Ransomware: May 2022 review
The Malwarebytes Threat Intelligence team monitors the threat landscape continuously and produces monthly ransomware reports based on a mixture of proprietary and open-source intelligence.
Conti sleight of hand?
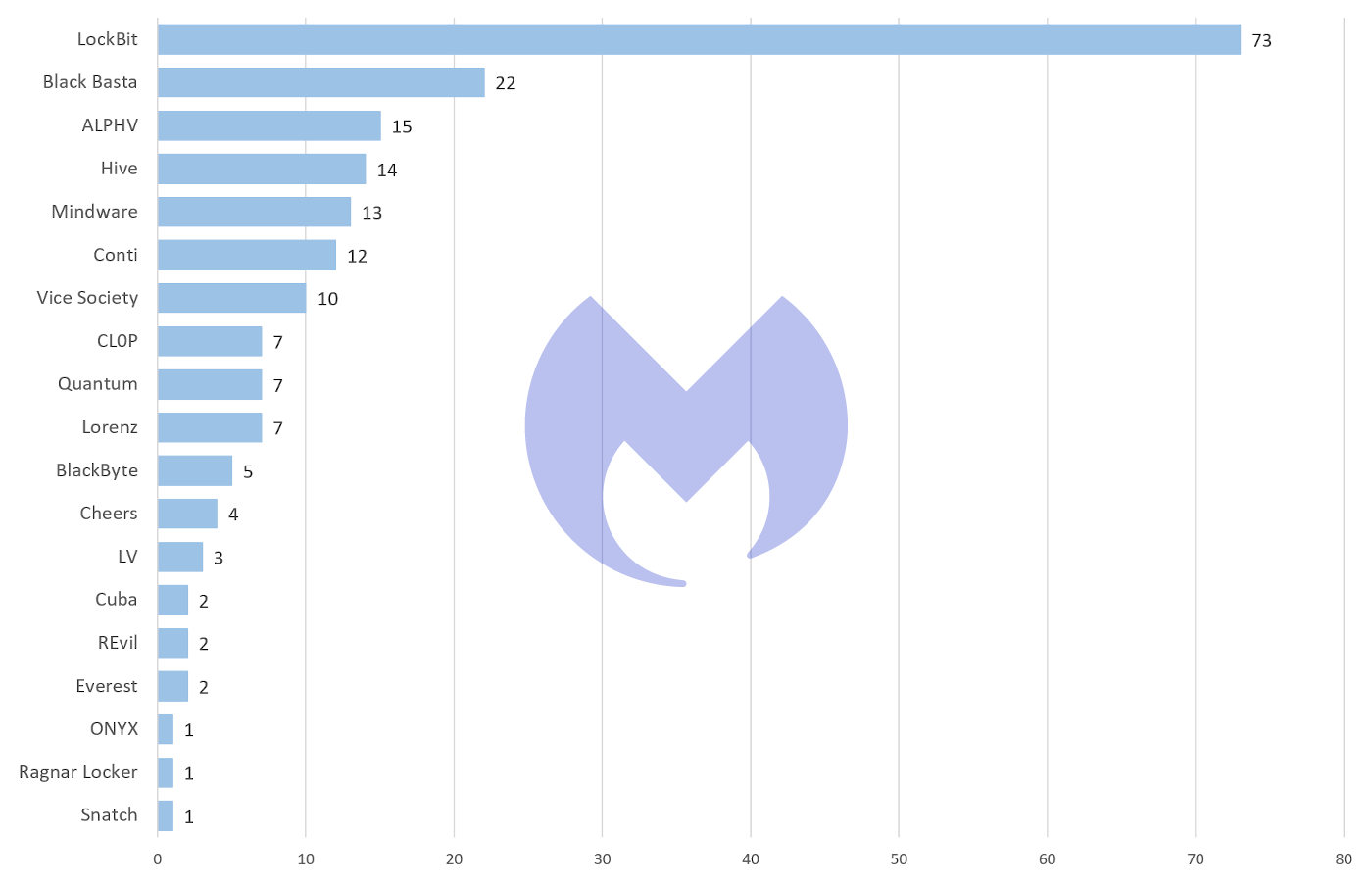
Although LockBit remained the most widely-deployed ransomware in May 2022, it was, typically, Conti that sucked all of the air out of the room.
