Optimizing Security in the Work-From-Home Era
To make matters worse, attackers are also capitalizing on fears and concerns associated with the global pandemic.
In early April, Google saw 18 million daily malware and phishing emails related to COVID-19 in addition to more than 240 million COVID-related daily spam messages.
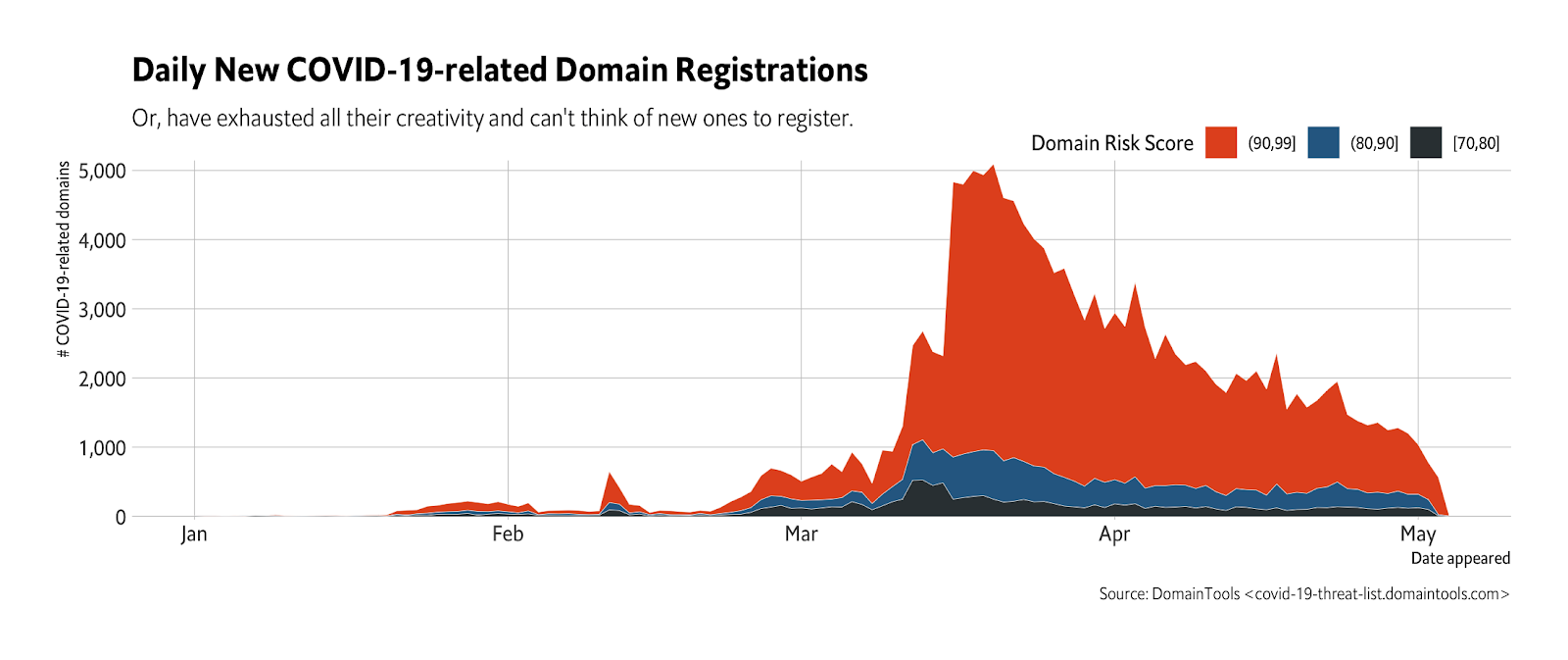
DomainTools has also set up a special tracking site and is releasing daily updates to a database of COVID-related domains (paired with risk scores) in an effort to help defenders mitigate against phishing and other types of cyber-attacks. While the pace of new, malicious domain creations has slowed (below), there are over 153,000 able to be used.
Automation is critical in the work-from-home era
Since it is difficult (impossible, really) to prevent novel phishing campaigns from reaching an organization’s workforce, speedy detection, response, and containment is of the essence.
With that in mind, Rapid7 is providing:
- Free access to InsightConnect
- Automation playbooks for remote security teams
- Best practices and assistance on how to get started with automation
- A community forum to provide feedback and collaborate on new automation tasks
A major component of this initial release is our “Phishing Tackle Box,” which provides a set of automated workflows and prebuilt integrations with email systems, Slack, and Microsoft Teams to optimize response times, tasks, and collaboration when an organization has been targeted by a phishing attack.
