OpenSMTPD Vulnerability (CVE-2020-8794) Can Lead to Root Privilege Escalation and Remote Code Execution

By Alexander Elkholy (Threats Analyst)
A root privilege escalation and remote execution vulnerability (designated as CVE-2020-8794) has been discovered in the free and open-source Unix Daemon, OpenSMTPD. The flaw originates from an out-of-bounds read, which attackers can take advantage of to execute arbitrary code on vulnerable systems.
What is the vulnerability about?
Discovered by Qualys Research Labs and disclosed on February 24, 2020, the vulnerability affects all versions of OpenSMTPD prior to 6.6.4. Part of the OpenBSD project, OpenSMTPD facilitates email communications to allow the retrieval and delivery of mail, and implements the Simple Mail Transfer Protocol (SMTP) protocol.
This is the third OpenSMTPD vulnerability found in the last month, with the previous two being a remote code execution vulnerability (CVE-2020-7247) that allows attackers to execute arbitrary commands as root through a specially crafted SMTP session and a vulnerability (CVE-2020-8793) that allows local users to potentially read arbitrary system files.
This vulnerability (CVE-2020-8794) is especially notable since it affects default installations of OpenSMTPD and the most current release of OpenBSD (version 6.6 at the time of writing) ships with a vulnerable version.
CVE-2020-8794, originally introduced to OpenSMTPD in version 5.7.1 and included in OpenBSD as of December 2015, allowed attackers to run commands as any non-root user. The effect of the flaw worsened after OpenSMTPD switched to a new message grammar in May 2018, where it allowed attackers to run commands as root.
How can the vulnerability be exploited?
The location of the vulnerability is in mta_session.c, specifically, in the mta_io function that is responsible for parsing multiline replies from an SMTP server. The out-of-bounds error occurs when the last line of the reply does not follow the standard format of three-digit code/space/text (e.g., instead of “250 DATA”, we pass “250”).
When this occurs, the pointer the program uses to read the string ends up pointing to a location that is found after the ‘�’ null terminator. As a result, the program incorrectly reads it and appends the following lines to the buffer as well.
If the response message is an error, the contents (including the additional lines) are saved internally to an envelope that describes the mail behavior. Since newline characters can be included in the additional lines, an attacker can modify this internal file and thus modify the behavior of OpenSMTPD.
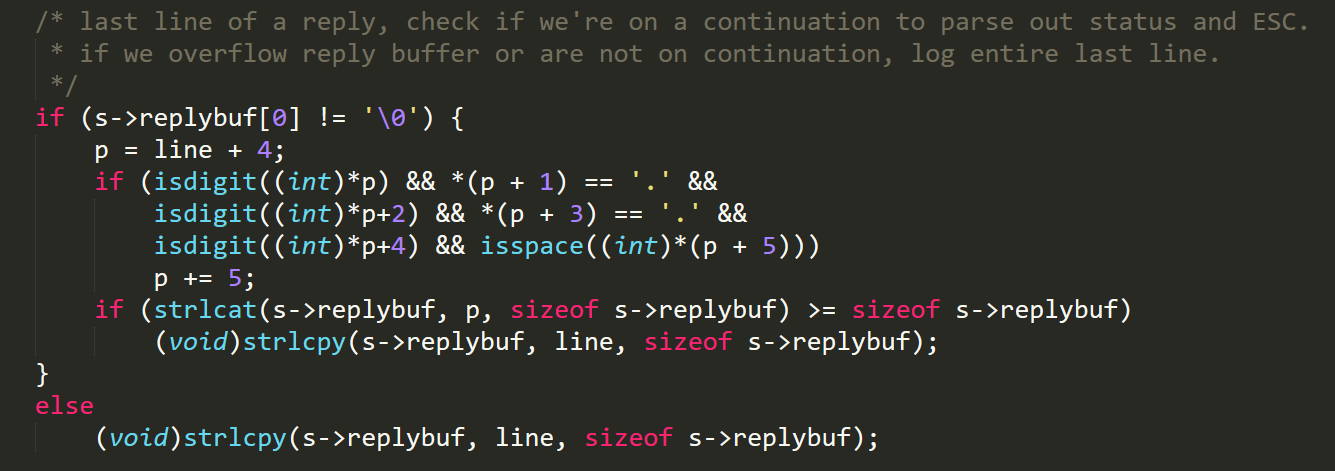
Figure 1. Vulnerable code inside mta_io function: If the final line of a reply is in an incorrect format, all the remaining content is also appended to the replybuf since p points to a location after the null byte
The vulnerability is located in the client-side portion of the code instead of the server-side, so some work needs to be done to exploit it since the client typically listens on localhost only. There are two methods that can be used to exploit the vulnerability: client-side and server-side.
Client-side exploitation is the simpler method. Essentially, if the client machine sends a mail message to a compromised mail server, the server can respond using a specially crafted response that causes the out-of-bounds read error to occur. It then injects the following lines into the mail envelope:
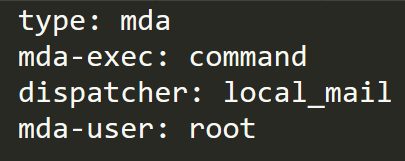
Figure 2. Lines injected into the mail envelope, where the command is an arbitrary one that the attacker wants to execute
Since the message type has been changed to MDA (Message Delivery Agent), OpenSMTPD executes the command when the message fails to deliver, giving the attacker the ability to run arbitrary code on the vulnerable machine.
