Proof-of-Concept released for critical Microsoft Word RCE bug

A proof-of-concept for CVE-2023-21716, a critical vulnerability in Microsoft Word that allows remote code execution, has been published over the weekend.
The vulnerability was assigned a 9.8 out of 10 severity score, with Microsoft addressing it in the February Patch Tuesday security updates along with a couple of workarounds.
The severity score is mainly given by the low attack complexity coupled with the lack of privileges and user interaction required to exploit it.
Tweet-sized PoC
Security researcher Joshua Drake last year discovered the vulnerability in Microsoft Office’s “wwlib.dll” and sent Microsoft a technical advisory containing proof-of-concept (PoC) code showing the issue is exploitable.
A remote attacker could potentially take advantage of the issue to execute code with the same privileges as the victim that opens a malicious .RTF document.
Delivering the malicious file to a victim can be as easy as an attachment to an email, although plenty of other methods exist.
Microsoft warns that users don’t have to open a malicious RTF document and simply loading the file in the Preview Pane is enough for the compromise to start.
The researcher explains that the RTF parser in Microsoft Word has a heap corruption vulnerability that is triggered “when dealing with a font table (*\fonttbl*) containing an excessive number of fonts (*\f###*).”
Drake says that there is additional processing after the memory corruption occurs and a threat actor could leverage the bug for arbitrary code execution by using “a properly crafted heap layout.”
The PoC from the researcher shows the heap corruption problem but stops short of launching the Calculator app in Windows, to demonstrate code execution.
Initially, the PoC had a little over a dozen lines, including comments. Since the report sent to Microsoft in November 2022, the researcher trimmed down some lines and managed to fit everything in a tweet:
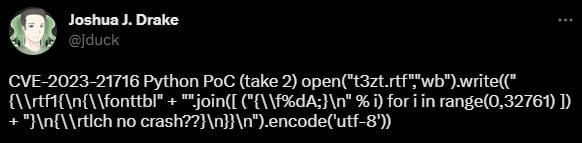
source: Joshua Drake
At the moment there is no indication that the vulnerability is being exploited in the wild and Microsoft’s current assessment is that taking advantage of the issue is “less likely.”
Critical vulnerabilities like this one draw the attention of threat actors, with the more advanced ones trying to reverse engineer the fix to find a way to leverage it.
Typically, when exploit code becomes available, a larger pool of attackers starts using the vulnerability since less effort is needed to modify a PoC than to come up with an exploit from scratch.
It is unclear if the current PoC from Joshua Drake can be weaponized into a full-blown exploit since it only shows exploitation to be possible without proving it.
However, this a remote code execution in Microsoft Word is highly coveted and would allow wide-scale distribution of malware via email.
A similar vulnerability in the Microsoft Excel Equation Editor has long since been patched, and is still used today in some campaigns.
Workarounds could backfire
A full list of the Microsoft Office products impacted by the vulnerability is available in the vendor’s advisory for CVE-2023-21716.
For users that cannot apply the fix, Microsoft recommends reading emails in plain text format, something unlikely to be adopted due to the resulting inconveniences (lack of images and rich content).
Another workaround is to enable the Microsoft Office File Block policy, which prevents Office apps from opening RTF documents of unknown or untrusted origin.
This method requires modifying the Windows Registry and also comes with a caveat: “if you use Registry Editor incorrectly, you may cause serious problems that may require you to reinstall your operating system.”
Additionally, if an “exempt directory” has not been set, users run the risk of not being able to open any RTF document.
Even if a complete exploit is currently unavailable and only theoretical, installing the security update from Microsoft remains the safest way to deal with the vulnerability.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.






![[DRAGONFORCE] - Ransomware Victim: Pratt Homes 9 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)