NICER Protocol Deep Dive: Internet Exposure of FTP/S (TCP/990)

Welcome to the NICER Protocol Deep Dive blog series! When we started researching what all was out on the internet way back in January, we had no idea we’d end up with a hefty, 137-page tome of a research report. The sheer length of such a thing might put off folks who might otherwise learn a thing or two about the nature of internet exposure, so we figured, why not break up all the protocol studies into their own reports?
So, here we are! What follows is taken directly from our National / Industry / Cloud Exposure Report (NICER), so if you don’t want to wait around for the next installment, you can cheat and read ahead!
[Research] Read the full NICER report today
Get Started
FTP/S (TCP/990)

TLDR
WHAT IT IS: FTP, but with an SSL wrapper, much like HTTPS is merely HTTP with an SSL layer.
HOW MANY: 459,907 discovered nodes. 84,607 (18%) have Recog fingerprints (10 total service families).
VULNERABILITIES: Mostly DoS vulnerabilities in the discovered, fingerprinted versions, but a few have auth/unauth RCE. We will discuss IIS in a future post.
ADVICE: Use SFTP instead, since FTP/S only encrypts authentication, leaving your file transfers in cleartext.
ALTERNATIVES: SFTP, SCP, SSH-wrapped rsync, or HTTPS-based file sharing applications
GETTING: Stuck, like its FTP cousin.
