Rapid7 Labs’ 2020 Naughty List Summary Report to Santa

As requested, your dutiful elves here at Rapid7 Labs have compiled a list of the naughty country networks being used to launch cyberattacks across the globe. Needless to say, some source networks have been very naughty (dare we use the word “again,” since these all seem to be repeat offenders).
To make it easier to digest, we’ve broken the list out into three categories:
- Naughty Microsoft SQL Server attacks
- Naughty Microsoft Remote Desktop Protocol (RDP) attacks
- Naughty Microsoft SMB attacks
These are focused on the top offenders for the last half of the year, and provide a smoothed trending view (vs. discrete daily counts) in each one to help you make your Naughty/Nice inclusion decisions.
Naughty Microsoft SQL server attacks
Hopefully you do not maintain your lists on publicly accessible Microsoft SQL servers, as they are regular targets for attackers who have their evil designs on them, with a major focus on using them for cryptocurrency mining this year.
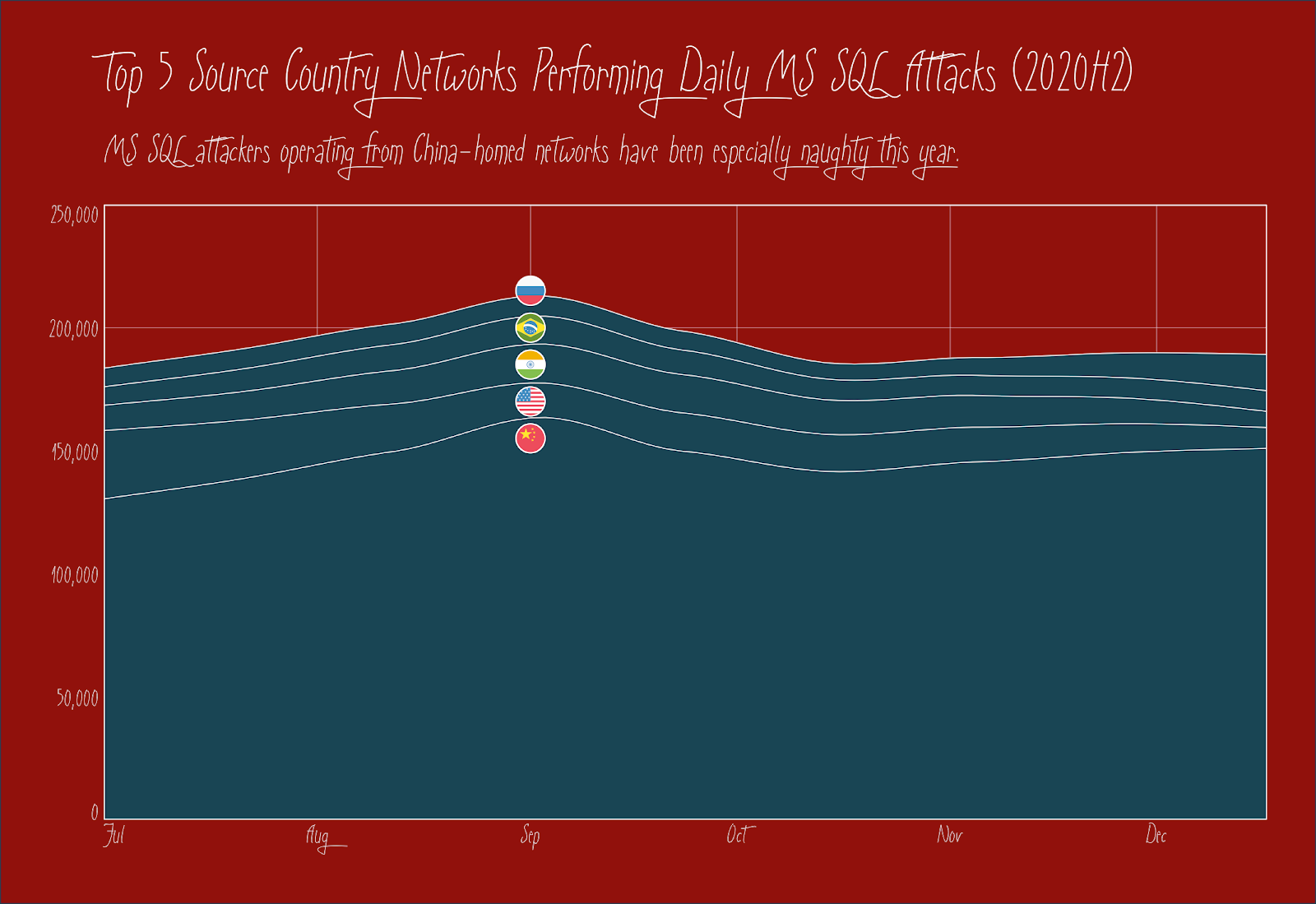
| Source Country Network | Median Daily MSSQL Attack Interactions |
|---|---|
| China | 147,677 |
| United States | 12,984 |
| India | 7,159 |
| Brazil | 8,984 |
| Russia | 7,031 |
A massive botnet operating from before the fall of 2019 and early 2020 abruptly stopped operations just before summer, and MS SQL server credential and query attack types have leveled off to previous baseline levels. The enduring lesson from measuring these interactions is for all the grown-up kids out there to never, ever put any database like MS SQL on the public internet. Unfortunately, you can read an excerpt from our other report that found nearly 100,000 of them earlier this year (perhaps the offenders on that list would be better placed on the naughty list?).
Naughty Microsoft Remote Desktop Protocol (RDP) attacks
We were sorry to hear that even your own factory had to observe remote-work protocols starting in March, but we hope your IT department did not have to resort to enabling direct Microsoft Remote Desktop Protocol (RDP) access, since it has been the target of a massive increase in discovery and credential stuffing attacks the last quarter of this year.
| Source Country Network | Median Daily RDP Attack Interactions |
|---|---|
| Russia | 41,515 |
| United Kingdom | 23,337 |
| United States | 32,840 |
| Germany | 2,832 |
| France | 12,802 |
Naughty traffic levels started just before the presidential election in the United States and further increased in size toward the end of the year.
