Patch Tuesday – June 2020

June 2020’s Microsoft Patch Tuesday gives us a whopping 129 CVEs patched (excluding Adobe Flash which addresses CVE-2020-9633 — a high severity remote code execution vulnerability). While the consistently high volume of vulnerabilities being addressed each month is alarming at times, there is a sense of peace in the steps Microsoft is taking on closing vulnerabilities fast and effectively through the virtues of cumulative patching on Windows 10-based operating systems (both Server and Client) and Monthly Rollup (or Security-Only) bundles of previous operating systems.
This month, a substantial number of vulnerabilities were held within the core components of Windows itself (including the Kernel) covering 54 of the 129 vulnerabilities. Particularly noteworthy are two Windows Media-related vulnerabilities (CVE-2020-1238, CVE-2020-1239) which I would almost bundle with “browser vulnerabilities” as its likely vector is a malicious webpage.
Continuing on the browser vulnerabilities front, we continue to emphasize the importance of good security practices and hygiene in not clicking (or installing) random links (applications). 5 of the 11 Critical RCEs noted this month (CVE-2020-1213, CVE-2020-1216, CVE-2020-1219, CVE-2020-1073, CVE-2020-1260) are browser based and can be heavily mitigated via good practices. Despite this, it is always better to patch as situations like CVE-2020-1213 (which is a VBScript RCE where an attacked could also embed an ActiveX control marked “safe for initialization”) can and often do occur.
In terms of urgency, critical remote execution vulnerabilities are typically choice patches to prioritize. Luckily this month, of the 11 Critical RCE vulnerabilities, 10 can be remediated via Operating System patches. The remaining CVE-2020-1181 is a SharePoint patch which would be more dependent on your environment.
Last, but not least, I want to acknowledge the SMBv3 vulnerabilities being addressed this month, and one interesting OpenSSH (CVE-2020-1292 – AttackerKB entry) privilege escalation vulnerability. CVE-2020-0796 (initially Security Advisory ADV200005), disclosed back in March 2020, is now seeing functional PoCs targeting unpatched systems. Part of this process has been to pivot off local privilege escalation, something that CVE-2020-1292 can provide a means of accomplishing. Strictly on the SMBv3 side, these vulnerabilities (CVE-2020-1206, CVE-2020-1284) continue to affect only Windows 10 variants on Version 1903 onwards. There is commonality between all these vulnerabilities however, and it is that mitigation can be accomplished via disabling SMBv3 compression, which is stated as having no negative performance impact (yet). There are patches, and patches will always be a solid strategy, but it’s nice to know what the alternatives could be. As for CVE-2020-1301 (AttackerKB entry), an SMBv1 remote code execution vulnerability — please consider disabling SMBv1 if it’s not a mission critical component of your infrastructure, or at least have a migration plan in place.
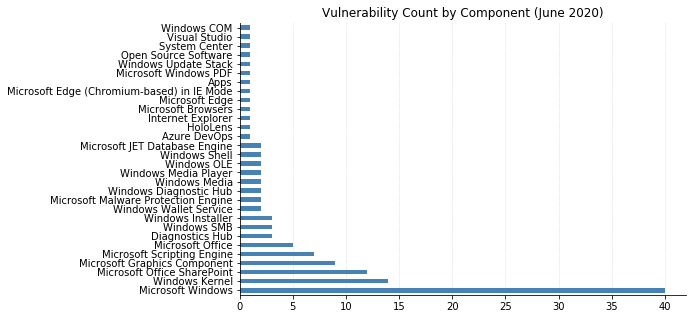
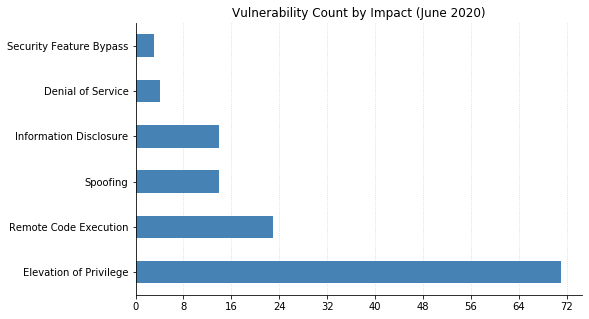
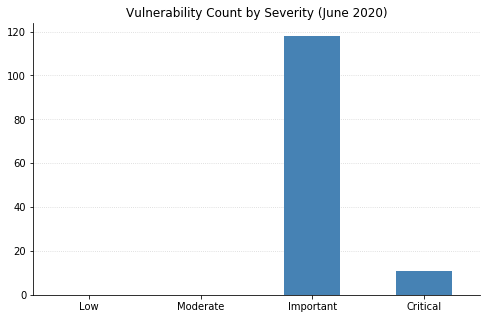
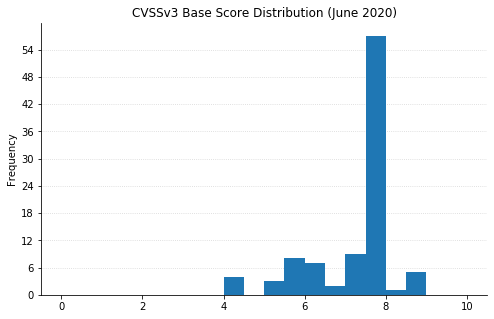
Note: Graph data is reflective of data presented by Microsoft’s CVRF at the time of writing.

