Preparing for the Cybersecurity Maturity Model Certification (CMMC) Part 1: Practice and Process

All of us here at Rapid7 hope that you and your families are safe and well during this unprecedented national crisis. Despite the fact that COVID-19 has many of us focused on other priorities, the expectation at the time of publication of this blog is that the Cybersecurity Maturity Model Certification (CMMC) is proceeding along original timelines. The certification is presently expected to be phased into new DoD contracts starting in Q3 2020. As such, it is important that all affected organizations continue to prepare for the requirements. In Part 1 of our CMMC Blog series, we’ll look at better explaining terms and structure of the framework.
In current developments, the CMMC Accreditation Body has been established, and it has formed the CMMC Standard Management Working Groups, with objectives of refining the CMMC Standards and Requirements Assessment Guide and developing the Certification Assessment Criteria Levels and Training and Learning Objectives. Additional working groups have been formed, and that information can be found here.
CMMC certification will be required for all contractors and subcontractors working with the U.S. Department of Defense. The goal is to enhance the protection of this information within the Department of Defense supply chain. While CMMC primarily leverages existing standards and regulations, such as FAR Clause 52.204-21 and National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171, it also draws from other best practices.
Under CMMC, organizations can no longer self-assess against 800-171 to be awarded DoD contracts. Instead, organizations will need to be certified by CMMC third-party assessment organizations (C3PAOs) accredited by the CMMC Accreditation Body. Both DoD and the CMMC Accreditation Body encourage organizations to perform self-evaluations for CMMC compliance prior to an official assessment from a C3PAO.
Version 1 of CMMC was released on Jan. 30, and a minor revision of the document, version 1.02, has since been released in March. The latest versions can be found here.
To understand the CMMC framework, you must understand how the different elements work.
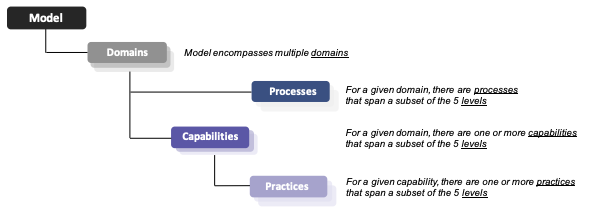
We’ll go through some of these terms in the following sections.
Domains
The CMMC defines 17 domains, familiar to anyone who has experience with NIST framework requirements. Organizations familiar with 800-171 will notice three additional domains defined within CMMC. These domains are defined as follows:
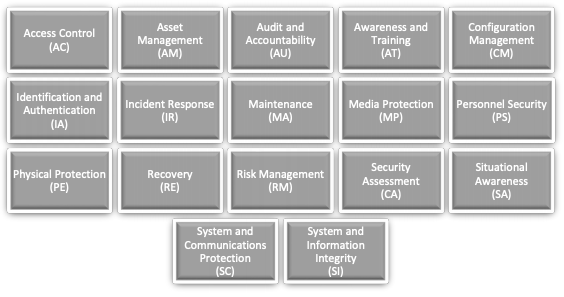
Each domain has a set of defined criteria that define the overall maturity level for your organization.
Level with us
The CMMC model measures cybersecurity maturity across five levels. Each level consists of a set of processes and practices within a domain. Practices further define capabilities (to be expanded upon in Part 2 of this blog series).
Compliance with CMMC requirements will occur at one of these five levels, depending on the sensitivity of information processed by organizations along the DoD supply chain. All DoD contractors will be required to certify at Level 1 or above, and all contractors that handle any Controlled Unclassified Information (CUI) must certify at Level 3 or above. DoD contract RFIs will specify the certification level required for a contract award.
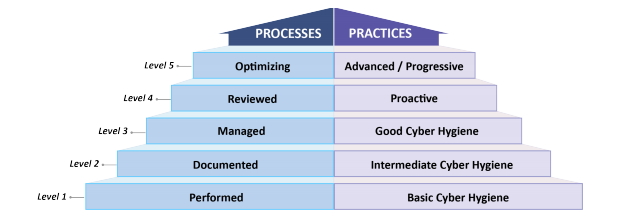
It’s important to understand that the set of processes and practices is cumulative, meaning that in order to achieve compliance with a specific maturity level, an organization must be compliant with all preceding maturity levels as well. Additionally, it is not enough to have practices implemented. Maturity of process is also required, and this is evaluated by the extent to which the practices are ingrained within the culture of your organization, which the CMMC refers to as institutionalization. If your organization demonstrates Level 3 maturity within a practice, but only a Level 2 maturity within the process, the compliance is certified at the lower of the two maturity levels.