Conti ransomware and the group that distributes it has been a dangerous, noisy presence in the ransomware ecosystem since 2020. It has been involved in hundreds of attacks, including the horrific disabling of Ireland’s Health Service Executive, and according to the FBI, it is “the costliest strain of ransomware ever documented”, having raked in over $150 million in ransom payments.
Recently, the group has had its troubles. On February 27, an individual with access to the group’s inner-workings started leaking a treasure trove of data that included source code, files, and tens of thousands of internal chat messages. Not long after, a hacking group began using the leaked source code to attack targets inside Russia, violating one of ransomware’s unspoken rules. And at the start of this month, the FBI put a $10 million bounty on the group’s head.
On May 8 the newly-inaugurated president of Costa Rica declared a national emergency across the country’s public sector, in response to the continuing effects of a devastating Conti ransomware attack carried out in April. On the same day, an inflammatory message appeared on the group’s leak site, alongside a leak of 672 GB of stolen data.
The message itself is the usual grandiose puffery: It took a swing at US President Joe Biden—”this old fool will soon die”, claimed the attack had been carried out by just two people, and threatened that Costa Rica was just a “Demo version” of what was to come.
You would be forgiven for thinking that despite recent travails, Conti is going strong.
But according to an in-depth analysis by Advintel though, that’s what it wants you to think. It says that far from being in rude health, the Conti brand is in the process of disbanding and that the attacks on Costa Rica were a deliberately showy act from an operation being run by a skeleton crew.
It seems that the decision to offer its “full support of Russian government” in February, following the invasion of Ukraine, may have been a fatal error. By aligning itself to the Russian state it had made ransom payments a potential sanctions violation, killing the group’s income.
