New malware variant has “radio silence” mode to evade detection

The Sharp Panda cyber-espionage hacking group is targeting high-profile government entities in Vietnam, Thailand, and Indonesia with a new version of the ‘Soul’ malware framework.
The particular malware was previously seen in espionage campaigns targeting critical Southeast Asian organizations, attributed to various Chinese APTs.
Check Point identified a new campaign using the malware that started in late 2022 and continues through 2023, employing spear-phishing attacks for initial compromise.
The use of the RoyalRoad RTF kit, C2 server addresses, and the hacker’s working hours allowed Check Point to attribute the latest espionage operation to state-backed Chinese hackers. The TTPs and tools are consistent with previously seen activities by Sharp Panda.
Infection chain
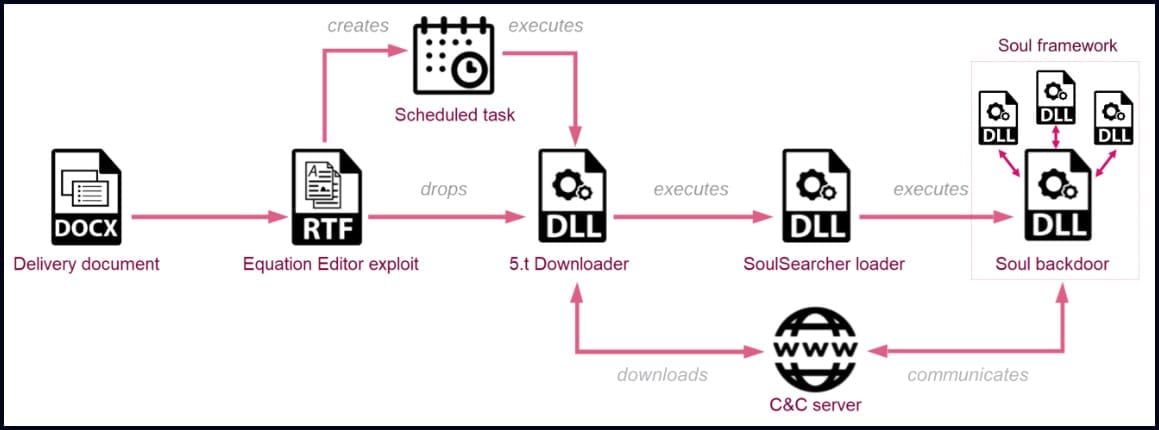
The new Sharp Panda campaign uses spear-phishing emails with malicious DOCX file attachments that deploy the RoyalRoad RTF kit to attempt to exploit older vulnerabilities to drop malware on the host.
In this case, the exploit creates a scheduled task and then drops and executes a DLL malware downloader, which in turn fetches and executes a second DLL from the C2 server, the SoulSearcher loader.
This second DLL creates a registry key with a value that contains the final compressed payload and then decrypts and loads the Soul modular backdoor into memory, helping it evade detection from antivirus tools running on the breached system.
Soul details
Upon execution, the main module of the Soul malware establishes a connection with the C2 and waits for additional modules that will extend its functionality.
The new version analyzed by Check Point features a “radio silence” mode which allows the threat actors to specify the specific hours of the week that the backdoor should not communicate with the command and control server, likely to evade detection during the victim’s working hours.
“This is an advanced OpSec feature that allows the actors to blend their communication flow into general traffic and decrease the chances of network communication being detected.” explained Check Point.
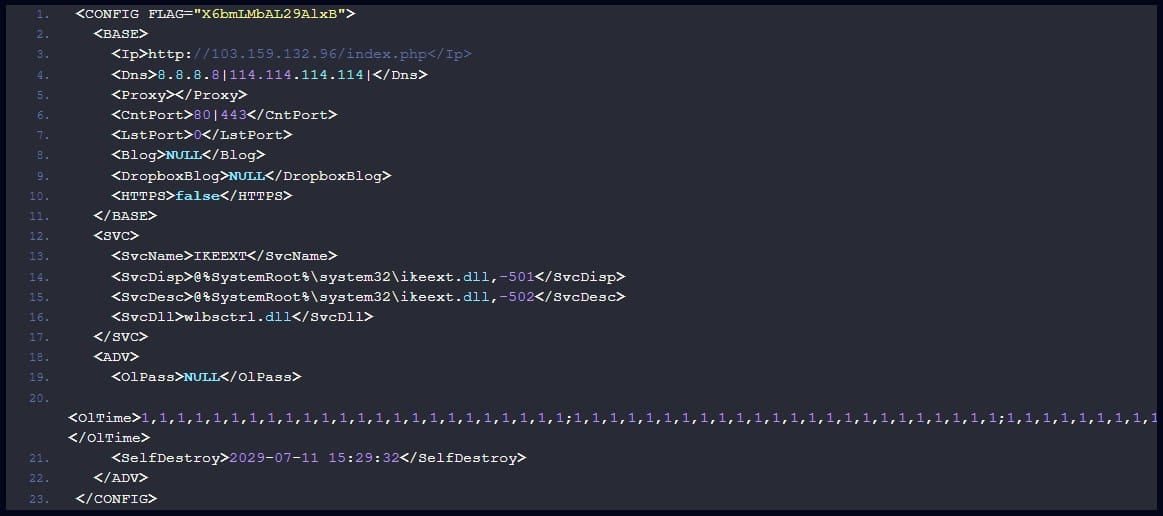
Moreover, the new variant implements a custom C2 communication protocol that uses various HTTP request methods, including GET, POST, and DELETE.
