
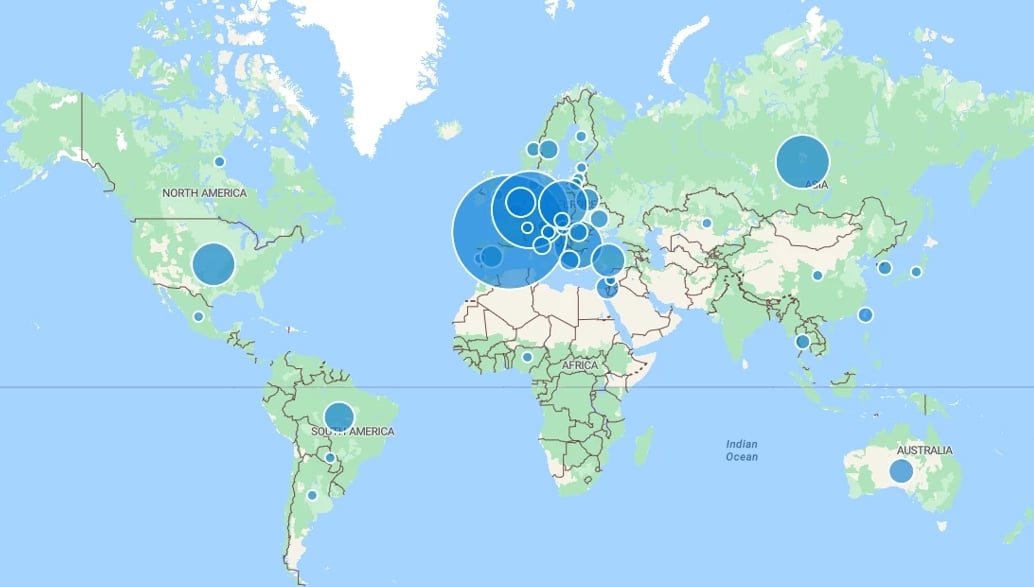
In total, as many as 2,491 web shells have been found across 1,952 distinct NetScaler appliances. A majority of the compromised instances are located in Germany, France, Switzerland, Japan, Italy, Spain, the Netherlands, Ireland, Sweden, and Austria.
The European focus aside, another notable aspect is that while Canada, Russia, and the U.S. had thousands of vulnerable NetScaler servers late last month, no web shells were found on any of them.
The mass exploitation campaign is estimated to have compromised 6.3% of the 31,127 NetScaler instances that were susceptible to CVE-2023-3519 as of July 21, 2023.
The disclosure also arrives as Mandiant has released an open-source tool to help organizations scan their Citrix appliances for evidence of post-exploitation activity related to CVE-2023-3519.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


![Cobalt Strike Beacon Detected - 1[.]94[.]105[.]46:81 1 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)