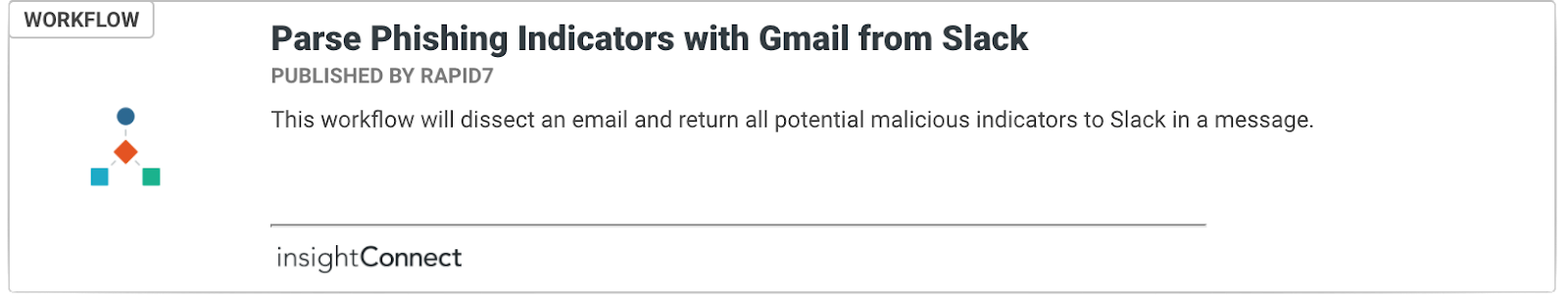
Pre-built InsightConnect workflows digest all indicators (domains, URLs, IP addresses, etc.) from incoming mail and check them against public and organization-accessible threat indicator lists and APIs.
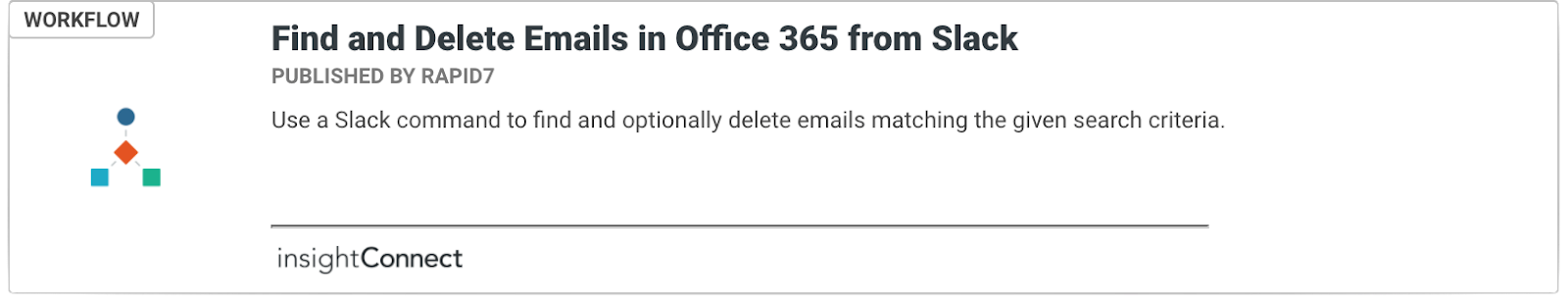
When IoCs associated with malicious campaigns are identified, many actions can take place automatically, whether it be notifying automation-shy security teams in their collaboration platform of choice or automatically configuring systems to reject new emails from certain senders and domains, delete existing ones, and identify accounts that may have opened them and/or been compromised.
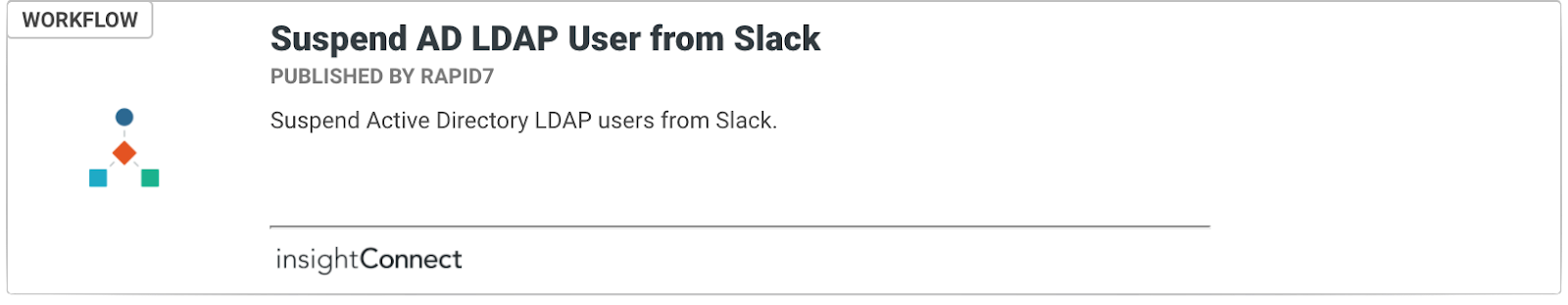
Provided proper processes have been developed and workers are aware of them, complete user containment can be automated if a compromise has been detected, with containment steps ranging from simple password resets to temporary removal of access to critical systems, network, and data.
The Work-from-Home Automation Playbooks are designed to help optimize your response, containment, and remediation times, whether you start with a Slack- or Teams-based workflow or migrate to full automatic actions as you become more comfortable and experienced with automation.
Get Started With Our Work-From-Home Automation Playbooks
Learn More

![[RHYSIDA] - Ransomware Victim: GEIGER 5 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)