Advintel asserts that as a result the Conti group has been “silently creating subdivisions that began operations before the start of the shutdown process.” These subdivisions—said to include KaraKurt, BlackByte, BlackBasta—are supposed to establish themselves before Conti disappears to avoid the kind of shallow and transparent rebrand some other groups have pursued.
Malwarebytes Threat Intel has been able to confirm that there was an internal announcement about the shutdown for affiliates, and that the group’s internal chat servers are down, although the leak site is still operational, and updated almost daily with additional data.
Ransomware attacks in May 2022
Malwarebytes Threat Intelligence builds a monthly picture of ransomware activity by monitoring the information published by ransomware gangs on their Dark Web leak sites. This information represents victims who were successfully attacked but opted not to pay a ransom.
In May, LockBit remained by far the most widely-used ransomware. Conti remained active, but its activity was significantly reduced compared to recent months. Notably, three of the four groups that have overtaken it—Black Basta, Hive, and ALPHV—are linked to the alleged Conti disbandment. Intriguingly, Hive was named as the ransomware used in an attack on Costa Rica’s national health service on May 31.
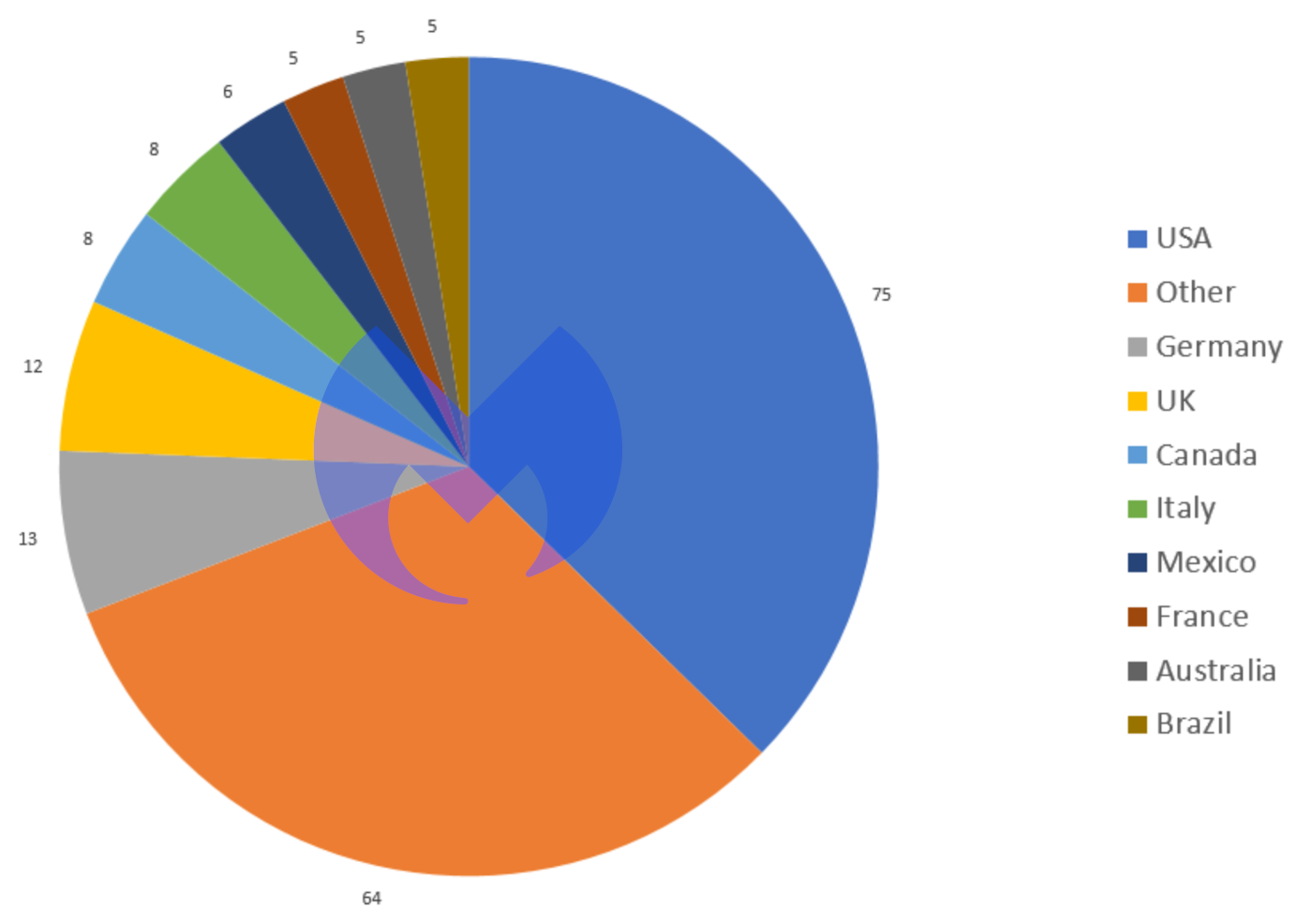
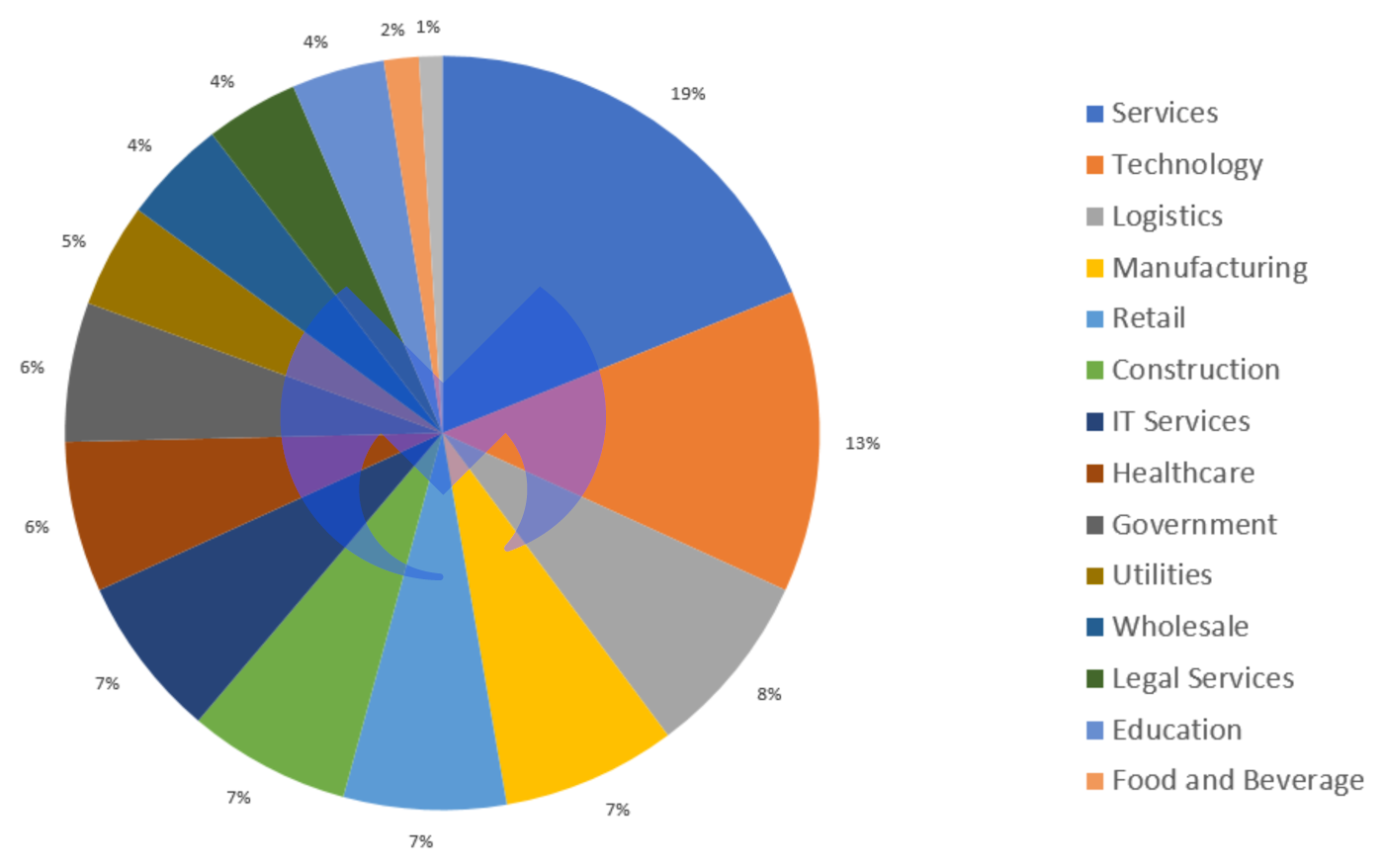
The USA remained far and away the country most badly affected by ransomware attacks in May, and services the industry sector more likely to be attacked.
Ransomware mitigations
Source: IC3.gov
- Implement regular backups of all data to be stored as air-gapped, password-protected copies offline. Ensure these copies are not accessible for modification or deletion from any system where the original data resides.
- Implement network segmentation, such that all machines on your network are not accessible from every other machine.
- Install and regularly update antivirus software on all hosts, and enable real-time detection.
- Install updates/patch operating systems, software, and firmware as soon as updates/patches are released.
- Review domain controllers, servers, workstations, and active directories for new or unrecognized user accounts.
