Police seize Netwire RAT malware infrastructure, arrest admin

An international law enforcement operation involving the FBI and police agencies worldwide led to the arrest of the suspected administrator of the NetWire remote access trojan and the seizure of the service’s web domain and hosting server.
NetWire was a remote access trojan promoted as a legitimate remote administration tool to manage a Windows computer remotely.
The service was sold via the website www.worldwiredlabs.com, where users could sign up for subscriptions for as little as $10 a month, which included support.
However, since at least 2014, NetWire has been a tool of choice in various malicious activities, including phishing attacks, BEC campaigns, and to breach corporate networks.
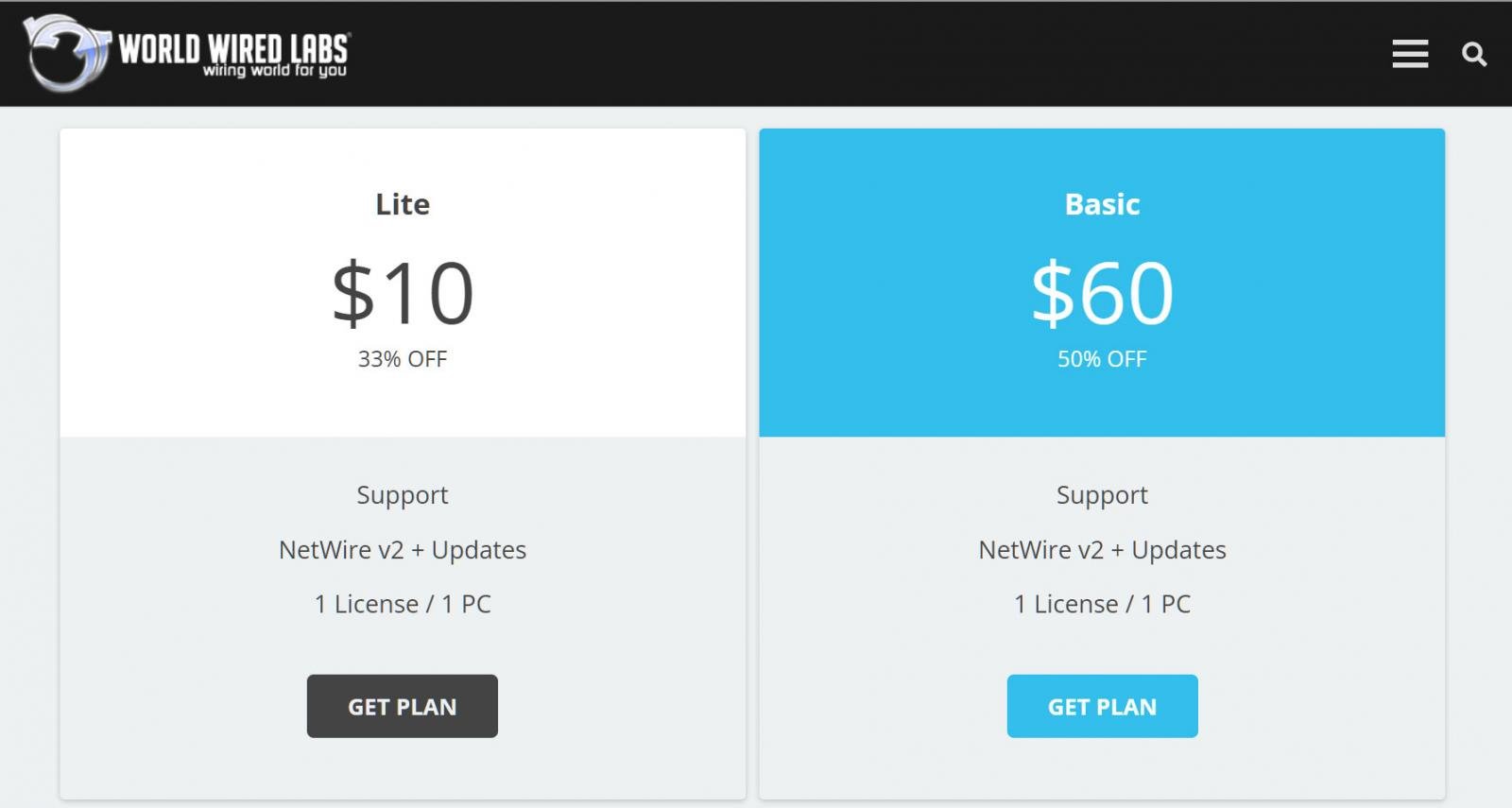
Threat actors could use the Netwire RAT to remotely take screenshots, download and upload files, execute commands, or download further programs to execute on infected Windows computers.
NetWire infrastructure seized by police
Today, the U.S. Attorney’s Office for the Central District of California announced that a seizure warrant was approved on March 3rd and executed in a coordinated international law enforcement operation on Tuesday to disrupt the NetWire service.
