Ransomware in November 2022
Malwarebytes Threat Intelligence builds a monthly picture of ransomware activity by monitoring the information published by ransomware gangs on their Dark Web leak sites. This information represents victims who were successfully attacked but opted not to pay a ransom.
In a surprising turn of events, LockBit was NOT the most prevalent ransomware in November. New player Royal accounted for the plurality of all ransomware attacks last month, racking up a total of 45 alleged victims.
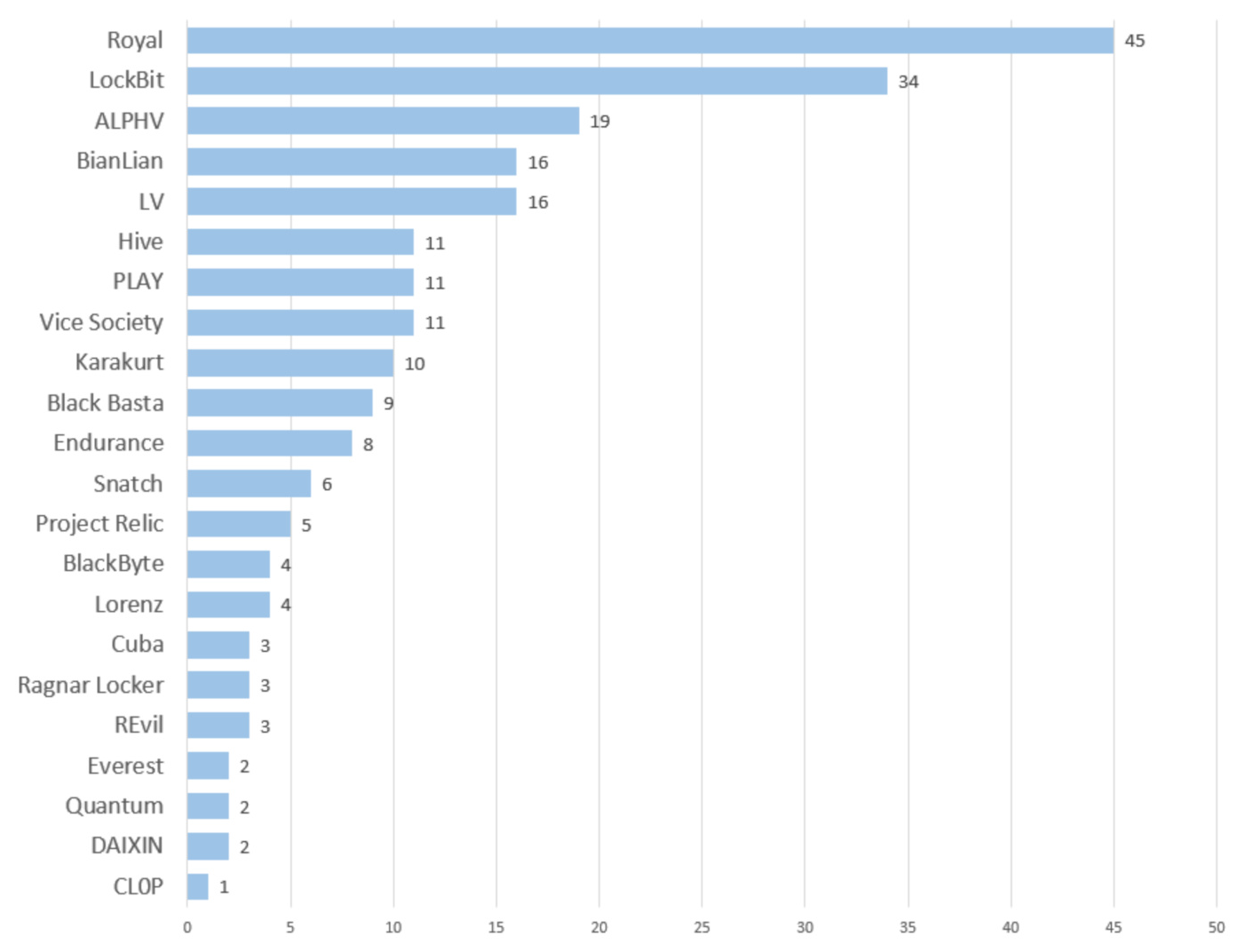
LockBit has far and away been the most used ransomware of 2022, accounting for about one third of all known attacks. However, the number of victims posted on its dark web leak site is on a steady three-month decline: September (109), October (59), and November (34).
