New Mac malware masquerades as iTerm2, Remote Desktop and other apps
Last week, security researcher Patrick Wardle released details of a new piece of malware masquerading as the legitimate app iTerm2. The malware was discovered earlier the same day by security researcher Zhi (@CodeColorist on Twitter), and detailed on a Chinese-language blog. (For those who don’t speak Chinese, Safari seems to do a fair job of translating it.)
iTerm2 is a legitimate replacement for the macOS Terminal app, offering some powerful features that Terminal does not. It is frequently used by power users. It is a favorite of security researchers because of the propensity for Mac malware to take control or detect usage of the Terminal app, which can interfere with attempts to reverse engineer malware. This makes iTerm2 an ideal app to trojanize to infect people who may have access to development system, research intelligence, etc.
The website for the legitimate iTerm2 app is iTerm2.com. However, the malicious version of iTerm2 was apparently being distributed via iTerm2[.]net, which was a very convincing duplicate of the legitimate iTerm2 site.
Clicking the download link on the lookalike site would result in an iTerm2.dmg disk image file being downloaded from kaidingle[.]com.
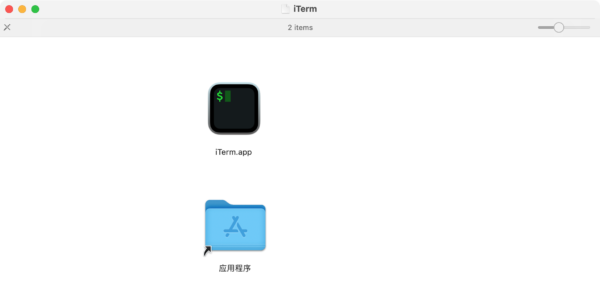
The disk image throws the first red flag. The real iTerm2 is distributed in a zip file, rather than a disk image. Further, for an app with a very professionally designed website, the disk image file is quite unpolished. It also includes a link to the Applications folder with a Chinese name, which is unusual for an app that is English-only and does not contain any Chinese localization files.
Malware behavior
The malicious iTerm2 app appears to be a legitimate copy of the iTerm2 app, but with one file added:
iTerm.app/Contents/Frameworks/libcrypto.2.dylib
When launched, the malicious app loads and runs the malicious libcrypto.2.dylib dynamic library, which in turn does a couple things.
The main purpose seems to be to connect to 47.75.123[.]111, from which it downloads a Python file named g.py and a mach-O binary named GoogleUpdate into the /tmp folder, then executes both of them.
The GoogleUpdate binary is heavily obfuscated, and it’s currently not known exactly what it does. However, according to Patrick, it communicates with what appears to be a Cobalt Strike server (47.75.96[.]198:443), which may mean it is a Cobalt Strike “beacon,” which would provide comprehensive backdoor access to the attacker.
The g.py file is clear-text Python code, and thus its intent is quite clear. It collects the following data:
- Machine serial number.
- Contents of the user’s home, desktop, Documents, and Downloads folders.
- Applications folder contents.
- Command histories for
bashandzsh, which can contain sensitive information such as credentials. - The git config file, which contains potentially sensitive information, including an e-mail password.
- The
/etc/hostsfile, which can contain details on custom servers accessed by the user. - The
.sshfolder, which can contain credentials for SSH. - The user’s keychains, which contain many credentials and can be unlocked if the user’s password can be obtained.
- The config file for SecureCRT, a terminal emulator program.
- The saved application state for iTerm2.
These files are all copied into ~/Library/Logs/tmp/, compressed into a file at ~/Library/Logs/tmp.zip, which is then uploaded to http://47.75.123[.]111/u.php?id=%s (where the %s is replaced with the machine’s serial number).
Thus, the primary goal of the g.py script seems to be to harvest credentials and other data that would be of use for lateral movement within an organization. Presumably, the backdoor provided by the GoogleUpdate process would be used to perform that lateral movement and infect other machines.
Additional trojanized apps
Subsequent findings revealed additional apps that had also been trojanized, using the same libcrypto.2.dylib file. These apps were:
- Microsoft Remote Desktop
- SecureCRT
- Navicat Premium (a database management app)
Who is affected?
At the moment, few people with Malwarebytes installed seem to be affected. We’ve only seen a detection on one computer so far, in Asia.
There are indications that this malware may be primarily distributed in China and other southeast Asian countries, where Malwarebytes has a relatively small install base. For readers outside that region, you probably don’t have much to fear.
However, out of an abundance of caution, if you have one of these apps, it would not be a bad idea to replace them with a known legitimate copy, being sure to get it from the official website of the developer rather than from a lookalike site or a download mirror.
You should also run a scan with Malwarebytes, which will detect this malware as OSX.ZuRu.
Samples
iTerm2.dmg e5126f74d430ff075d6f7edcae0c95b81a5e389bf47e4c742618a042f378a3fa com.microsoft.rdc.macos.dmg 5ca2fb207762e886dd3336cf1cb92c28f096a5fbb1798ea6721b7c94c1395259 Navicat15_cn.dmg 6df91af12c87874780cc9d49e700161e1ead71ae045954adbe7633ec9e5e45ff SecureCRT.dmg 1e462f8716275dbae6acb3ff4f7a95624c1afb23c5069fa42a14ed49c2588921
The post New Mac malware masquerades as iTerm2, Remote Desktop and other apps appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


