Ransomware Payments Reached Record 11 Billion In 2023

Ransomware payments in 2023 soared above $1.1 billion for the first time, shattering previous records and reversing the decline seen in 2022, marking the year as an exceptionally profitable period for ransomware gangs.
The previous record-high figure was set in 2021, with ransomware payments amounting to $983 million, surpassing the preceding record of $905 million in 2020 by approximately 10%.
Unfortunately, the resurgence of ransomware in 2023 confirms that 2022 was a statistical anomaly, with that year’s activity impacted by geopolitical events like the war between Russia and Ukraine and law enforcement’s dismantling of the Hive operation.
According to a new Chainalysis report, the 2023 record can be attributed to escalating attacks against major institutions and critical infrastructure and Clop’s massive MOVEit campaign, which impacted thousands of organizations worldwide.
In July 2023, Chainalysis warned that based on the activity and recorded payments up until that time, ransomware payments were on a record-breaking trajectory, and unfortunately, the prediction was confirmed.
The most prolific threat groups in terms of ransom amounts they received in 2023, are ALPHV/Blackcat, Clop, Play, LockBit, BlackBasta, Royal, Ransomhouse, and Dark Angels.
However, the above groups achieved high payment volumes following different strategies:
- Lockbit has a moderate median payment size and frequency but has a large total ransom inflow.
- Clop and Dark Angels have larger median payment sizes but a lower frequency of payments.
- ALPHV/Blackcat has a high frequency and median payment size, with a substantial total ransom inflow.
- Phobos has a very high frequency of ransom payments but a lower median payment size.
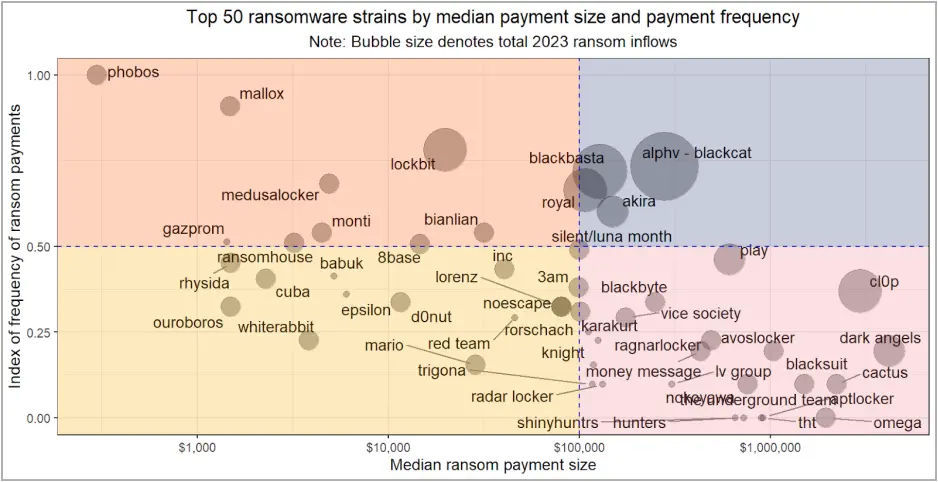
Source: Chainalysis
“Some strains, like Clop, exemplify the “big game hunting” strategy, carrying out fewer attacks than many other strains, but collecting large payments with each attack,” explains the report by Chainalysis.
“Clop leveraged zero-day vulnerabilities that allowed it to extort many large, deep-pocketed victims en masse, spurring the strain’s operators to embrace a strategy of data exfiltration rather than encryption.”
Ransomware groups are adapting to a decline in ransom payments by shifting towards “big game hunting,” which is the tactic of targeting very large companies who are more likely to pay large ransom demands rather than targeting many smaller companies for a higher number of small ransom payments.
Other ransomware gangs escalated their attack frequency to compensate for the reduced number of paying victims.
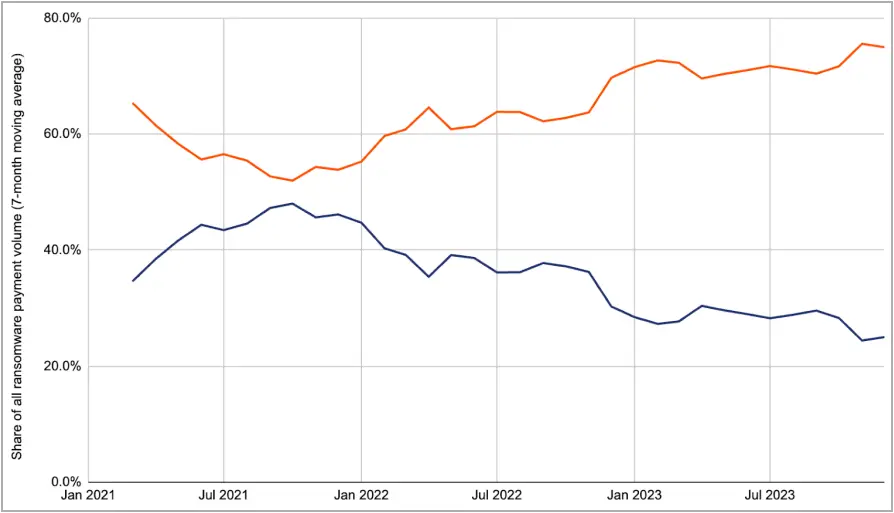
Source: Chainalysis
Regarding the laundering of ransom payments, Chainalysis says that in 2023, ransom payments were primarily passed through mixing services, underground exchanges, instant exchangers, sanctioned entities, and platforms that do not have know-your-customer (KYC) requirements in place.
This activity has led to increased law enforcement operations against rogue exchanges and mixers to prevent threat actors from laundering their illicit proceeds.
Coveware recently reported a steady decline in ransomware victims opting to give in to the blackmail and pay the cyber criminals. Still, Chainalysis’ stats show this may not be enough to tackle the problem.
On the contrary, ransomware operations can remain highly profitable as long as the number of attacks increases and large organizations continue to pay these more considerable ransom demands.
Overall, 2023 has been a good year for ransomware gangs despite attempts from law enforcement to disrupt their operations.
Hopefully, the trend of victims refusing to pay ransom will persist and potentially escalate this year, reaching a critical point where ransomware operations become financially unsustainable.
