Newly exposed APT43 hacking group targeting US orgs since 2018

A new North Korean hacking group has been revealed to be targeting government organizations, academics, and think tanks in the United States, Europe, Japan, and South Korea for the past five years.
The moderately-sophisticated threat actor is tracked as ‘APT43’ and is seen engaging in espionage and financially-motivated cybercrime operations that help fund its activities.
Mandiant analysts who disclosed the activities of APT43 for the first time assess with high confidence that the threat actors are state-sponsored, aligning their operational goals with the North Korean government’s geopolitical aims.
“More specifically, Mandiant assesses with moderate confidence that APT43 is attributable to the North Korean Reconnaissance General Bureau (RGB), the country’s primary foreign intelligence service,” explains the new report by Mandiant.
The researchers have been tracking APT43 since late 2018 but have disclosed more specific details about the threat group only now.
APT43 espionage
APT43 has been observed shifting focus on its espionage operations abruptly, which is a sign they receive orders on their targets, following the directions of broader strategic planning.
Over the years, it has targeted government offices, diplomatic organizations, think tank entities, universities employing professors specializing in Korean peninsula matters, and other critical organizations in South Korea, the United States, Europe, and Japan.
APT43 uses spear-phishing emails from fake or spoofed personas to approach their targets, sending them to websites impersonating legitimating entities. However, these websites contain phony login pages where victims are tricked into entering their account credentials.
Having stolen these credentials, APT43 logs in as the target to carry out the intelligence collection themselves. They also use the victim’s contacts to further their phishing activities to other marks.
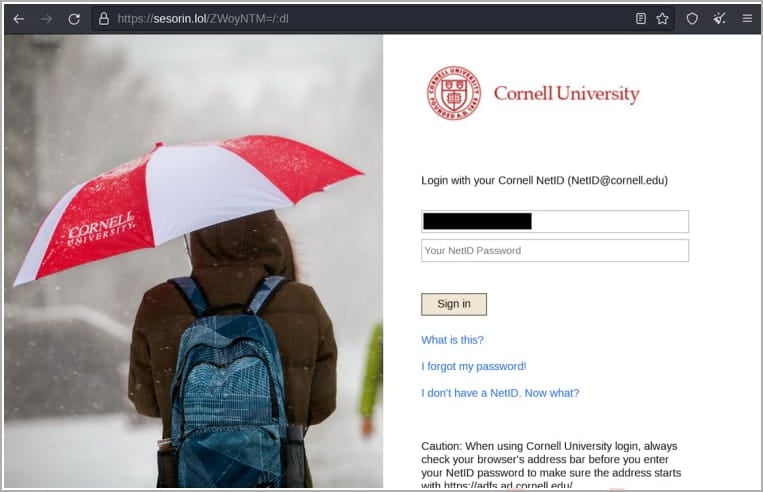
“The group is primarily interested in information developed and stored within the U.S. military and government, defense industrial base (DIB), and research and security policies developed by U.S.-based academia and think tanks focused on nuclear security policy and nonproliferation,” explains the Mandiant report.
“APT43 has displayed interest in similar industries within South Korea, specifically non-profit organizations and universities that focus on global and regional policies, as well as businesses, such as manufacturing, that can provide information around goods whose export to North Korea has been restricted.”
Examples of such goods include weapons, transportation vehicles, machinery, fuel, and metals.
Funding its own operations
APT43 employs a strategy akin to most North Korean threat groups that operate independently of state funding. Instead, they are expected to sustain their activities through financially-driven cyber operations.
Mandiant has observed APT43 using malicious Android apps that target Chinese users looking to get cryptocurrency loans and instead lose their digital assets to the threat actors.
The cryptocurrency stolen by APT43 is laundered through hash rental and cloud mining services using many aliases, addresses, and payment methods.
Hash rental allowers customers to rent computational power for cryptocurrency mining, which can be paid for in crypto. Mandiant says that APT43 uses these services to launder stolen cryptocurrency so that it cannot be traced back to malicious operations.