This operation involved police from the FBI, the United States Attorney’s Office for the Central District of California, the Croatia Ministry of the Interior Criminal Police Directorate, Zurich Cantonal Police, Europol, and the Australian Federal Police.
As part of this operation, the FBI seized the worldwiredlabs.com domain used to promote the service, and police in Switzerland seized the server hosting the website.
The website now displays a seizure message, stating, “This Website Has Been Seized as part of a coordinated law enforcement action taken against the NetWire Remote Access Trojan.”
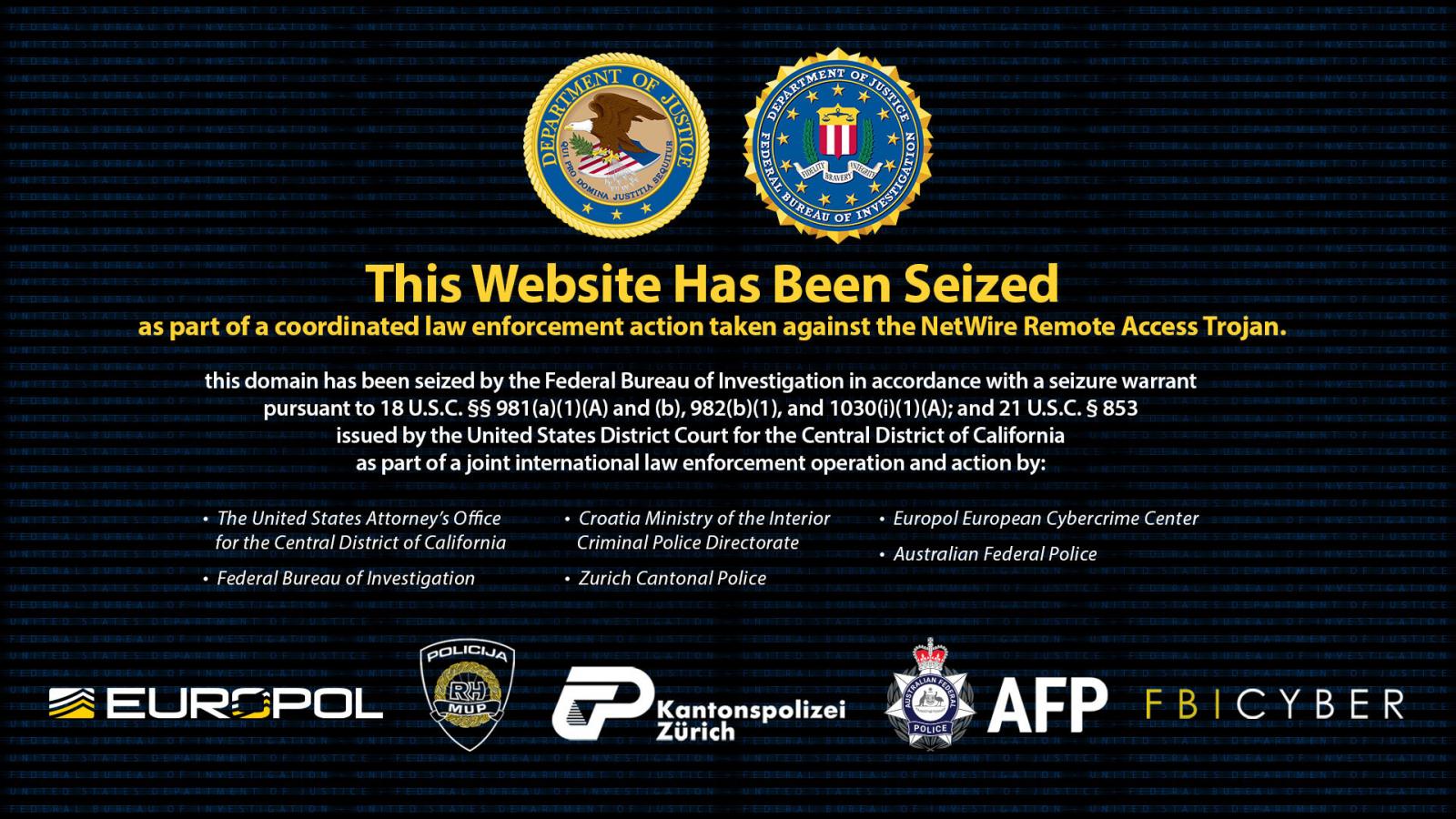
Source: BleepingComputer
A Croatian national suspected to be the administrator of the NetWire website was also arrested on Tuesday in Croatia and will be prosecuted by local authorities.
“By removing the Netwire RAT, the FBI has impacted the criminal cyber ecosystem,” said Donald Alway, the Assistant Director in Charge of the FBI’s Los Angeles Field Office.
“The global partnership that led to the arrest in Croatia also removed a popular tool used to hijack computers in order to perpetuate global fraud, data breaches and network intrusions by threat groups and cyber criminals.”
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.






![[DRAGONFORCE] - Ransomware Victim: Pratt Homes 11 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)