Practices
There are a total of 171 practices mapped across the five levels of CMMC maturity.
- Level 1: 17 practices
- Level 2: 72 total practices (17 Level 1 + 55 additional)
- Level 3: 130 total practices (72 Level 2 + 58 additional)
- Level 4: 156 total practices (130 Level 3 + 26 additional)
- Level 5: 171 total practices (156 Level 4 + 15 additional)
The practices are derived primarily from the following sources:
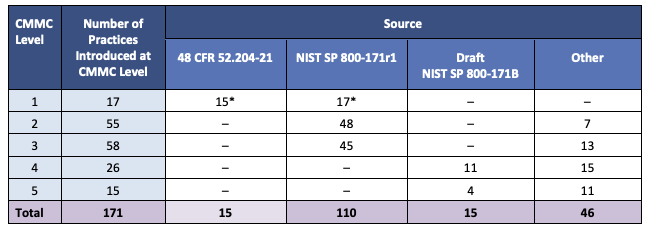
Again, you will notice that if you have been compliant with FARS clause 52.204-21 and 800-171, you are likely in good shape to meet the practice requirements of CMMC, especially at lower maturity levels. However, as your requirement to achieve higher overall maturity levels increases, so do the additional requirements (see “Other” above”).
An example of practice implementation for the Identification and Authentication (IA) domain:
- A Level 2 practice would be to enforce minimum password requirements
- A Level 3 practice would be to use multifactor authentication.
Processes
As mentioned earlier, it’s no longer enough to have mature practices in place. You must also be able to demonstrate process maturity—institutionalization of the practices—to achieve certification at the maturity levels. Keep in mind, process maturity is evaluated differently than practice maturity, but both are required.
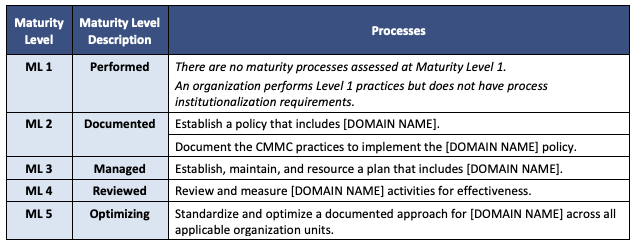
Building on the Identification and Authentication (IA) practice example from above, process maturity would be defined as:
- A Level 2 Process Maturity might mean that you have authentication policies defined for applicable systems, and that password requirements are defined. This could include more detailed procedural documentation.
- A Level 3 Process Maturity might mean that your organization can demonstrate more ingrained authentication processes, and that perhaps multifactor authentication is built into all new system requirements by default.
In Part 2 of the CMMC blog series, we’ll break down these practices and processes in greater detail, and discuss capabilities in additional detail and provide some examples of how all these concepts tie together.
How Rapid7 can help
As with most frameworks, CMMC defines the practices your organization must implement. Implementation guidance exists with the CMMC Appendices, although as with most standards and frameworks, the guidance is currently ambiguous and open to interpretation in some cases. To ensure your organization is ready for CMMC certification, it is recommended that you begin reviewing how you have these requirements defined and implemented.
Rapid7 can provide readiness assessments of your organization at any level of the CMMC requirements by leveraging our consultant team’s vast experience. We can look at your organization’s implementation of security governance and technology controls to help answer the process institutionalization questions you likely have. Rapid7 can also provide a Plan of Actions & Milestones (POA&M) to help you quickly understand weaknesses or deficiencies in deployed security controls or processes, and give you a path forward toward compliance.
Additionally Rapid7 has solutions that can meet CMMC practice requirements. As an example, InsightIDR meets the requirements of practice IR.2.093, and InsightVM meets the requirements of RM.2.142.
Be aware that, as of early April, the CMMC Accreditation Body has not yet certified any CMMC Third Party Assessment Organizations (C3PAO). As such, neither Rapid7 nor any other third party can currently provide a CMMC certification. A Memorandum of Understanding (MOU) has just been signed between the Accreditation Body (CMMC-AB) and DoD, and the AB is working to define the criteria for becoming a C3PAO and to define certification testing requirements. However, organizations can (and should!) prepare for an official CMMC assessment by self-evaluating their cybersecurity programs against the DoD’s CMMC model.
Need a CMMC readiness assessment? Our team of experts are ready to help.
Learn More

![[HANDALA] - Ransomware Victim: Saturday Unveilings – Shadows Have Names 7 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

