New Android FluHorse malware steals your passwords, 2FA codes

A new Android malware called ‘FluHorse’ has been discovered, targeting users in Eastern Asia with malicious apps that imitate legitimate versions.
The malware was discovered by Check Point Research, which reports that it has been targeting various sectors of Eastern Asia since May 2022.
The FluHorse malware is distributed via email, while its goal is to steal its target’s account credentials and credit card data and, if needed, snatch two-factor authentication (2FA) codes.
High-profile targets
FluHorse attacks begin with malicious emails sent to high-profile targets, urging them to take immediate action to resolve a payment issue.

Typically, the victim is led to a phishing site via a link provided in the email, where they download the fake app APK (Android package file) from.
The apps mimicked by the FluHorse carrier apps are ‘ETC,’ a toll-collection app used in Taiwan, and ‘VPBank Neo,’ a banking app in Vietnam. Both legitimate versions of these apps have over a million downloads each on Google Play.
Check Point has also observed the malware posing as a transportation app used by 100,000 people, but its name wasn’t disclosed in the report.
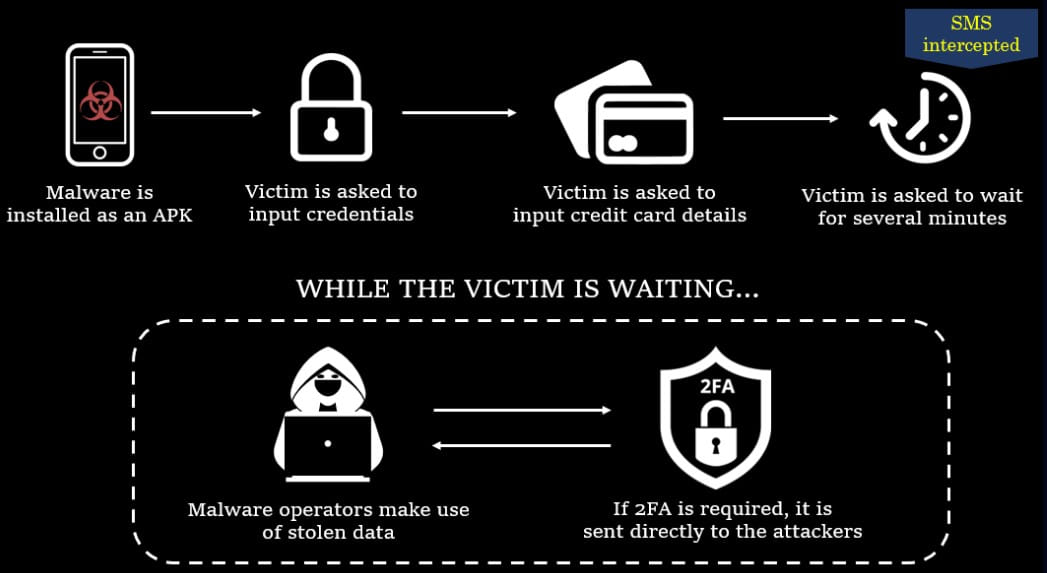
All three fake apps request SMS access upon installation to intercept incoming 2FA codes in case it’s needed to hijack the accounts.
(Check Point)
The analysts comment that the fake apps copy the GUI of the originals but do not feature much functionality besides two-three windows that load the forms which capture the victim’s information.
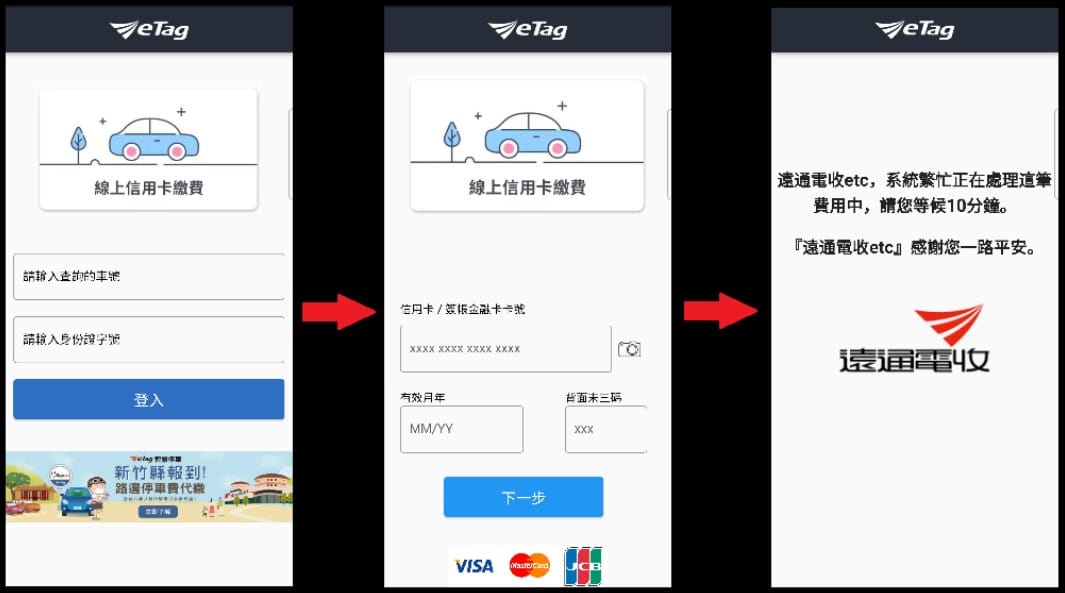
After capturing the victims’ account credentials and credit card details, the apps display a “system is busy” message for 10 minutes, likely to make the process appear realistic while the operators act in the background to intercept 2FA codes and leverage the stolen data.
CheckPoint says that the malicious apps were built in Dart, using the Flutter platform, and reverse engineering and decompiling the malware was challenging.
“Flutter runtime for ARM uses its own stack pointer register (R15) instead of the built-in stack pointer (SP),” reads Check Point’s report.
“Which register is used as a stack pointer makes no difference in code execution or in the reverse-engineering process. However, it makes a big difference for the decompiler. Because of a non-standard register usage, a wrong and ugly pseudocode is generated.”
The analysis was so challenging that CheckPoint ended up contributing improvements to existing open-source tools like ‘flutter-re-demo’ and ‘reFlutter.’
Ultimately, this work revealed the functions responsible for exfiltrating victims’ credentials, credit card data, and the HTTP POST communication that sent the intercepted SMS messages to the C2 server.
CheckPoint warns that the FluHorse campaign is ongoing, with new infrastructure and malicious apps appearing each month, so this is an active threat for Android users.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.





