Pathprober – Probe And Discover HTTP Pathname Using Brute-Force Methodology And Filtered By Specific Word Or 2 Words At Once
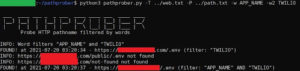
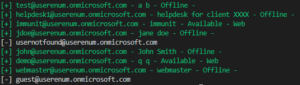
Probe and discover HTTP pathname using brute-force methodology and filtered by specific word or 2 words at once. PurposeBrute-forcing website...