New Malspam Campaign Targets WinRAR ACE Flaw to Deliver Malware
Security researchers have discovered a new Malspam campaign exploiting the recently discovered WinRAR ACE flaw to install malware on the computer. Last week security researchers at Checkpoint disclosed a 19-year-old vulnerability in WinRARwhich can be exploited by attackers to execute malicious code on the targeted system.
The flaw was a result of an Absolute Path Traversal bug that resides in the library called UNACEV2.DLL.The UNACEV2.DLL is a third party library is responsible for extracting archives in the ACE file format.
The flaw can be exploited by the attackers to archives the files to a folder of their choice rather than the folder chosen by the user. The attacker could extract the file to Windows PC’s Startup folder where it would be automatically executed after the next reboot. The WinRAR development team lost access to UNACEV2.DLL library source code in 2005. To resolve the issue, the company released WinRAR 5.70 beta 1 that doesn’t support the ACE format. Now security researchers from 60 Threat Intelligence Center discovered an email distributing RAR archives which when extracted will infect the computer with a backdoor.
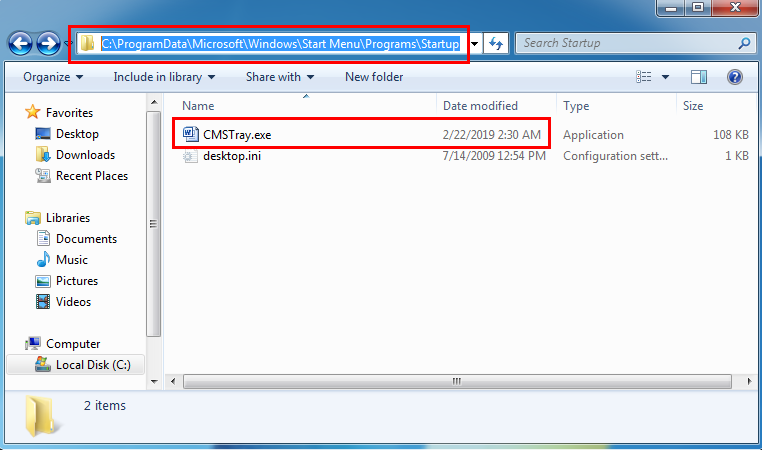
According to Bleepingcomputer, the malware leverages recently discovered ACE flaw in WinRAR. The backdoor is generated by MSF and attempts to extract the file into the user’s Startup folder. If UAC is running, the attack will fail because of the lack of permissions to extract it into the specific folder.
But if UAC is disabled or WinRAR is running with administrator privileges it will install the malware to the following folder: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\CMSTray.exe.
Once CMSTray.exe is extracted to the user’s Startup folder, on the next reboot the executable will be launched and will copy the CMSTray.exe to %Temp%\wbssrv.exe and execute the wbssrv.exe file.
According to bleeping computer the malware was also discovered connecting to hXXp://138[.]204[.]171[.]108/ and download addition tool such as Cobalt Strike Beacon DLL.
Users are advised to update their WinRAR to the latest version immediately.
source: securereading.com

![[NIGHTSPIRE] - Ransomware Victim: MFR CULTIVONS LES REUSSITES, France 2 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