At the same time, new gangs such as Project Relic and Royal have made headlines—with Royal even managing to topple LockBit as the month’s biggest ransomware player. Old players such as Play, on the other hand, were seen using new tactics.
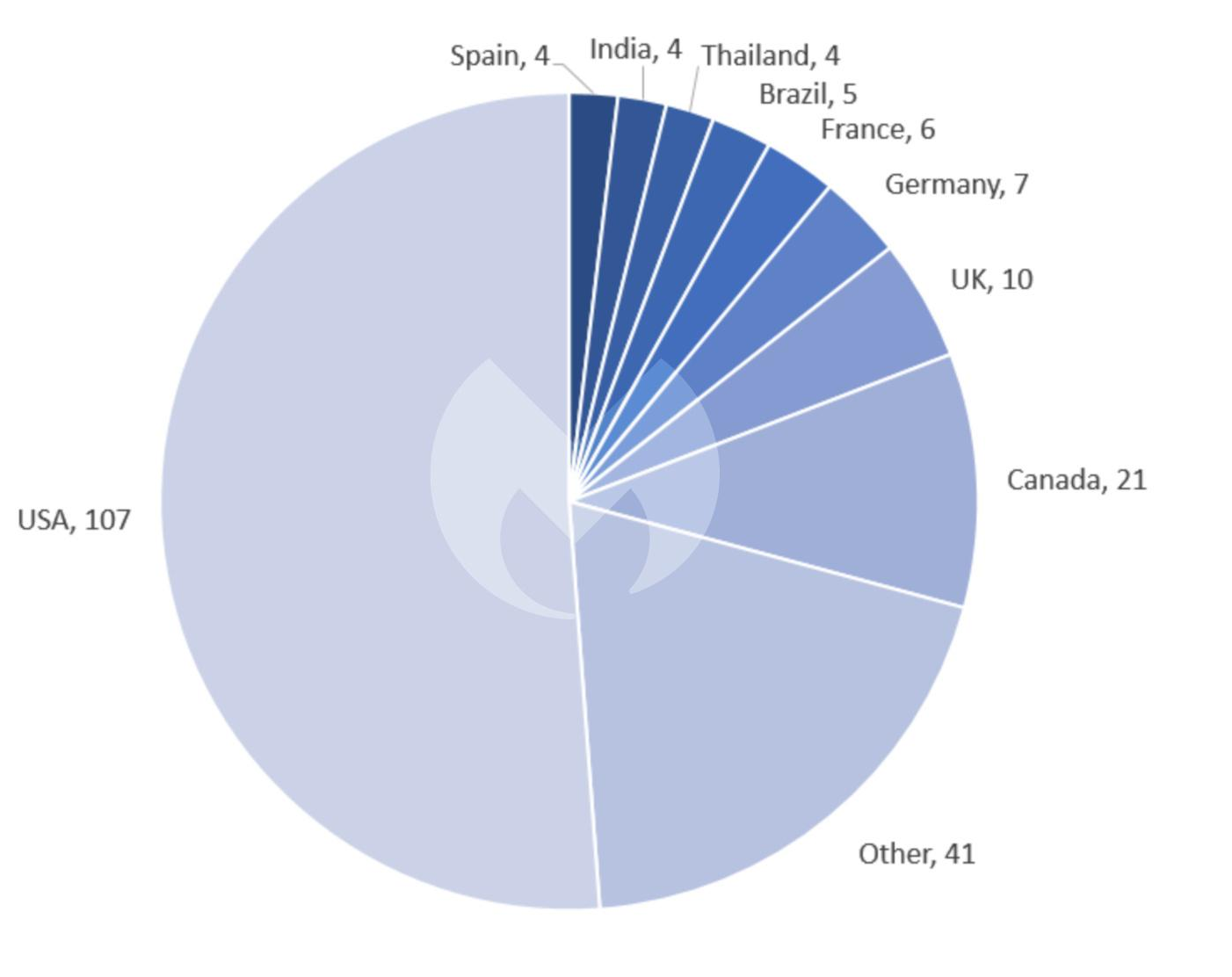
In November, the USA was the country hit most by ransomware, suffering over 100 known ransomware attacks for the first time all year since April.
