Ransomware’s Russia problem
This blog post was written in collaboration with members of the Threat Intelligence Team.
Last week, US news outlet NBC News caused a stir with an article proclaiming that the REvil ransomware used in the recent, colossal Kaseya supply-chain attack was “written to avoid computers that use Russian.”
The attack, one of the largest and most dramatic ransomware attacks in history, happened at a time when the Biden administration was escalating its rhetoric over Russian cyber-activity. To the uninitiated, and the NBC headline writer, it looked like a “new revelation.” Readers were invited to join the geopolitical dots.
But the stir it caused, at least among those familiar with ransomware, wasn’t surprise that REvil was coded to avoid Russia, but surprise that anybody would be surprised by that. TrustWave, authors of the the report the article was based on, certainly weren’t surprised that REvil didn’t want to run in Russia. They give it barely a mention.
Ransomware really caught the world’s attention in May when threat actors using DarkSide ransomware kicked the hornet’s nest by attacking the Colonial Pipeline, the largest fuel pipeline in the US. But as many readers will know, ransomware attacks have been relentless over the past few years, escalating each year. Even a global pandemic didn’t hamper the ransomware gangs’ activities, and just this year targets have included countless private companies, as well as hospitals, law enforcement agencies, governments, charities, and critical infrastructure.
There are multiple groups creating and developing different strains of ransomware—and many more affiliates enticed to use it to conduct their own attacks. Although their attacks follow similar patterns, there is constant innovation of tools, tactics and technology. And while some groups are cooperating, more or less, others work alone.
Yet, they all of them have one thing in common: Ransomware really, really doesn’t want to run in Russia or members of the Commonwealth of Independent States (CIS), and it never has.
Russia-averse ransomware families
The Commonwealth of Independent States (CIS, for short, or Sodruzhestvo Nezavisimykh Gosudarstv in Russian), is an international organization comprised of Russia and other republics that used to be part of the Soviet Union. Armenia, Azerbaijan, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, and Uzbekistan are member states of CIS. The two founding states, Ukraine and Turkmenistan, are allowed to participate in CIS although they are not recognized as official members.
Malwarebytes researchers have compiled a list of the most prolific ransomware families based on the number of known attacks in the first half of 2021 (this does not include the cascading Kaseya attack from July) and whether or not that ransomware will run in the CIS. None of them do. Almost anything is fair game for ransomware gangs it seems, unless it happens to be located in the CIS.
| Ransomware family | Known attacks in 2021† | Currently Active? | Runs in the CIS? |
|---|---|---|---|
| Conti (215) | 215 | Yes | No |
| Avaddon (161) | 161 | No | No |
| REvil (116) | 116 | No | No |
| DarkSide (75) | 75 | No | No |
| PYSA (68) | 68 | Yes | No |
| DoppelPaymer (60) | 60 | Yes | No |
| CL0P (44) | 44 | Yes | No |
| Babuk Locker (43) | 43 | Yes | No |
| RagnarLocker (30) | 30 | Yes | No |
| NetWalker (22) | 22 | Yes | No |
| Nefilim (17) | 17 | Yes | No |
| RansomEXX (14) | 14 | Yes | No |
| Mount Locker (8) | 8 | Yes | No |
Among the 13 ransomware families listed in the table, 10 are known to be active. Avaddon and DarkSide seem to have been disrupted by law enforcement agencies. The CL0P money laundering operation was raided in June but attacks involving that ransomware have continued. The group behind Babuk Loader recently announced it was quitting the ransomware encryption scene but its ransomware builder later emerged on VirusTotal, and ransomware built with it has since been used in attacks. Following the enormous Kaseya attack, the websites and infrastructure of the REvil ransomware group have been shut down. Despite rampant speculation, the cause is unknown.
How ransomware avoids CIS countries
There are a number of techniques that ransomware creators commonly use and include in their code to avoid CIS countries, such as hard-coding country names and geographical territories, and checking the system language.
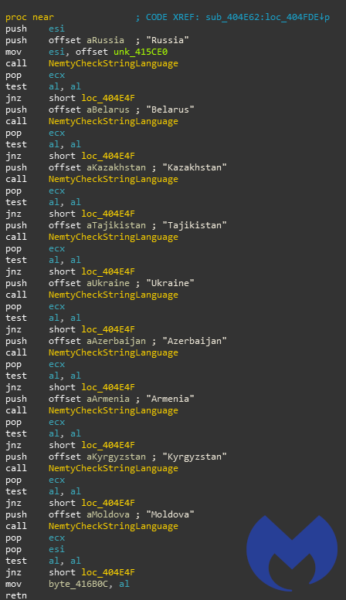
Some threat actors include code to check for the default system language by, for example, calling the GetUserDefaultLangID or GetLocaleInfoW functions, which return a language particular to a user—American English, for example. Another checking process retrieves the victim’s IP address via a public API, such as api.ipify.org. Because IP addresses are allocated geographically they can be used to guess the user’s rough location.
