Ransomware is targeting vulnerable Microsoft Exchange servers
The Microsoft Exchange attacks using the ProxyLogon vulnerability, and previously associated with the dropping of malicious web shells, are taking on a ransomware twist. Until now, the name of the game has been compromise and data exfiltration, with a bit of cryptomining on the side.
To summarise: In ten days we’ve gone from “limited and targeted attacks” by a nation-state actor, to countless attacks by a number of groups against anyone with a vulnerable server. And in the space of a week the severity has escalated from unused web shells to ransomware. Depending on how the uptake in patching goes, this could well evolve again.
The danger of this pivot to ransomware is the sheer number of potential targets. Needless to say, it is essential that you install the Exchange updates required to keep your systems safe from harm.
The scale of the problem
Internet intelligence group Shadowserver has attempted to quantify the problem of exposed Exchange servers by scanning the Internet looking for vulnerable machines.
It has made two startling conclusions. The first is that as many as 68,500 servers may have been compromised by the so-called Hafnium threat actor before Microsoft released patches for its Exchange zero-days.
The total dataset distributed includes over 68500 distinct IP addresses. Of these IP addresses, there is high certainty that 8911 IP addresses were compromised. However, the remaining IP addresses included in the report are also very likely compromised too, since they were targeted with the OWA 0-day exploit before Microsoft publicly released patches for Exchange.
The groups second insight, is that at the time of its most recent scan, three days ago, 64,088 unique IP addresses were assessed as “still having exposed Microsoft Exchange Server vulnerabilities“. According to the group, the USA has by far the largest population of vulnerable servers, with almost 17,500.
The group’s research partner, the Dutch Institute for Vulnerability Disclosure, reported separately that nearly 20% of the 250,000 servers it scanned were vulnerable.
Which ever way you slice it, there are still a lot of vulnerable Exchange servers out there, and history suggests it will take a considerable time to patch them all.
With that out of the way: what, exactly, is the ransomware angle to this latest round of ProxyLogon attacks?
Introducing DearCry ransomware
Bad actors are now using Exchange exploits to gain entry to networks, before manually running DearCry ransomware.
This is an indicator of how easy Exchange exploitation is becoming. For years, targeted ransomware attacks have been synonymous with brute-force attacks on RDP ports. It’s such a common tactic, it’s easy to forget that criminals were simply using the easiest method of entry available.
The ransomware, first reported by BleepingComputer, has been dubbed “DearCry”. This is because it uses “DEARCRY!” as a file marker inside every encrypted file.
Malwarebytes and Microsoft have both independently confirmed that ProxyLogon is the entry vector for DearCry.
At the time of writing, it seems there is no way to decrypt the files without payment. As ever, prevention is better than cure, but if you are attacked successfully you’ll wish you’d secured your off-site backups and put a disaster recovery plan in place.
Once encryption takes place, the inevitable ransom note is deployed.
With backups and plans to restore them in place, victims can choose to ignore the attackers and carry on as normal. However, it is possible copies of the compromised files remain in the hands of the ransomware authors. This is how you get leaks further down the line.
According to the Bleeping Computer, a demand for $16,000 was made to one victim for the safe decryption of their files. There isn’t enough information available at this stage to determine if $16,000 is the going rate for DearCry attacks, or if there’s some variance to the amounts requested.
What’s certain is that other ransomware gangs will happily charge vastly greater sums, and if Exchange exploitation proves easier than RDP access, they will use it.
It’s time to update
If you haven’t already patched your systems, please do so right away and search your systems for signs of compromise.
Malwarebytes detects web shells planted on comprised Exchange servers as Backdoor.Hafnium. When the ransomware was still unknown, DearCry attacks would have been detected proactively as Malware.Ransom.Agent.Generic.