RDP-targeted ransomware has been a fairly huge problem this year, with many nefarious attackers setting their sights on overworked and under-resourced healthcare, education, and municipal targets.
It might be worth taking some time to remind your elves in IT that it’s not a good idea to put RDP services directly on the internet. While another of our reports earlier this year did not find any RDP nodes coming from the North Pole autonomous system, it is possible we didn’t inventory your network on a day they did. As you know, it’s best to put RDP servers behind a dedicated (and properly configured) Microsoft RDP Gateway server or—better yet—a multifactor virtual private network (VPN).
The majority of the malicious RDP traffic coming from the U.K., U.S., and Germany appear to be the work of one or two groups who should also be considered candidates for the naughty list.
Naughty Microsoft SMB attacks
| Source Country Network | Median Daily SMB Attack Interactions |
|---|---|
| Vietnam | 4,206,475 |
| India | 2,137,146 |
| Russia | 2,055,072 |
| Brazil | 1,478,000 |
| Indonesia | 1,420,109 |
Last, we lament the need to report a renewed uptick in EternalBlue-infused attacks against internet-accessible Microsoft SMB servers. The vast majority of source nodes involved with these attacks are part of the various Mirai-like botnets that use both traditional compromised server hosts and (mostly) “internet of things” devices such as cameras, DVRs, and other business and home automation devices to coordinate and orchestrate attacks.
Might we be so bold as to suggest that you hold off—at least this year—distributing rebranded white-box electronics components to the folks on the Nice list? If you do insist on giving out home automation presents this year, please make sure the programmer elves follow the guidance in the IoT Security Foundation’s Security Compliance Framework to guard against adding more nodes to these naughty botnets.
If you’re wondering why attackers are still looking for SMB servers, you can see for yourself that there are still hundreds of thousands of them out on the internet to connect to. We’re just glad you switched to using a secure file transfer service to exchange documents (like this one!) with all your partner elves.
Glad tidings `til next year!
We hope you, Mrs. Claus, the elves and all the reindeer stay safe and socially distanced. We’ll make sure to leave the cookies and bourbon milk in the usual place.
Happy Holidays from all the Elves in Rapid7 Labs!
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


