PingRAT – Secretly Passes C2 Traffic Through Firewalls Using ICMP Payloads
PingRAT secretly passes C2 traffic through firewalls using ICMP payloads.
Features:
- Uses ICMP for Command and Control
- Undetectable by most AV/EDR solutions
- Written in Go
Installation:
Download the binaries
or build the binaries and you are ready to go:
$ git clone https://github.com/Nemesis0U/PingRAT.git
$ go build client.go
$ go build server.go
Usage:
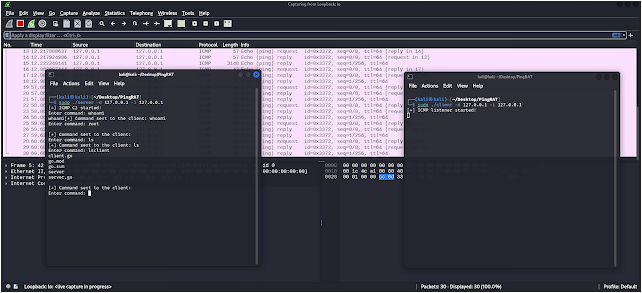
Server:
./server -h
Usage of ./server:
-d string
Destination IP address
-i string
Listener (virtual) Network Interface (e.g. eth0)
Client:
./client -h
Usage of ./client:
-d string
Destination IP address
-i string
(Virtual) Network Interface (e.g., eth0)A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.



![Cobalt Strike Beacon Detected - 119[.]45[.]29[.]172:8089 5 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