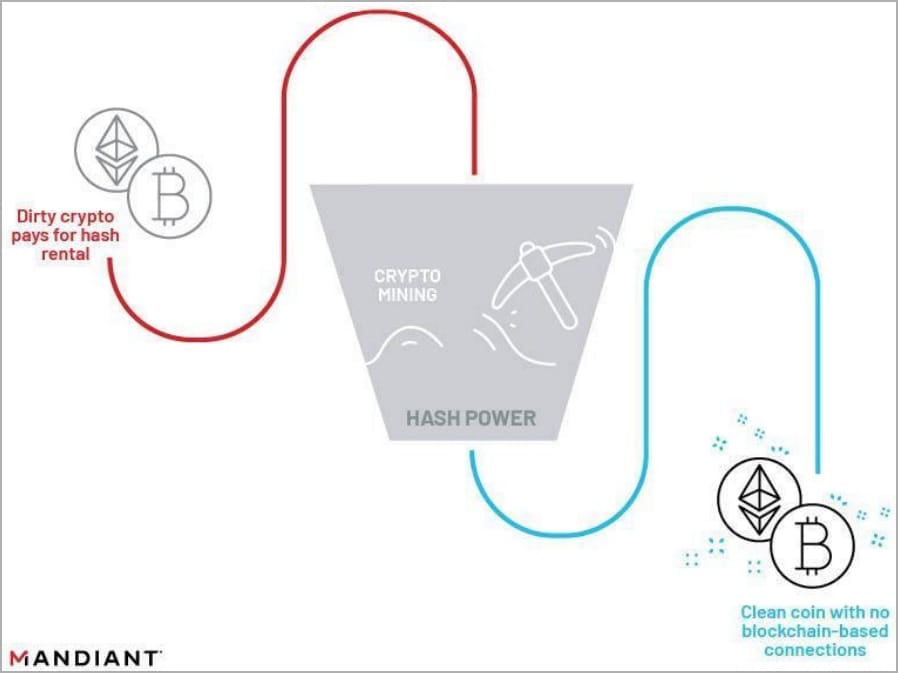
Mandiant reports seeing the group paying for hardware and infrastructure with PayPal, American Express cards, and Bitcoin, likely all stolen from victims.
Malware and Korean overlaps
Mandiant reports that other researchers in the past have spotted APT43 activity, but it was typically attributed to Kimsuky or Thalium.
Also, APT43 has been seen utilizing malware during the COVID-19 pandemic that the Lazarus hacking group also uses, but this overlap was short-lived.
In another instance, the threat group used the “Lonejogger” crypto-stealing tool that has been associated with the UNC1069 threat actor, likely to be connected to APT38.
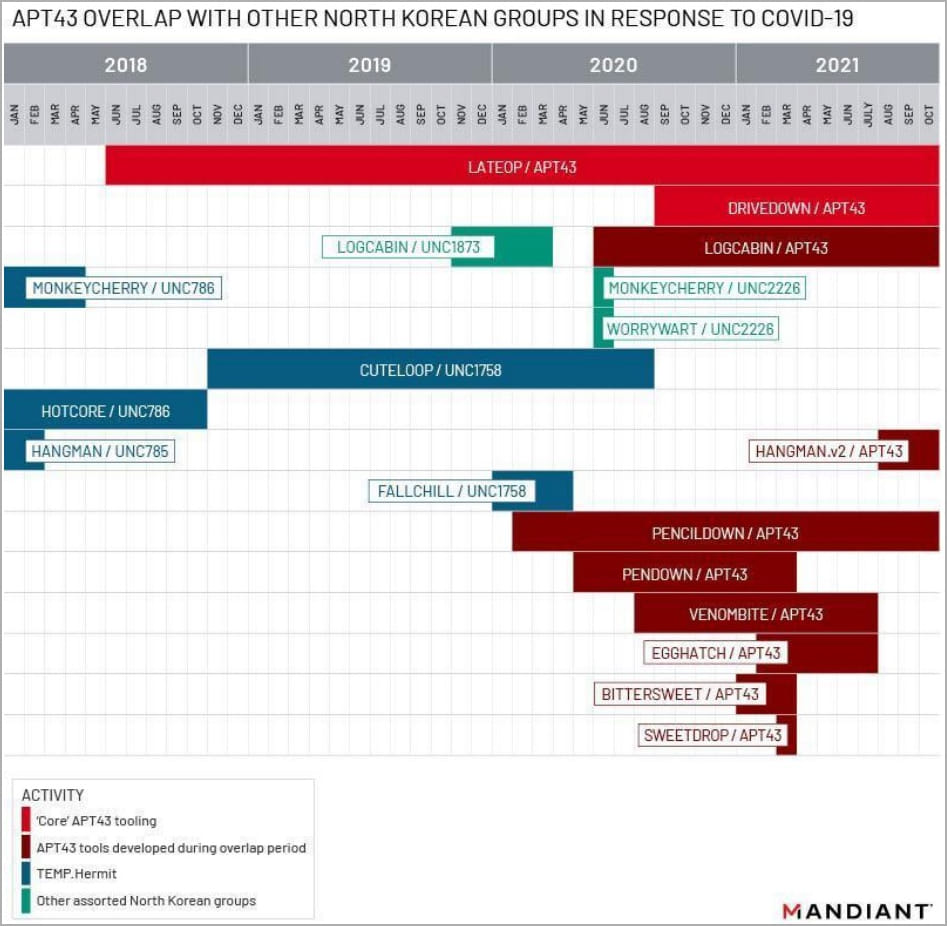
APT43 also has its own set of custom malware not employed by other threat actors, like the “Pencildown,” “Pendown,” “Venombite,” and “Egghatch” downloaders, the “Logcabin” and “Lateop” (“BabyShark”) tools, and the “Hangman” backdoor.
Apart from those, the threat group has also deployed publicly available tools like “gh0st RAT,” “QuasarRAT,” and “Amadey.”
Mandiant expects APT43 to continue to be a highly active threat group unless North Korea shifts national priorities.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.