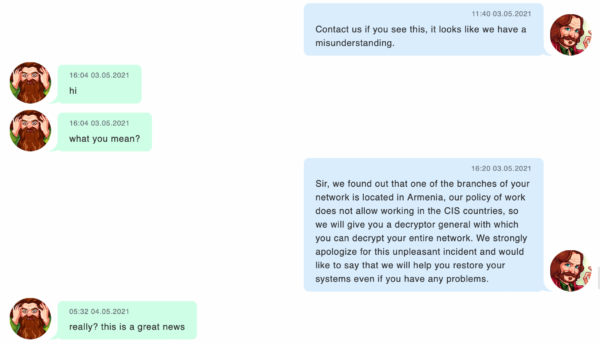
Although ransomware tries very hard not to run in Russia or the CIS, sometimes it does. Where ransomware has netted systems in those countries by accident the attackers have been known to hand over decryptor keys and apologize for the error.
On rare occasions threat actors have also chosen to avoid other targets based on the country they’re in. Famously, a Syrian father took to Twitter to plead with Coveware to mediate between him and GandCrab ransomware operators, to let him see his boys again. In an underground forum post, GandCrab threat actors decided to release decryption keys to anyone else affected by their attack in Syria. They also stated that not including Syria in the list of countries to avoid was a mistake. Their benevolence was patchy though, and targets outside Syria, including hospitals, were still considered fair game.
Why does ransomware avoid Russia?
So what’s behind ransomware’s keenness to avoid attacks inside the CIS? Although it’s possible that some ransomware gangs operate with the active cooperation of the Russian state, that isn’t the prevailing view.
The Biden administration, and many security professionals, believe that ransomware gangs are either operating with Russia’s blessing or that the country is turning a blind eye. Ransomware gangs don’t expect to face any penalty from inside the CIS, provided they avoid attacking its organizations. And since Russia has no extradition treaty with the US, the gangs operating there are also unreachable and untouchable by US law enforcement.
Put simply, ransomware is a low risk, high reward form of cybercrime, if you avoid the CIS.
The mood music is changing though, and efforts to increase the risks criminals face are underway. Even before the Colonial Pipeline attack in April, US government officials and cybersecurity experts were beginning to talk about ransomware as a threat to national security.
“Those behind these malicious activities should be held accountable for their actions. That includes governments that do not use the full extent of their authority to stop the culprits,” says Homeland Security Secretary Alejandro Mayorkas in a speech he gave on March 31.
This sentiment is also echoed by the Ransomware Task Force (RTF), a group of expert volunteers tasked with tackling the ransomware problem and finding ways to disrupt it. In its April report [PDF], the RTF urged the US government to spearhead international coordination efforts to tackle the global problem of ransomware. Among a host of recommendations, it also suggested that ransomware be viewed as a threat to national security, and that the Racketeer Influenced and Corrupt Organizations Act, otherwise known as the RICO Act, be expanded to include ransomware gangs.
On several occasions, the Biden administration has indicated it intends to aggressively go after ransomware gangs. This includes treating, investigating, and prosecuting ransomware attacks as if they were terrorism. Involving the military is also being carefully considered, according to Commerce Secretary Gina Raimondo. Meanwhile, General Secretary of Nato Jens Stoltenberg told BBC Newsnight that the organization could respond to cyberattacks with military force “by air, sea, or land.”
Don’t invest in Russian keyboards
Regardless of whether ransomware—or any malware, for that matter—checks to see if its victim is in a CIS or CIS-affiliated state or not, it is worth remembering that the “big game” attacks they are used in are not automated. A level of human involvement is part of the modus operandi.
So, before you think about buying Russian keyboards, installing Russian language packs, or other weird tricks, realize that by the time a ransomware operator has put themselves in a position to attack you, they know a lot about you and your business, such as where your main HQ and satellite offices are. Trying to convince them otherwise—at any point, really—is a bit ridiculous, impractical, and a waste of effort.
Perhaps Fabian Woser, chief technology officer of Emsisoft, said it best:
Our advice: Avoid weird tricks. There is no substitute for a robust strategy of defense in depth.
The post Ransomware’s Russia problem appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