The server-side exploitation method is more complicated. This method involves sending a message to the SMTP server that bounces back to the compromised mail server. The compromised server responds to the bounce with a temporary error, then forces the server to crash by repeating the bounce with one that has a fatal error.
After the server restarts, it will execute the command stored in the message with a temporary error.
Note that a permanent error cannot be sent at the start since the server automatically discards double bounces and thus would not execute the command. Furthermore, the server must be restarted before the command is executed because, even though the message type has been changed in the envelope, it is still stored in the queue corresponding to its old type. After a reset, everything is re-checked and the message is moved to the MDA queue for execution.
The older versions (prior to May 2018) have a very similar exploitation method — the main differences are the response mail message, which has a slightly different format, and the fact that only non-root users are allowed.
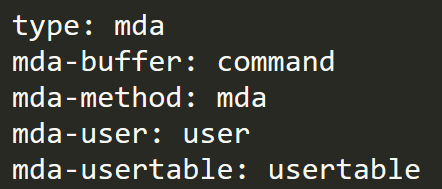
Figure 3. Lines injected to envelope for older versions
The vulnerability has been patched in version 6.6.4, and the patch works by adding an additional check on the length of the final message line being greater than 4. This way, the pointer p is no longer able to point beyond the null character; as a result, it will no longer read the out-of-bounds content.
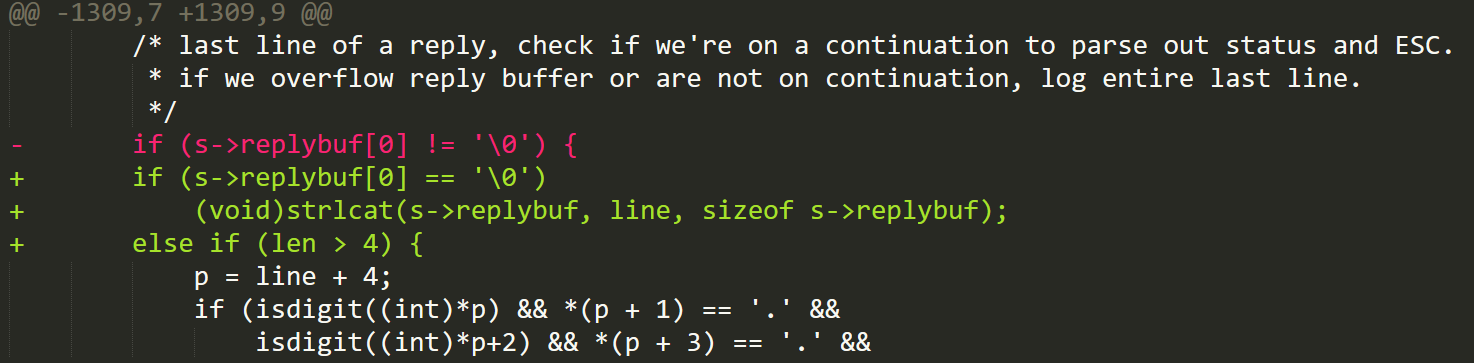
Figure 4. The mta_io function patch closes the out-of-bounds read by checking if the length of the string is at least 4 before collecting the message
What can be done to protect against the vulnerability?
OpenSMTPD users can protect systems from threats targeting CVE-2020-8794 by updating installations below version 6.6.4, especially if they are using a version released after May 2018. It should be noted that even if a server is using an older version that does not allow the attacker to execute commands as root, there are still significant risks since an attacker could still run many malicious commands. It is also possible for the attacker to elevate their privilege if combined with other exploits.
System administrators and IT/security teams, in addition, should always adopt best practices and mitigations such as:
- Adding layers of security mechanisms such as virtual patching, which pre-empts exploitation of known, unknown, and undisclosed vulnerabilities
- Enforcing the principle of least privilege and disabling or deleting outdated or unused components
- Proactively monitoring, detecting, and blocking malicious traffic through intrusion prevention systems
The Trend Micro Deep Security
Deep Security and Vulnerability Protection solutions also protect systems and users from threats that exploit CVE-2020-8794 via the following rule:
and Vulnerability Protection solutions also protect systems and users from threats that exploit CVE-2020-8794 via the following rule:
- 1010190 – OpenBSD OpenSMTPD ‘mta_io’ Out Of Bounds Read Vulnerability (CVE-2020-8794)
Trend Micro TippingPoint® customers are protected from threats and attacks that may exploit CVE-2020-8794 via the following MainlineDV filter:
TippingPoint® customers are protected from threats and attacks that may exploit CVE-2020-8794 via the following MainlineDV filter:
- 37303: SMTP: OpenBSD OpenSMTPD mta_io Out-of-Bounds Read Vulnerability
Trend Micro Deep Discovery Inspector users are protected from this threat via this rule, which covers the network traffic:
Deep Discovery Inspector users are protected from this threat via this rule, which covers the network traffic:
- Rule 4355: CVE-2020-8794 – OPENSMTPD RCE EXPLOIT – SMTP (RESPONSE)
The post OpenSMTPD Vulnerability (CVE-2020-8794) Can Lead to Root Privilege Escalation and Remote Code Execution appeared first on .

![[QILIN] - Ransomware Victim: Doha British School 10 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