- Audit user accounts with administrative privileges and configures access controls with the least privilege in mind. Do not give all users administrative privileges.
- Disable unused remote access/Remote Desktop Protocol (RDP) ports and monitor remote access/RDP logs for any unusual activity.
- Consider adding an email banner to emails received from outside your organization.
- Disable hyperlinks in received emails.
- Use double authentication when logging into accounts or services.
- Ensure routine auditing is conducted for all accounts.
- Ensure all the identified IOCs are input into the network SIEM for continuous monitoring and alerts.
How Malwarebytes protects against ransomware
Malwarebytes can protect systems against all ransomware variants in several ways.
The Malwarebytes Anti-Malware technology detects malicious files, browser modifications, and system modifications on Windows PCs using a combination of signature-based and signatureless technologies. This layer of protection detects the Ransomware binary itself. Detections can happen in real-time as the binary is run or the infection can be rooted out from an already-compromised machine by conducting a full system scan.
Anti-Ransomware is a signatureless technology in charge of monitoring system activity of processes against a certain subset of data in specific locations on the endpoint. Using patented technology, Anti-Ransomware assesses changes in those data files. If an internal scoring threshold is crossed by a monitored process, it triggers a detection from the Anti-Ransomware component.
For those already infected, Ransomware Rollback can help recover encrypted files within 72 hours of the attack. Rollback creates a local cache on the endpoint to store changes to files on the system. It can use this cache to help revert changes caused by a threat. The rollback feature is dependent on activity monitoring available in Malwarebytes Endpoint Detection and Response.
The post Ransomware: May 2022 review appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[INCRANSOM] - Ransomware Victim: State Bar of Texas (www[.]texasbar[.]com) 6 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)