Support for multiple HTTP methods gives the malware flexibility, as GET is used for retrieving data, POST for submitting data.
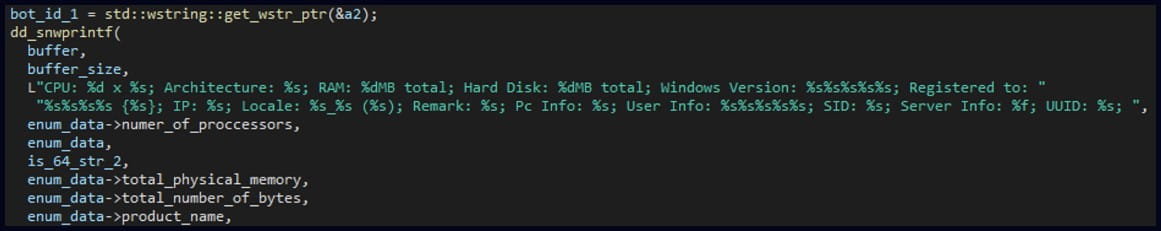
Soul’s communication with the C2 begins by registering itself and sending victim fingerprinting data (hardware details, OS type, time zone, IP address), after which it enters an infinite C2 contacting loop.
The commands it may receive during these communications concern loading additional modules, collecting and resending enumeration data, restarting the C2 communication, or exiting its process.
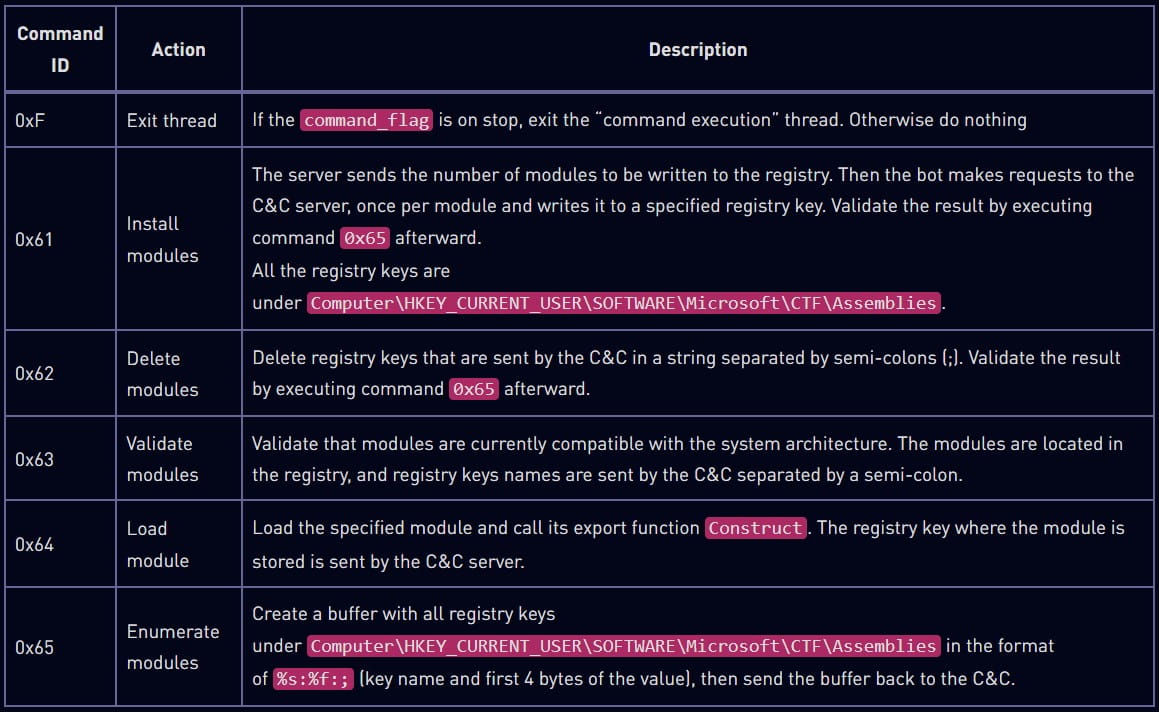
Check Point did not sample additional modules that might perform more specialized functions such as file actions, data exfiltration, keylogging, screenshot capturing, etc.
The Soul framework was first seen in the wild in 2017 and subsequently tracked throughout 2019 in Chinese espionage campaigns conducted by threat actors with no obvious links to Sharp Panda.
Despite the overlaps in the use of the tool, Check Point’s recent findings show that Soul is still under active development and deployment.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.





![[QILIN] - Ransomware Victim: Omrin 12 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
