OilRig’s Poison Frog – old samples, same trick

After we wrote our private report on the OilRig leak, we decided to scan our archives with our YARA rule, to hunt for new and older samples. Aside from finding some new samples, we believe we also succeeded in finding some of the first Poison Frog samples.
Poison Frog
We’re not quite sure whether the name Poison Frog is the name given to the backdoor by the malware authors, or by the leakers. The fact is though, that one of the earliest Poison Frog samples we could find uses ‘poison-frog[.]club’ as the domain name for its C2.
But before we go there, let’s first take a look at a sample (MD5 4EA656D10BE1D6EAC05D69252D270592). This is a PE32 executable, written in C#. The C# code is not that interesting; its only functionality is to drop the PowerShell script (which contains the backdoors and is embedded within the executable), execute it and delete it afterwards. The same functionality (with occasional variations in the implementation) appears in all the PE32 samples we found.
The embedded PowerShell script follows the same logic as all the dropper PowerShell scripts we found. There are two long strings called dns_ag and http_ag (although the former is an empty string in this sample) that contain the DNS and HTTP backdoor (base64 encoded). As always, persistence is achieved by using the task scheduler utility.
After base64 decoding the DNS agent, and converting it from UTF16 to ASCII, we end up with the first version of the Poison Frog HTTP backdoor: a 59-line PowerShell backdoor. As you would expect from a 59-line backdoor written in PowerShell, its functionality is limited and its operation is rather simple.
First, it starts by calculating a UID based on the MAC address or the output of whoami. Then it sends the UID, surrounded by random numbers and/or encapsulated within the string 24351243510. Then, if a reply 11 characters long is received, the reply is sent back to the C2 followed by or prepended with a ‘1’. This reply is saved in a variable because it is used to determine what functionality is called by the C2. But first, the initial reply is sent back – this time followed by or prepended with a ‘3’.
Now, depending on the last character of the saved reply, the following actions take place:
If the last character is a ‘0’, the command specified in the reply is executed on the machine and the result is sent back to the C2;
If the last character is a ‘1’, the agent checks if the file specified in the reply exists on the system. If it doesn’t, a 404 is sent back; if it does, the file is sent to the server;
If a ‘2’ is received, the file is saved on the system at the location specified in the reply.
And that’s it. All in 59 lines.
Another sample we found is MD5 C9F16F0BE8C77F0170B9B6CE876ED7FB. It embeds one of the earliest versions of the DNS agent. In 335 lines of code it is able to execute commands on the system as well as save files to the system.
Poison Frog disguises
Installing malware on a system is not always easy. So the OilRig developers decided to pull a little trick and disguise the malware as the legitimate Cisco AnyConnect application. The backdoor is embedded in a similar way to that used in the samples above.
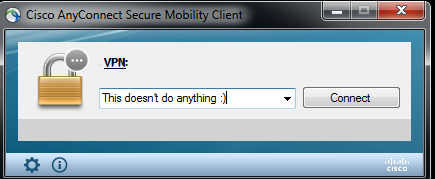
They made some small implementation mistakes, however. For example, the info popup appears every time you click on it, which doesn’t happen with the benign application.
The following message also helped fool users – it appeared when the connect button was clicked:
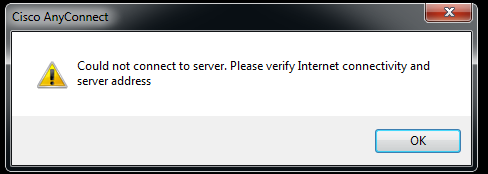
This may lead users to think there is something wrong with the application or their internet access, though in reality the backdoor is being silently installed on the system.
OilRig’s sloppiness
OilRig is not the most advanced APT actor, with several small mistakes made during the course of its activities.
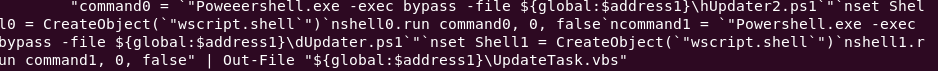
For example, one sample failed to execute properly because of a typo (note the ‘Poweeershell.exe’ instead of ‘Powershell.exe’):
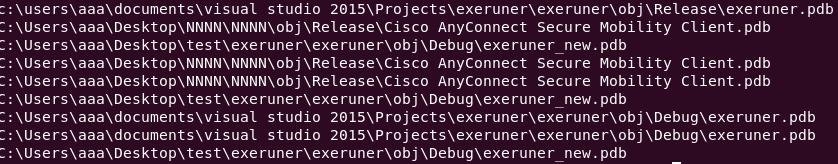
Also, many samples still had the PDB path inside the binary:
With other samples, they changed the compilation date to a future date – one that was after its release. For instance, one sample – 87FB0C1E0DE46177390DE3EE18608B21 – has a compilation date of 2018-07-25, though we found it on our systems a year earlier.
For more details and the latest information on OilRig, please contact [email protected]


