PAKURI – Penetration Test Achieve Knowledge Unite Rapid Interface

What’s PAKURI
In Japanese, imitating is called “Pakuru”.
ぱくる (godan conjugation, hiragana and katakana パクる, rōmaji pakuru)
- eat with a wide open mouth
- steal when one isn’t looking, snatch, swipe
- copy someone’s idea or design
- nab, be caught by the police
Wiktionary:ぱくる
Description
Pentesters love to move their hands. However, I do not like troublesome work. Simple work is performed semi-automatically with simple operations. PAKURI executes commands frequently used in penetration tests by simply operating the numeric keypad. You can test penetration as if you were playing a fighting game.
Presentation
- November 2nd,2019: AV TOKYO 2018 Hive
Abilities of “PAKURI”.
- Intelligence gathering.
- Vulnerability analysis.
- Visualize.
- Brute Force Attack.
- Exploitation.
Your benefits.
By using our PAKURI, you will benefit from the following.
For redteam:
(a) This saves you the trouble of entering frequently used commands.
(b) Beginner pentester can learn the floe of attacks using PAKURI.
For blueteam:
(c) Attack packets can be generated with a simple operation.
NOTE
If you are interested, please use them in an environment under your control and at your own risk. And, if you execute the PAKURI on systems that are not under your control, it may be considered an attack and you may have legally liabillity for your action.
Features
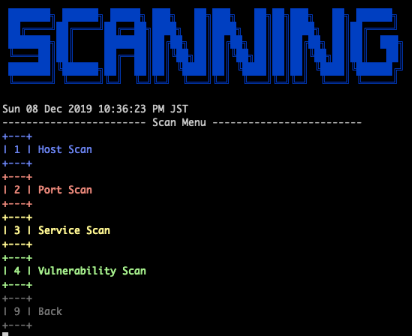
- Scan
- Nmap
- AutoRecon
- OpenVAS
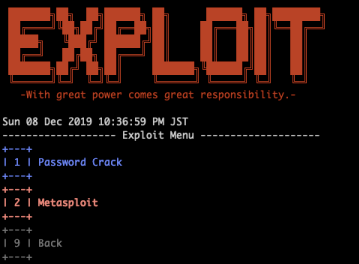
- Exploit
- BruteSpray
- Metasploit
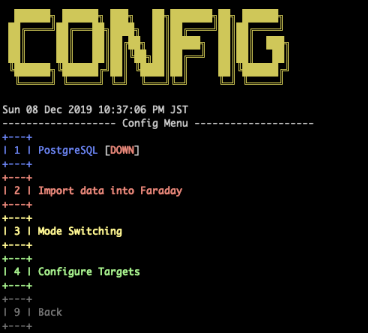
- Visualize
- Faraday
- CUI-GUI switching
Installbash install.sh
Usageroot@kali:/usr/share/pakuri# ./pakuri.sh
Main
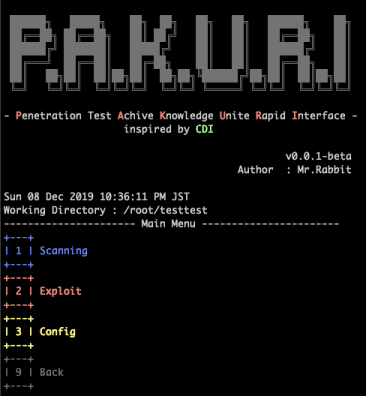
Scanning
Exploit
Config
Command
Operation check environment
- OS: KAli Linux 2019.4
- Memory: 8.0GB
This tool is not yet complete. It will be updated sequentially.