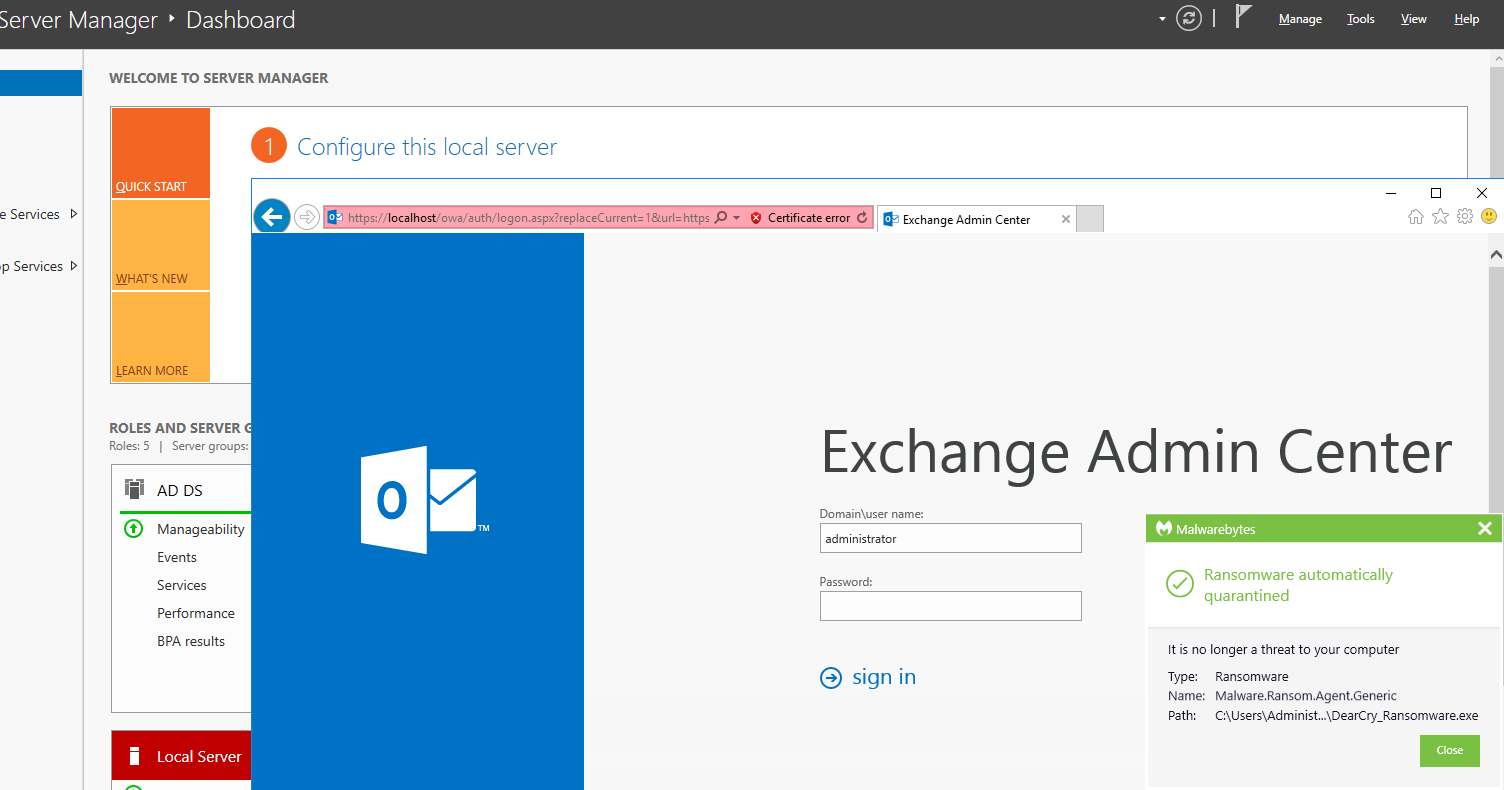
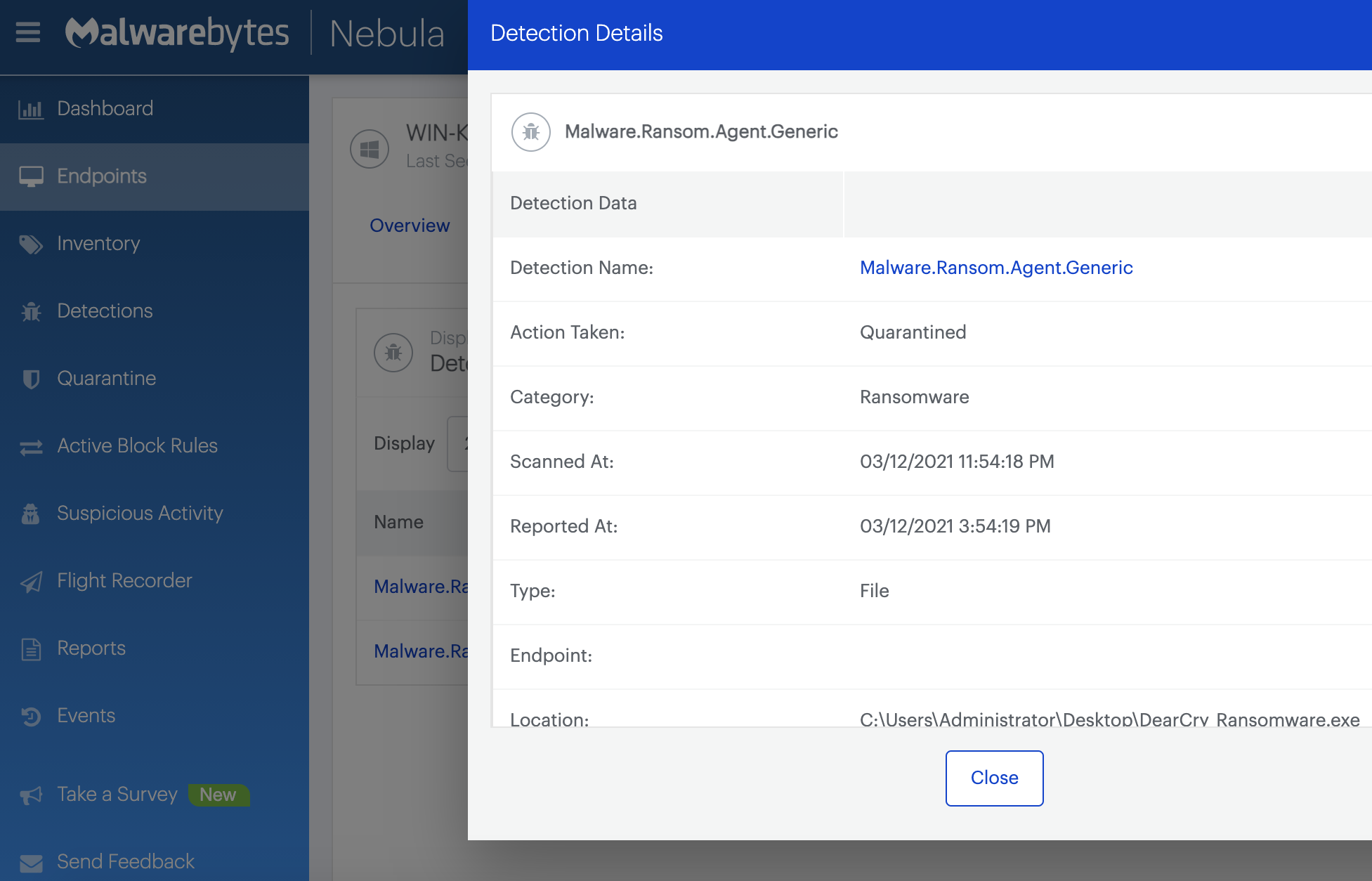
We’ll update the timeline in our first article on this topic as more developments and fresh information comes to light.
The post Ransomware is targeting vulnerable Microsoft Exchange servers appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


