Patch Tuesday – May 2020

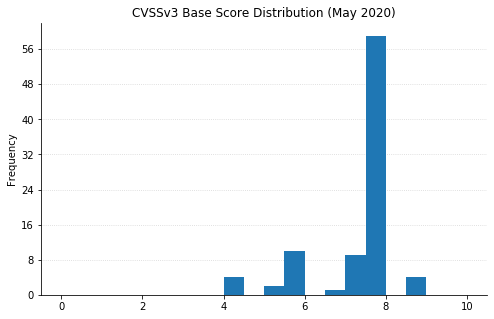
Microsoft’s fifth Patch Tuesday of the year brings us fixes for 111 different security issues, just a touch under what we saw from them last month but still on the higher side of their typical volume. No 0-days to speak of, and no vulnerabilities that had been publicly disclosed before today.
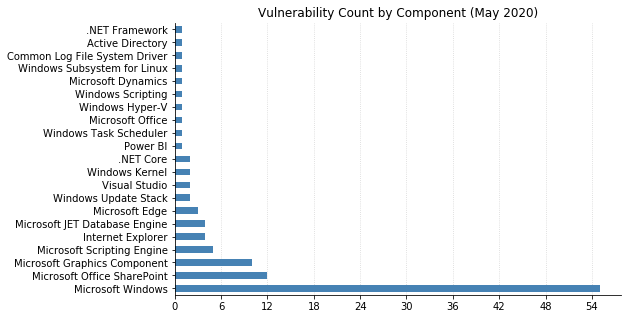
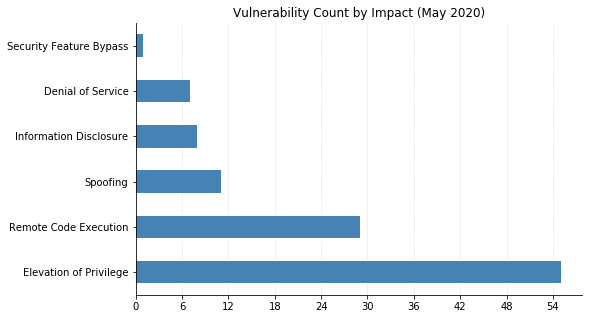
The bulk of this month’s fixes, as well as most of the critical ones, are for core components of the Windows operating system itself. 44 of the 55 Windows vulnerabilities allow elevation of privilege, a favourite for attackers who want to expand their capabilities after getting an initial foothold (perhaps by first exploiting CVE-2020-1126, for example, a new Remote Code Execution (RCE) vulnerability in Windows Media Foundation).
There is a smattering of browser vulnerabilities, fewer than usual but still worth your attention. CVE-2020-1062 and CVE-2020-1035 are two of several vulnerabilities this month that allows RCE in Internet Explorer. Three vulnerabilities in Edge could allow spoofing (CVE-2020-1059), RCE (CVE-2020-1096, related to Edge’s PDF reader), or elevation of privilege (CVE-2020-1056) for anyone an attacker can convince to visit a malicious website. Only one vulnerability is being patched in Office: CVE-2020-0901 is an RCE in Excel on all supported versions (including Office for Mac).
SharePoint admins need to be aware of twelve distinct CVEs being patched this month, including CVE-2020-1069 (one of four RCEs), seven spoofing weaknesses, and an information disclosure vulnerability (CVE-2020-1103). Also on the server side, CVE-2020-1055 affects Active Directory Federation Services and could allow an unauthenticated attacker to perform cross-site scripting attacks on affected systems, running scripts as the current user of the system.
Similar to April, and likely a relief to many administrators who are still facing the task of patching remotely working fleets, most of this month’s issues will be addressed by relatively few KBs. And don’t forget about Adobe, who published fixes for 22 CVEs in Acrobat and Reader (APSB20-24).
Good luck patching!
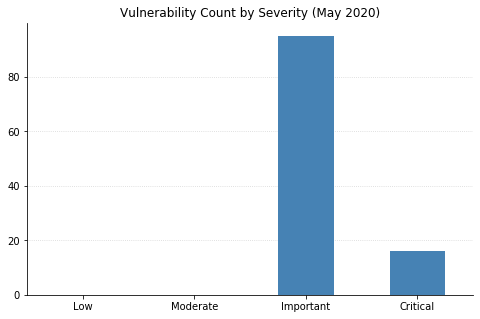

![Cobalt Strike Beacon Detected - 121[.]43[.]227[.]196:777 8 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)