New ‘HTTP/2 Rapid Reset’ zero-day attack breaks DDoS records

A new DDoS (distributed denial of service) technique named ‘HTTP/2 Rapid Reset’ has been actively exploited as a zero-day since August, breaking all previous records in magnitude.
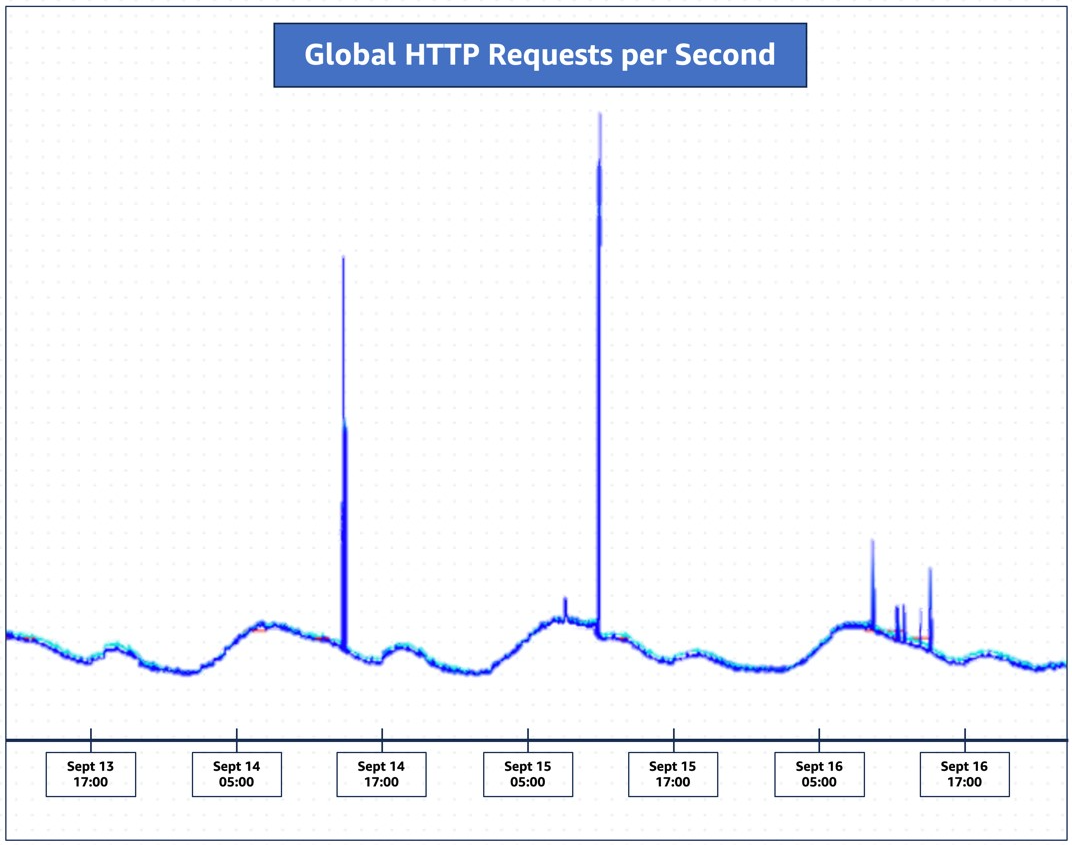
News of the zero-day technique comes as a coordinated announcement today between Amazon Web Services, Cloudflare, and Google, who report mitigating attacks reaching 155 million requests per second (Amazon), 201 million rps (Cloudflare), and a record-breaking 398 million rps (Google).
Google says they were able to mitigate these new attacks by adding further capacity on the edge of their network.
Cloudflare comments that the size of the attack it mitigated is three times bigger than its previous record, from February 2023 (71 million rps), and it’s alarming that this was achieved using a relatively small botnet comprising 20,000 machines.
Since late August, Cloudflare has detected and mitigated over a thousand ‘HTTP/2 Rapid Reset’ DDoS attacks that surpassed 10 million rps, with 184 breaking the previous 71 million rps record.
Cloudflare is confident that as further threat actors employ more expansive botnets along with this new attack method, HTTP/2 Rapid Reset attacks will continue to break even greater records.
“There are botnets today that are made up of hundreds of thousands or millions of machines,” comments Cloudflare.
“Given that the entire web typically sees only between 1–3 billion requests per second, it’s not inconceivable that using this method could focus an entire web’s worth of requests on a small number of targets.”