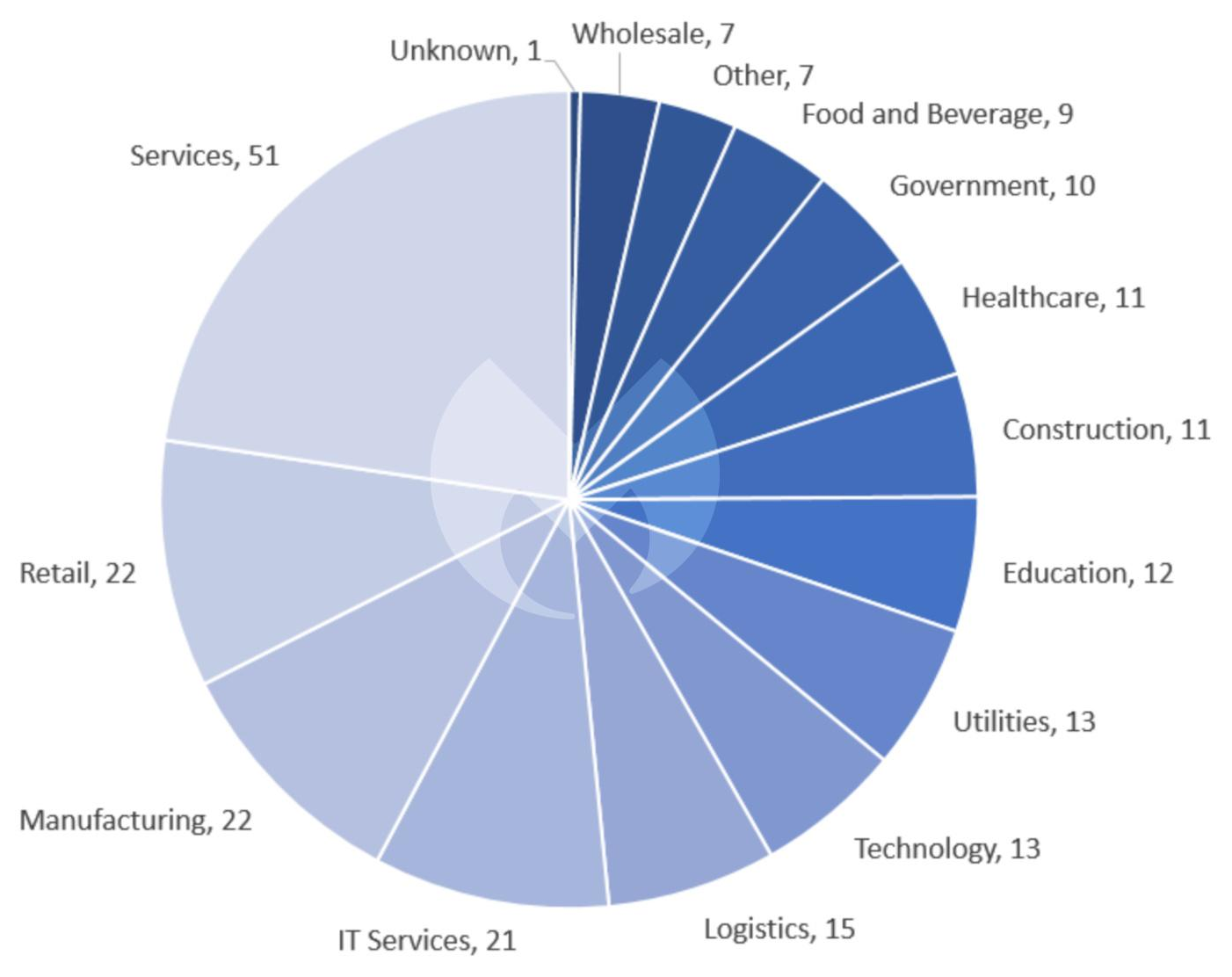
As has been the case all year, services was the most afflicted sector in November. Attacks on retail jumped to a three-month high, tying with manufacturing at 22 attacks, while attacks on IT services jumped from 13 attacks in October up to 22.
Royal dethrones LockBit
The Royal ransomware emerged in January 2022, its distribution initially attributed to a group Microsoft researchers dubbed DEV-0569. It wasn’t until September 2022, however, that the threat actors behind this ransomware officially branded themselves with the name Royal.
By November 2022, Royal had claimed responsibility for a ransomware attack on Silverstone Circuit, one of the UK’s most popular race tracks. Other high-profile attacks include victims such as M2S Electronics, Virginia Farm Bureau, and Cristal Controls.
Royal is different from the traditional ransomware-as-a-service model in that it works as a private gang, without affiliates. According to Microsoft’s research, the group relies on several ways to carry out their attacks, such as malicious ads, fake forum pages, blog comments, and phishing emails. In their software downloader attacks, for example, a victim downloads malware posing as an installer for applications such as Teamviewer or Zoom. In reality the victim downloads BATLOADER, an initial access malware that uses batch and PowerShell scripts to infiltrate victim machines. The gang also carries out malvertising campaigns using Google Ads.