Discovery details
FTP/S (the TCP/990 variant) dates back to 1997 and was intended to resolve the outstanding security issues with the FTP protocol. It is, in essence, a somewhat more secure version of FTP. Unfortunately, it only makes logins safer, as file transfers are still performed in cleartext and without any sort of protection from eavesdropping or modification in transit. One other benefit is that FTP/S servers can assert their identities with cryptographic certainty—much like how HTTPS servers can—but this assertion relies on clients actually checking the certificate details and doing the right thing when certificate identification fails.
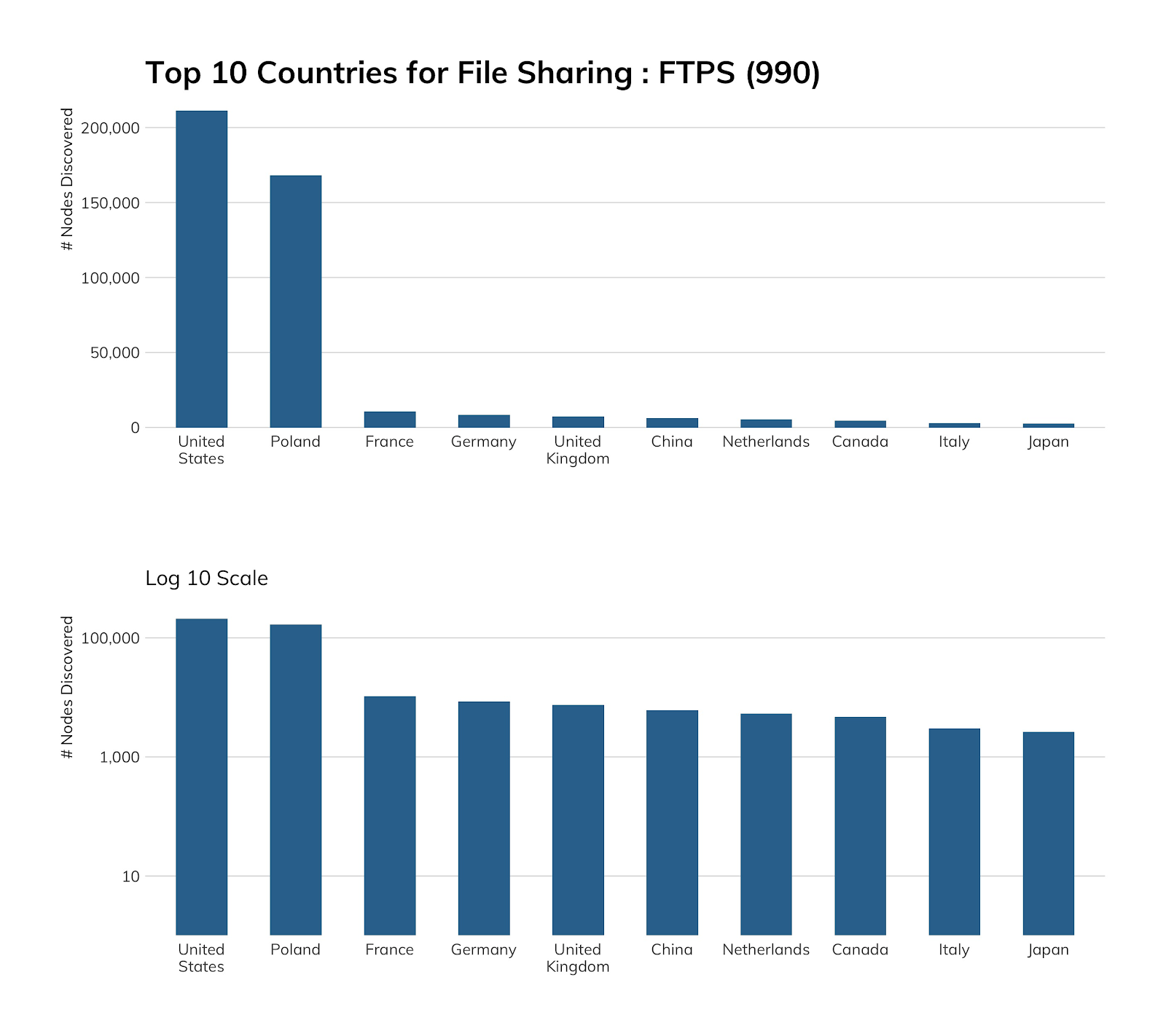
Given that FTP/S is almost exactly like its insecure cousin but safer to use, you’d think there would be widespread adoption of it. Alas, you would be wrong. Project Sonar barely found half a million nodes on the public internet compared to millions of plain ol’ FTP servers. A possible big reason for this is the need to generate, install, and periodically update TLS certificates, a process for FTP/S that is not as simple as it is these days for HTTPS.
There are high concentrations of FTP/S in the U.S. (mostly due to heavy prevalence in Azure, which we’ll cover in a bit), but also in Poland due to the home.pl hosting provider, which goes out of its way to get you to use it over vanilla FTP—a laudable documentation effort we would love to see other cloud providers strive toward.