HTTP/2 Rapid Reset details
The novel attack exploits a zero-day vulnerability tracked as CVE-2023-44487, which abuses a weakness in the HTTP/2 protocol.
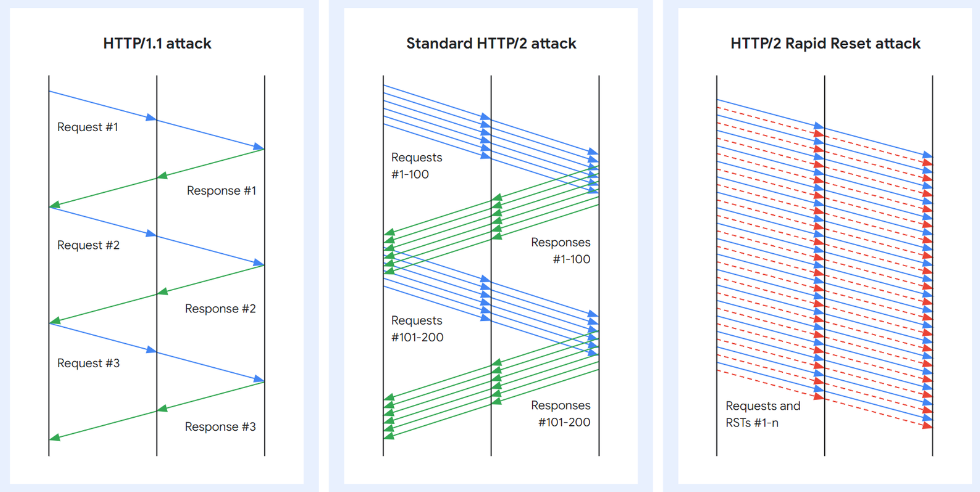
Simply put, the attack method abuses HTTP/2’s stream cancellation feature to continuously send and cancel requests, overwhelming the target server/application and imposing a DoS state.
HTTP/2 features a safeguard in the form of a parameter that limits the number of concurrently active streams to prevent DoS attacks; however, this isn’t always effective.
The protocol developers introduced a more efficient measure called “request cancelation,” which doesn’t tear down the whole connection but which can be abused.
Malicious actors have been abusing this feature since late August to send a flurry of HTTP/2 requests and resets (RST_Stream frames) on a server, asking it to process each of them and perform rapid resets, overwhelming its capacity to respond to new incoming requests.
“The protocol does not require the client and server to coordinate the cancelation in any way, the client may do it unilaterally,” explains Google in its post on the issue.
“The client may also assume that the cancellation will take effect immediately when the server receives the RST_STREAM frame, before any other data from that TCP connection is processed.”
Providers develop mitigations
Cloudflare explains that HTTP/2 proxies or load-balancers are particularly susceptible to those long strings of reset requests sent quickly.
The firm’s network was overwhelmed at the point between the TLS proxy and its upstream counterpart, so the damage was done before the bad requests reached the block point.
In terms of real-world impact, these attacks have caused an increase in 502 error reports among Cloudflare’s clients.
Cloudflare says it eventually mitigated these attacks using a system designed to handle hyper-volumetric attacks called ‘IP Jail,’ which the internet firm expanded to cover its entire infrastructure.
This system “jails” offending IPs and bars them from using HTTP/2 for any Cloudflare domain for a period of time while impacting legitimate users sharing the jailed IP with a minor performance drop.
Amazon says it mitigated dozens of these attacks without providing any details on their impact, highlighting that the availability of their customer services was maintained.
All three firms conclude that the best approach for clients to counter HTTP/2 Rapid Reset attacks is to use all available HTTP-flood protection tools and bolster their DDoS resilience with multifaceted mitigations.
Unfortunately, as this tactic abuses the HTTP/2 protocol, there is no general fix that entirely blocks attackers from using this DDoS technique.
Instead, software developers who utilize the protocol in their software are implementing rate controls to mitigate HTTP/2 Rapid Reset attacks.
In a separate post, Cloudflare explains that they had to keep the zero-day secret for over a month to allow security vendors and stakeholders time to react to the threat before it’s made known to more threat actors and the “cat and mouse” game begins.
“We’ve kept the information restricted until today to give as many security vendors as possible the opportunity to react,” explained Cloudflare
“However, at some point, the responsible thing becomes to publicly disclose zero-day threats like this. Today is that day.”
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![Cobalt Strike Beacon Detected - 45[.]143[.]233[.]205:80 5 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)