RDP brute force attacks explained
While you read these words, the chances are that somebody, somewhere, is trying to break in to your computer by guessing your password. If your computer is connected to the Internet it can be found, quickly, and if it can be found, somebody will try to break in.
And it isn’t like the movies. The criminal hacker trying to guess your password isn’t sat in a darkened room wondering which of your pets’ names to type on their keyboard. The hacker’s at lunch and they’ve left a computer program churning away, relentlessly trying every password it can think of. And computers can think of a lot of passwords.
Oh, and there are lots of hackers out there and they don’t take turns trying to break into your computer one at a time. They’re all trying to break in separately, all at the same time.
While there are lots of ways to break into a computer that’s connected to the Internet, one of the most popular targets is the Remote Desktop Protocol (RDP), a feature of Microsoft Windows that allows somebody to use it remotely. It’s a front door to your computer that can be opened from the Internet by anyone with the right password.
RDP explained
RDP is an immensely useful feature: Remote workers can use it to log in to computers physically located at their office buildings, and IT experts can use it to fix somebody’s computer from anywhere in the world. However, that ability to log in to a computer from anywhere in the world also makes RDP an immensely attractive target for criminal hackers looking to steal data or spread malware.
To log in to a computer using RDP, users simply type in the Internet address a computer running and enter their username and password. Then they can use it as if it was on the desk in front of them. It’s that simple.
Reading that you might think that you’re safe as long as nobody knows your computer’s address. Unfortunately, your computer’s address isn’t a secret, even if you’ve never told anyone what it is.
Internet addresses (IP addresses) are just sequences of numbers, so it’s easy to create computer programs that guess all the possible IP addresses in existence and then quickly visit them to see if they belong to Windows computers with RDP switched on, over and over again. And if that’s too much work, there are websites like Shodan that can do it for them.
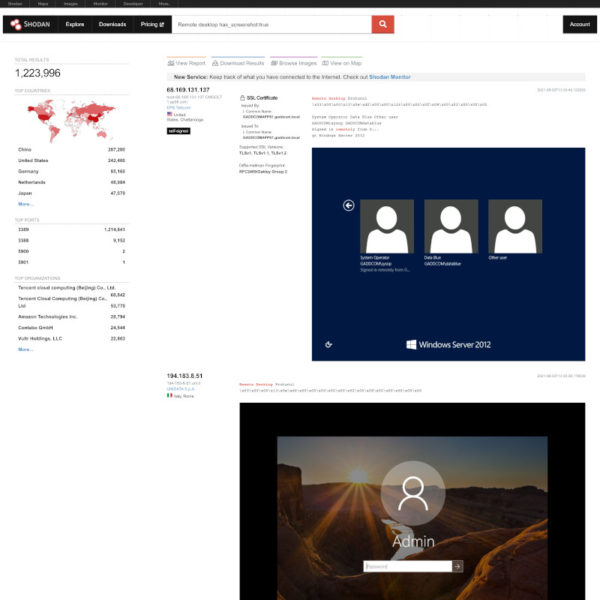
Searches like this make it easy for hackers to find the computers they want to target, but they don’t help them break in. To do that they will need to guess a password successfully.
Brute force guessing explained
Hackers figure out RDP passwords using a technique called “brute force guessing,” which is as basic as it sounds. They simply use a computer program that will try a password and see if it works. If it doesn’t, it will try another, and another, and another, until it guesses a password correctly or decides it’s time to try its list of passwords on a different computer. The guesses aren’t random. Some passwords are far more popular than others, so criminals use lists of the most commonly used passwords, starting with the most popular.
Unfortunately, weak passwords are extremely common. In fact, they’re so common that there is an entire criminal industry dedicated to guessing RDP passwords. Often, the hackers that guess the passwords don’t actually use them. Instead, they sell them on the Dark Web to other criminals, at an average price of just $3 per account.
Imagine how many $3 passwords a hacker has to sell to make it pay its way and you’ll get a sense for how big this problem is.
There are numerous groups scanning the Internet and trying to guess RDP passwords. Some hang around, making tens of thousands of guesses at the same computer, while others will try just a few guesses before moving on to another target. At any one time your computer might have the attention of multiple groups, all employing slightly different tactics to guess your password. And they never get bored. Even if they appear to give up, they’ll return later, to see if anything has changed or to try something new.
Before the COVID-19 pandemic, RDP was already the go-to method for spreading ransomware, and it had been for several years. Because of that, I co-authored some research into RDP brute force attacks in 2019. Our research was simple: We connected some Windows computers to the Internet, turned on RDP, and waited to see what happened.
We didn’t have to wait long. Hackers started trying to guess our test computers’ passwords within 90 seconds of them being attached to the Internet. Over the course of a month our test computers were probed with password attempts all day, every day, 600 times an hour.
And that was before things got really serious, in 2020.
The pandemic triggered a huge surge in the number of people working from home. In turn, that triggered a surge in the number of people relying on RDP. Because guessing RDP credentials and selling them was already a viable underground business, the criminal infrastructure to take advantage of remote workers was already in place. The result was a colossal increase in the number of attacks on computers running RDP.
Stopping RDP brute force attacks
RDP brute force attacks represent a serious, on-going danger to Internet-connected Windows computers. However, there are a number of ways to protect yourself against them. As in all areas of computer security, defence in depth is the best approach, so aim to do as many things on this list as you reasonably can.
- Turn it off. The simplest way to protect yourself from RDP brute force attacks is to just turn off RDP permanently, if you don’t need it.
- Use a strong password. Brute force attacks exploit weak passwords so in theory a strong password is enough to keep attackers out. In practice, users often overestimate how strong their passwords are, and even technically strong passwords can be rendered useless if they are stolen or leaked. For those and other reasons it’s best to use at least one of the other methods in this list too.
- Use a VPN. RDP can be protected from brute force attacks by forcing users connect to it over a Virtual Private Network (VPN). This hides RDP from the Internet but exposes the VPN, leaving it vulnerable to attack, so it also needs to be properly secured. This is the approach taken by a lot of organizations, but is likely to be beyond the patience or technical ability of many home users.
- Use multi-factor authentication (MFA). MFA forces users to provide multiple forms of authentication in order to log in, such as a password and a one-time code from an app. MFA offers very strong protection because even if an attacker guesses a password, it isn’t enough to give them access. Like VPNs, MFA solutions can be complex and are often aimed at business users.
- Limit the number of guesses. The simplest way to lock out brute force attackers is to limit the number of password guesses they can make. If a legitimate user gets their password wrong, they normally only need a few extra guesses to get it right. There is no need to give somebody the luxury of making tens- or hundreds-of-thousands of guesses if you only need a handful. Locking out users who make too many wrong guesses, or limiting the number of guesses users can make has the effect of making weak passwords much, much stronger. (It’s how bank cards and smartphones get away with using simple four- or six-digit PINs to protect themselves.)
The post RDP brute force attacks explained appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



