Patch now to bypass Firefox add-ons that abuse the proxy API to deny updates
In a Firefox security announcement, Mozilla said 455,000 users have downloaded Firefox add-ons that interfere with how they connect to the internet.
The interference in itself was not the deciding factor, however. The add-ons abused the proxy API to prevent users who had installed them from downloading updates, accessing updated blocklists, and updating remotely configured content.
What is the proxy API?
The proxy API can be used by add-on developers as an event listener to intercept web requests, and return an object that describes whether and how to proxy them. Add-ons that use the proxy API need the “proxy” permission. And where they want to intercept requests, they also need “host” permission for the URLs of intercepted requests.
Google Chrome provides an extension API also called “proxy” which is functionally similar to this API, in that extensions can use it to implement a proxying policy. However, the design of the Chrome API is completely different to this API. They are incompatible, which means using both is NOT recommended as it may result in connectivity issues.
Abuse cases
Mozilla says the add-ons were advertised to users as being able bypass paywall restrictions on websites. It is unknown whether the blocking of updates was intentional and whether the add-ons were performing other malicious actions.
Mozilla has blocked the malicious add-ons so they are not installed by anyone else. Starting with Firefox 91.1, Firefox now includes changes to fall back to direct connections when Firefox makes an important request (such as those for updates) via a proxy configuration that fails. By doing so, users can not be denied important updates.
Mitigation
Mozilla stopped accepting add-on submissions that use the proxy API until fixes were available for all users.
One of those fixes lies in the fact that Mozilla deployed a system add-on named “Proxy Failover” (ID: [email protected]) with additional mitigations, and that has been shipped to both current and older Firefox versions. This system add-on implements failover rules for system requests over malfunctioning proxies. In other words, If a proxied system request fails, the proxy configuration in use will be disabled.
As usual, make sure your browser is up to date. The latest version of the Firefox Standard Release for Desktop is at 93.0.
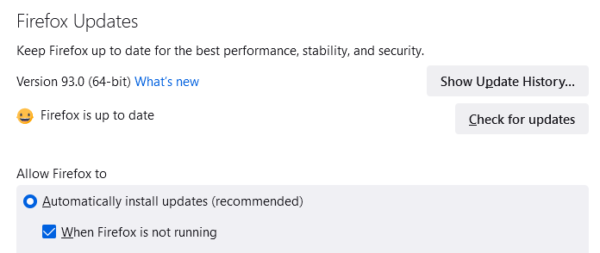
In case you are not running the latest version, and have not disabled updates, you might want to check if you are affected by this issue. First, try updating Firefox manually (In the menu click Settings > on the General tab scroll down to > Firefox Updates > click on the Check for updates button). Recent versions of Firefox come with an updated blocklist that automatically disables the malicious add-ons. So you should be able to get an update.
If that does not work you are advised to check In the Add-ons section, and search for one of the following entries:
- Name: Bypass ID: {7c3a8b88-4dc9-4487-b7f9-736b5f38b957}
- Name: Bypass XM ID: {d61552ef-e2a6-4fb5-bf67-8990f0014957}
Please make sure the ID matches exactly as there might be other, unrelated add-ons using those or similar names. If none of those IDs are shown in the list, you are not affected.
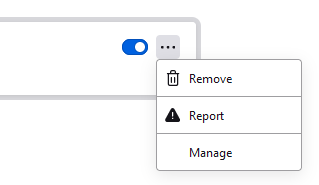
If you do find one of these entries, you can remove the add-on under the Add-ons and themes section of the menu, by clicking on the three horizontal dots and select Remove from the dropdown menu.
Using the proxy API going forward
Developers that wish to use the proxy API for legitimate reasons are asked to include a strict_min_version key in their manifest.json files targeting “91.1” or above. This will make sure that the users will not suffer blocked updates and it will expedite the review for your add-on.
Stay safe everyone
The post Patch now to bypass Firefox add-ons that abuse the proxy API to deny updates appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![Cobalt Strike Beacon Detected - 8[.]219[.]161[.]236:48899 4 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
