RagnarLocker ransomware gang breached 52 critical infrastructure organizations
In a FLASH publication issued by the FBI in coordination with DHS/CISA, the FBI says it has identified at least 52 organizations across 10 critical infrastructure sectors affected by RagnarLocker ransomware, including organizations in the critical manufacturing, energy, financial services, government, and information technology sectors.
Threat profile
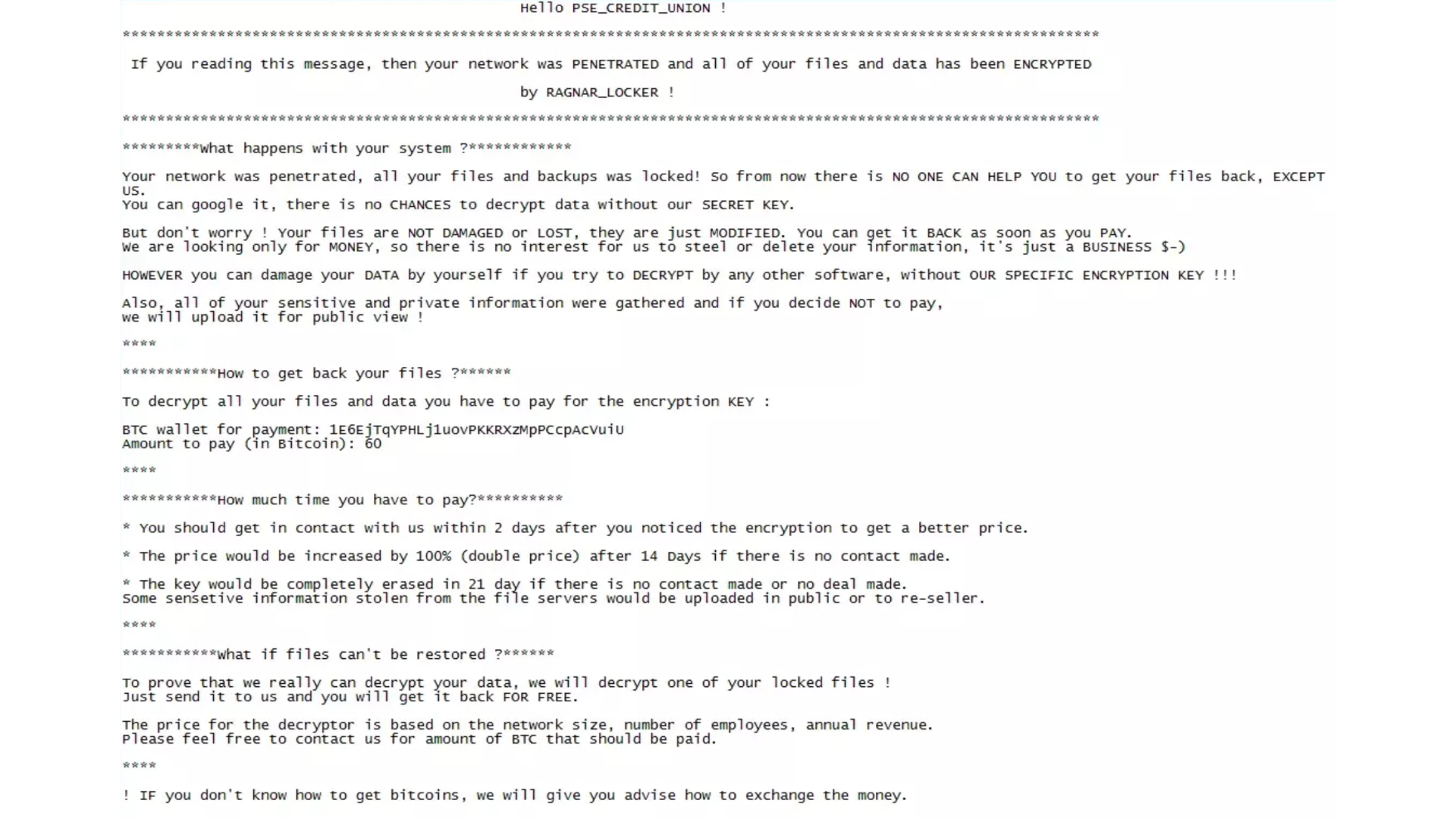
RagnarLocker can be recognized by the extension of the encrypted files which contains “.RGNR_<ID>,” or “.ragnar_<ID>” where <ID> is a hash of the computer’s NETBIOS name.
