QakBot Malware Operators Expand C2 Network with 15 New Servers
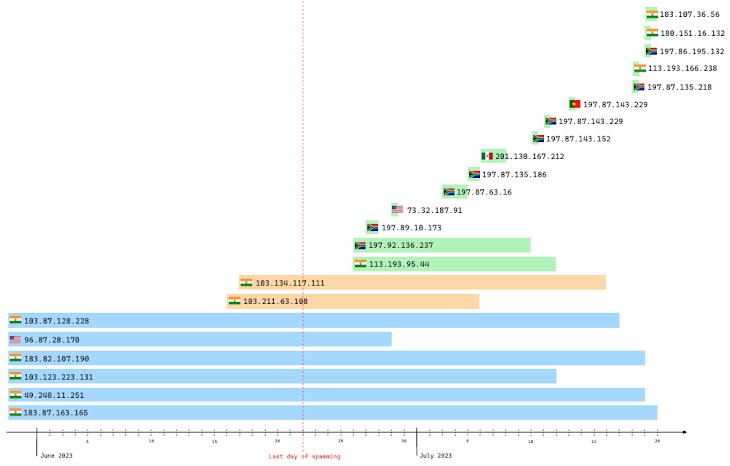
The operators associated with the QakBot (aka QBot) malware have set up 15 new command-and-control (C2) servers as of late June 2023.
The findings are a continuation of the malware’s infrastructure analysis from Team Cymru, and arrive a little over two months after Lumen Black Lotus Labs revealed that 25% of its C2 servers are only active for a single day.
“QakBot has a history of taking an extended break each summer before returning sometime in September, with this year’s spamming activities ceasing around 22 June 2023,” the cybersecurity firm said.
“But are the QakBot operators actually on vacation when they aren’t spamming, or is this ‘break’ a time for them to refine and update their infrastructure and tools?”
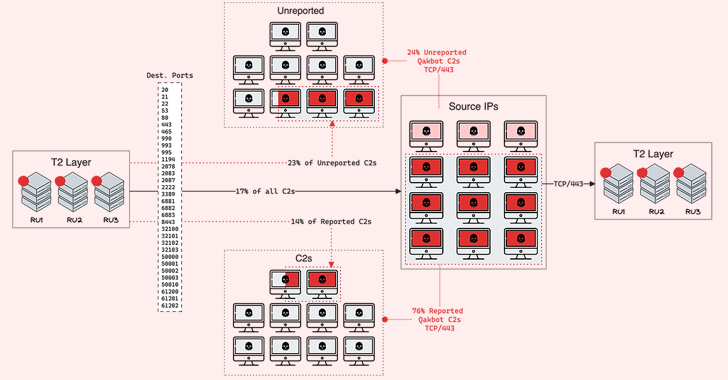
QakBot’s C2 network, like in the case of Emotet and IcedID, is characterized by a tiered architecture in which C2 nodes communicate with upstream Tier 2 (T2) C2 nodes hosted on VPS providers geolocated in Russia.
A majority of the bot C2 servers, which communicate with the victim hosts, are located in India and the U.S. Destination IP addresses identified from outbound T2 connections are primarily based in the U.S., India, Mexico, and Venezuela.
Also present alongside the C2s and the Tier 2 C2s is a BackConnect (BC) server that turns the infected bots into a proxy for other malicious purposes.
The latest research from Team Cymru reveals that the number of existing C2s communicating with the T2 layer has significantly decreased, with only eight remaining, in part driven by Black Lotus Labs’ null-routing of the higher-tier infrastructure in May 2023.
“We observe that on June 2, U.S. C2s all but disappeared, and traffic from Indian C2s significantly decreased,” the company said, attributing the lack of U.S. activity to null-routing the T2 layer.
Outside of the 15 C2 servers, six C2 servers active since before June and two C2 servers that came alive in June have continued to exhibit activity in July after spamming concluded.
A further analysis of NetFlow data exhibits a pattern wherein “instances of increased outbound T2 connections often occur following spikes in activity for inbound bot C2 connections” and “spikes in outbound T2 connections frequently correspond with a decline in bot C2 activity.”
“In elevating victims to be used as C2 infrastructure with T2 communication, QakBot effectively punishes users twice, first in the initial compromise, and second in the potential risk to reputation of a host being identified publicly as malicious,” Team Cymru said.
By cutting off communications to the upstream servers, the company pointed out, victims are prevented from receiving C2 instructions, thereby effectively protecting current and future users from compromise.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![Cobalt Strike Beacon Detected - 154[.]204[.]35[.]215:80 1 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)