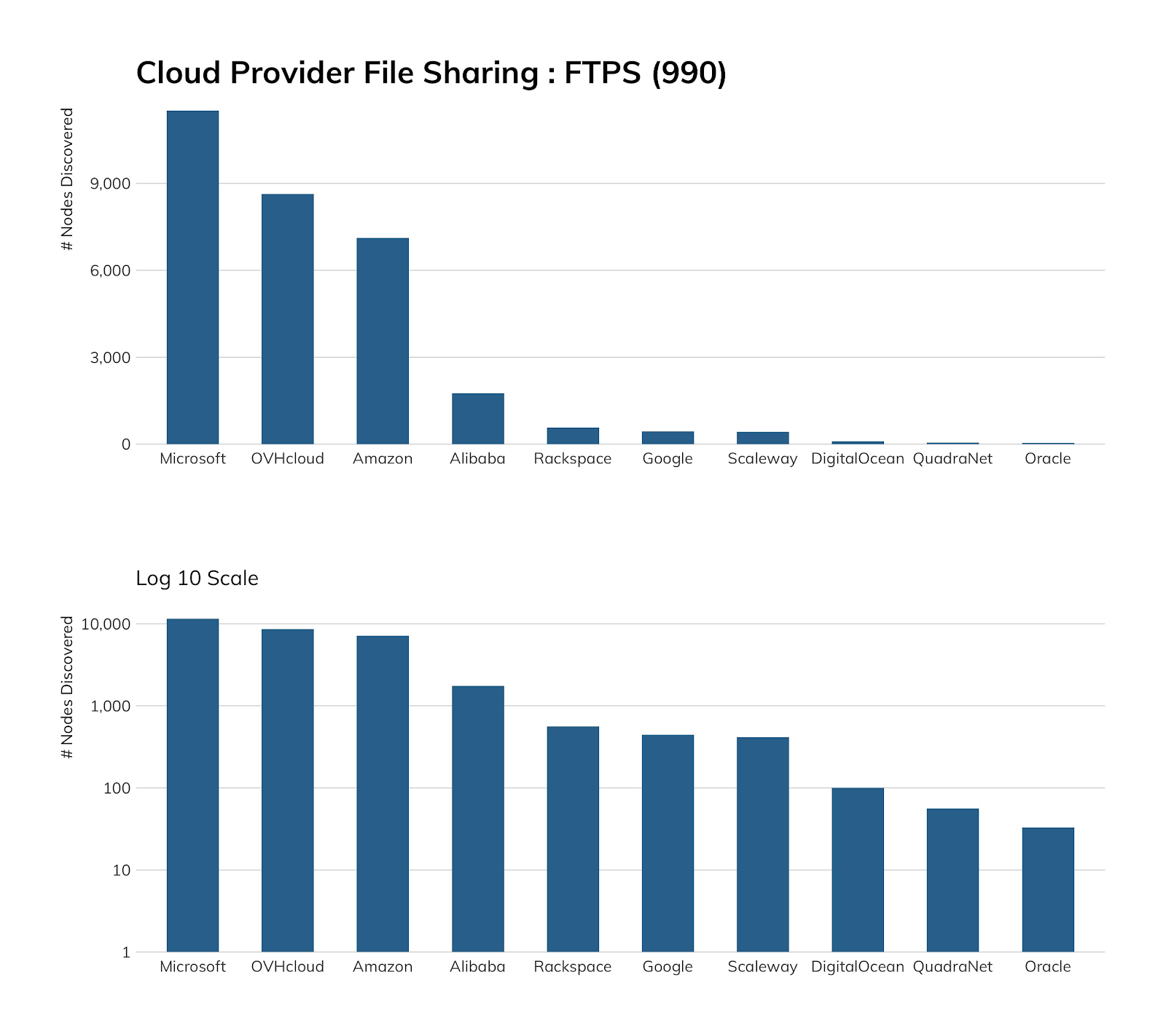
Unfortunately, home.pl didn’t expose sufficient nodes to make it into the top 10 cloud providers we used across all studies in this report, but they’re doing the right thing, as is Microsoft. Along with the aforementioned FTP documentation, they also have dedicated FTP/S setup and use instructions, and it’s fairly trivial to enable FTP/S in IIS, as the table in the Exposure section hints at.
For all this effort, though, users are likely using SCP instead of FTP/S, since SCP does, in fact, encrypt the contents of files in transit as well as login credentials.
Exposure information
Recog was only able to fingerprint 84,607 (18%) of the available FTP/S services, but IIS “wins” this time, as there are explicit configuration parameters available for FTP/S and there is a GUI for requesting and installing certificates.
| Service | Count |
|---|---|
| IIS | 38,314 |
| FileZilla FTP | 33,147 |
| Serv-U | 7,092 |
| ProFTPD | 1,697 |
| vsFTPd | 1,420 |
| Pure-FTPd | 1,184 |
| WS_FTP | 1,110 |
| Gene6 | 623 |
| Bftpd | 19 |
| Twisted | 1 |
Since many FTP/S servers are both FTP and FTP/S servers, the same vulnerabilities apply. We’ll be giving IIS a full workout in a future post.