The ransom note is called “.RGNR_[extension].txt” and states the files and data have been encrypted by RAGNAR_LOCKER.
Exfiltrated data of victims that refuse to pay will be published on the “Wall of Shame” leak site.
RagnarLocker iterates through all running services and terminates services commonly used by Managed Service Providers (MSPs) to remotely administer networks. The malware then attempts to silently delete all Volume Shadow Copies, preventing user recovery of encrypted files.
Don’t call the cops
In the past, RagnarLocker has warned victims explicitly against contacting the FBI, or other law enforcement agencies for that matter. In September 2021, the ransomware operators threatened to publish all the data of victimized organizations that seek help from law enforcement or investigators following ransomware attacks.
But, in the wake of recent high-profile cyber and ransomware attacks, Congress and the Biden administration have joined forces to drive policy changes that would require organizations to report certain cyberincidents to the federal government. Importantly, the legislation would give organizations 72-hours to report a cyberincident. Ransomware attacks by an entity believed to originate from the CIS would certainly qualify as such.
The FBI urges you to report ransomware incidents to your local field office. Doing so provides investigators and analysts with the critical information they need to track ransomware attackers, hold them accountable under US law, and prevent future attacks.
The FBI says it would like the following information:
Short term items:
- Copy of the ransom note (screen shot/picture/text file)
- Any discovered malicious IPs with time stamps/time zones (unusual RDP connections/unusual VPN connections/beacons to malicious IPs)
- Virtual currency addresses/amount of demand
- Any malicious files (executables/binaries)
- Summary of timeline of events (dates of initial observation/malicious activity)
- Evidence of data exfiltration
Long term items:
- Brief summary of where the IOCs came from
- Incident response report
- Copy of any communications with malicious actors
- Forensic images and memory captures
- Host and network logs
- Any available decryptor
- Scope of impact (amount of loss)
CIS
As mentioned in our blog post Ransomware’s Russia problem, RagnarLocker is believed to be of Russian origin and will try to avoid making victims in the Commonwealth of Independent States (CIS). To do so, Ragnar Locker uses Windows API GetLocaleInfoW to identify the location of the infected machine. If the victim location is identified as “Azerbaijani,” “Armenian,” “Belorussian,” “Kazakh,” “Kyrgyz,” “Moldavian,” “Tajik,” “Russian,” “Turkmen,” “Uzbek,” “Ukrainian,” or “Georgian,” the process terminates.
IOCs
In the pdf file that carries FLASH Number CU-000163-MW you can find the current IOCs, including IP addresses, Bitcoin addresses, and email addresses.
Mitigation
To stay out of the claws of the RagnarLocker group the usual mitigation techniques for ransomware apply. The FBI lists:
- Use multi-factor authentication with strong passwords, including for remote access services.
- Keep computers, devices, and applications patched and up-to-date.
- Monitor cyberthreat reporting regarding the publication of compromised VPN login credentials and change passwords and settings.
- Consider adding an email banner to emails received from outside your organization.
- Disable unused remote access/Remote Desktop Protocol (RDP) ports and monitor remote access/RDP logs.
- Audit user accounts with administrative privileges and configure access controls with least privilege in mind.
- Implement network segmentation.
The FBI recommends backup strategies to speed up recovery from a ransomware attack:
- Back-up critical data offline.
- Ensure copies of critical data are in the cloud or on an external hard drive or storage device. This information should not be accessible from the compromised network.
- Secure your backups and ensure data is not accessible for modification or deletion from the system where the data resides.
Stay safe, everyone!
The post RagnarLocker ransomware gang breached 52 critical infrastructure organizations appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