With Royal eclipsing LockBit as the number one gang in November, the question becomes not so much how Royal rose, but more so why Lockbit fell: Its 34 victims in November was its lowest monthly total all year.
One possible reason for this decline is the fact that a LockBit affiliate was arrested in Canada last month. After a two-and-a-half-years investigation into LockBit that began in March 2020, the US Justice Department announced on November 10 that it had arrested a dual Russian-Canadian national for his alleged participation in the LockBit campaign. Not only does that make one less affiliate, but it may have stoked fear and increased caution among other affiliates.
Project Relic
A relatively new group calling itself Project Relic attacked a Puerto Rico hospital last month, leaking 114 GB of sensitive information. Not much is known about the newcomer, which is believed to have only started operating in October 2022. Project Relic is similar to other ransomware groups in that it uses a chat application for negotiations and a dark web leak site, pictured below.
MDR provider Blackpoint said in a report last month that one of its partners suffered a ransomware attack from Project Relic, which claims to have stolen over 400 GB of data from the client and demanded a ransom of 100 bitcoins (a bit less than $2 million) for decryption.
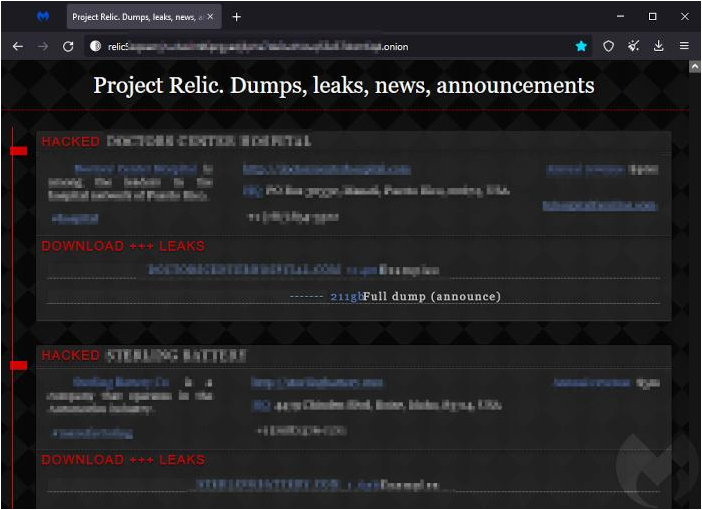
It appears there have been at least five victims of Project Relic so far, three of which are based in the United States.
Play ransomware
Over the past few weeks, more organizations in Europe and Asia have been targeted by a relatively new ransomware group named Play. While Play has been seen before and so is not a new player, it has started using the double-extortion tactic with a new dark web leak site.
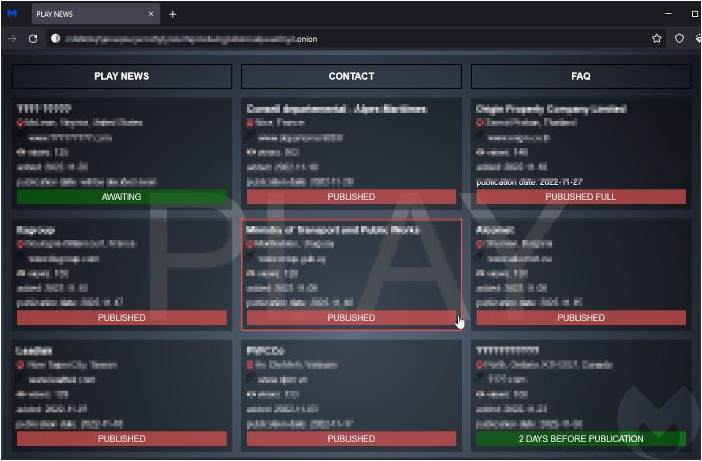
Play first attracted media attention a few months ago when it attacked Argentina’s Judiciary of Córdoba; this month, it added at least 11 more victims to its leak site. Play can be recognized by the .play extension it adds to encrypted files and a very simple ReadMe.txt ransom note which is only dropped at the root of the C: drive, that simply contains the word ‘play’ and a contact email address.
According to OriginalNetwork, Play gains initial access through valid accounts (VPN, exposed RDP, etc.) and by exploiting FortiOS vulnerabilities. It looks like Play ransomware specifically targets backup solutions as well in order to ensure that victims have no other option but to pay the ransom in order to recover the data.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.