Attacker’s view
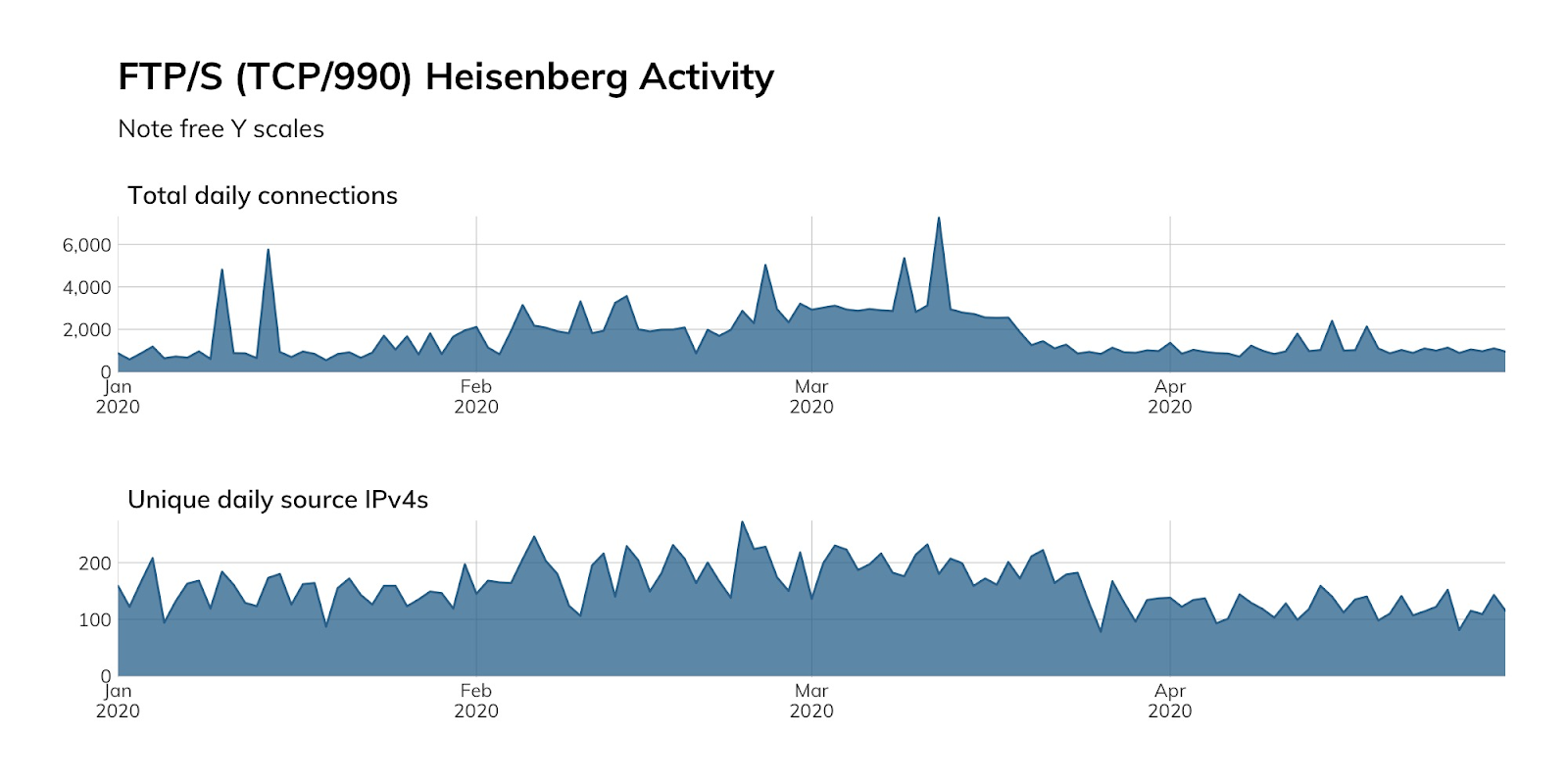
FTP/S is not used much, and that’s generally a sign it’s not going to get much love from either attackers or researchers, a posit that our Project Heisenberg activity reinforces (like FTP, we do not have a high-interaction honeypot for FTP/S, so raw total and unique time series counts are used as a proxy for attacker and researcher activity):
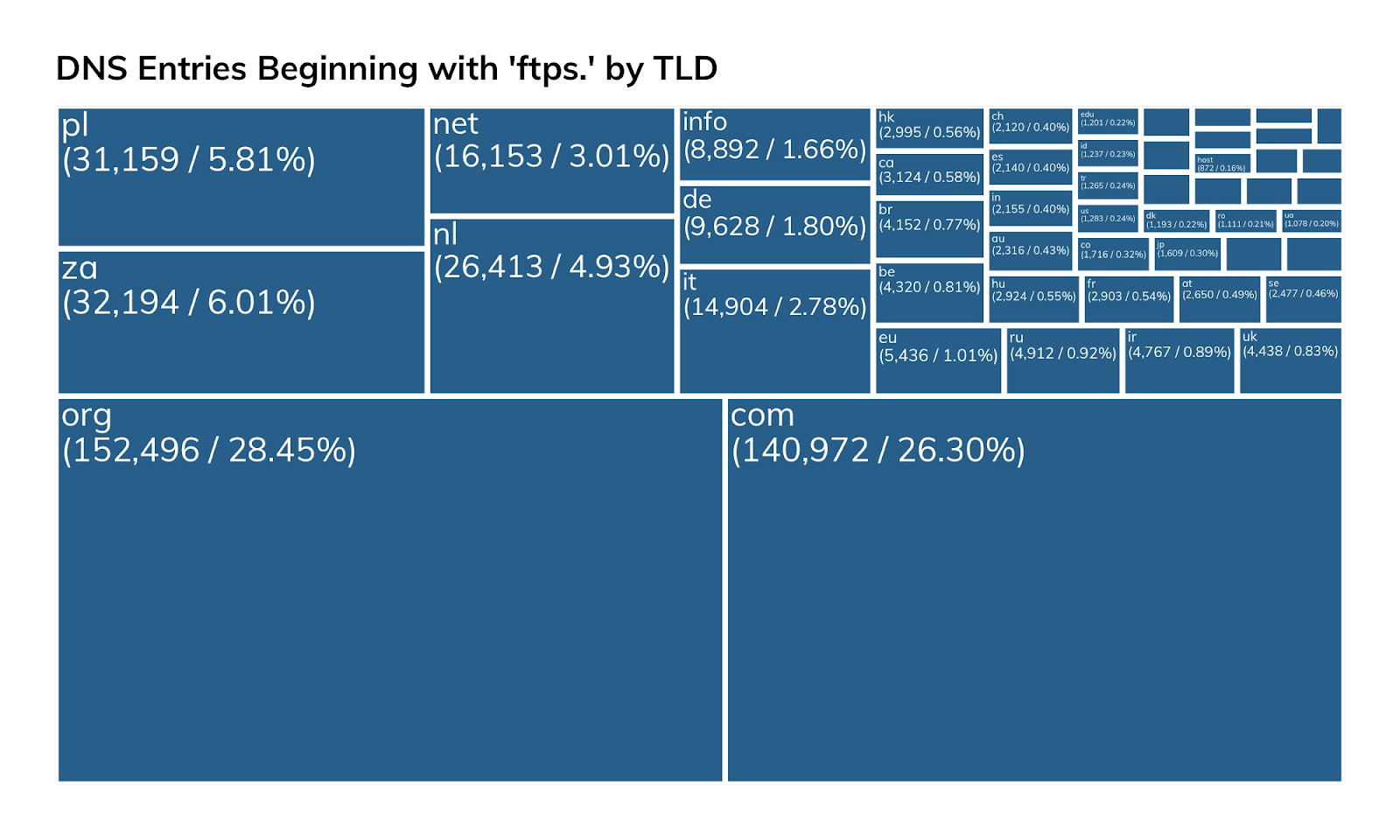
Besides exposing FTP/S on the default port, attackers will also have no trouble finding these systems by DNS entries, given just how many entries there are for ftps.….tld in public DNS:
Our advice
IT and IT security teams should follow the advice given in the FTP section, since most of it still applies. If you are always sending pre-encrypted files or the content you are uploading/downloading is not sensitive (and, you’re not worried about person-in-the-middle snooping or alteration), you may be able to get away with using FTP/S a bit longer.
Cloud providers should follow home.pl’s example and be explicit about what FTP/S can and cannot do for file transfer safety. While there may be some systems that are reliant on FTP/S, cloud providers should be actively promoting total solutions, like SCP and rsync, over SSH.
Government cybersecurity agencies should provide guidance on what FTP/S can and cannot do for file transfer safety and provide suggestions for alternative services. As noted in our FTP blog post (which applies also to FTP/S), there are unauthenticated RCE vulnerabilities in this small-ish population of internet-facing FTP/S systems, making them available targets for attackers and an inherent weakness in public infrastructure of each country with exposed FTP/S services.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



![[EVEREST] - Ransomware Victim: MUSE-INSECURE: Inside Collins Aerospaces Security Failure 9 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
![Cobalt Strike Beacon Detected - 47[.]109[.]90[.]134:88 11 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
