Researchers Monitor Rise Of An Infostealer Dubbed As ‘Poulight’ That Most Likely Has A Russian Origin
In times where info-stealer is progressively becoming one of the most common threats, the Infostealer market has thus risen as one of the most lucrative for cyber crooks, for the data gathered from infected frameworks could be ‘resold’ in the cybercrime underground or utilized for credential stuffing attacks.
This class of malware is said to incorporate many well-known malware like Azorult, Tesla, and Hawkeye.
Recently over the two months, Researchers from Cybaze-Yoroi ZLab observed the evolution and the diffusion of an info stealer dubbed as Poulight that most probably has a Russian origin. First spotted by MalwareBytes specialists in middle March and indicators of compromise have been as of now shared among the security community.
The vindictive code has propelled further stealing capabilities and continues to evolve.
Hash 8ef7b98e2fc129f59dd8f23d324df1f92277fcc16da362918655a1115c74ab95
Threat Poulight Stealer
Brief Description Poulight Stealer
Ssdeep 1536:GJv5McKmdnrc4TXNGx1vZD8qlCGrUZ5Bx5M9D7wOHUN4ZKNJH: GJeunoMXNQC+E5B/MuO0Ogt
Above is the sample information / Technical Analysis
Like a large portion of the malware of this particular family, it is created from a builder accessible to cyber-criminal groups that offer a ‘subscription plan’ for its “product”. The outcome is a .NET executable:
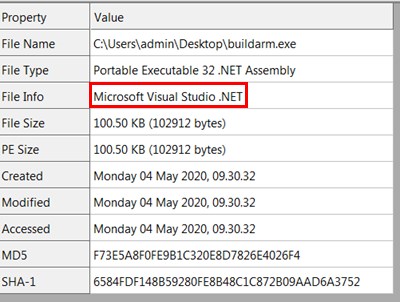 |
| Static information about the binary file |
A quirk of this sample is that it doesn’t have a minimal indication of obscurity; the analysis is very simple to depict the malware abilities/capabilities. When the malware is propelled, it plays out a classical evasion technique (as shown in Fig.3):
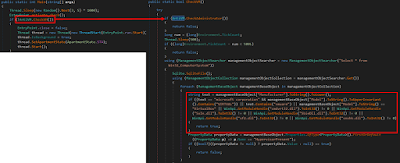 |
| Figure 3: Evasion Technique |
This implemented evasion technique is one of the most exemplary ones, where, through the utilization of Windows Management Instrumentation (WMI) by executing the inquiry “Select * from Win32_ComputerSystem”. Specifically, along these lines, a few checks of the most relevant tracks of virtualization are given, as:
• “vmware”
• “VIRTUAL”
• “VirtualBox”
• “sbiedll.dll” (Sandboxie)
• “snxhk.dll” (Avast sandbox)
• “SxIn.dll” (Avast sandbox)
• “Sf2.dll” (Avast Sandbox”)
These checks are additionally recorded from the Al-Khaser or Pafish tools which are planned to be a test suite to distinguish malware analysis environments and intended to test the strength of the sandboxes. At that point, the malware can continue with the infection beginning giving rise to another threat called “Starter”.
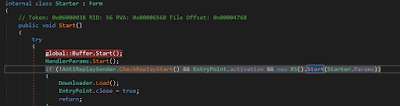 |
| Figure 4: Loader module of the malware |
The “Starter” class contains the routine to load the segments of the malware. Prior to that, there is the initialization of certain directories and files utilized to store the accumulated data from the victim machine. This activity is performed by the primary instruction “global:: Buffer.Start()”, the method is very simple and easy: a series of folders were created within Windows Special folders (AppData, Local AppData, Personal, Desktop) along these lines:
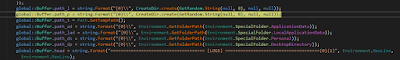 |
| Figure 5: Creation of folders in the Windows Special Folders |
From that point forward, the malware extracts the configuration document and its parameters from the asset named “String0”, a Base64 encoded string and through the following strategy they are then decoded:
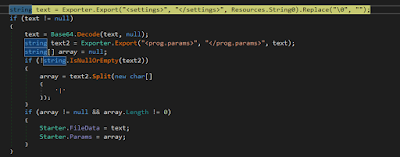 |
| Figure 6: Routine to extract the configuration file |
The primary data tag “prog.params” is quickly recovered in the instruction “HandlerParams.Start()” which can be seen in Figure 4. Presently, a check of a previous infection is performed before beginning another one. The instruction “AntiReplaySender.CheckReplayStart()” (in figure 4) is assigned.
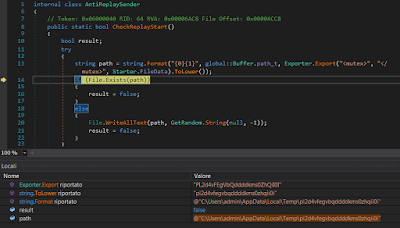 |
| Figure 7: Check of a previous infection |
The malware attempts to discover the id of the mutex. In the event that the file is available, the malware doesn’t execute itself some other time, else it composes this empty document to sign the infection is begun. From that point forward, it transforms into the real vindictive main contained inside the “XS” class, as seen in figure 4. The primary bit of the code is the following:
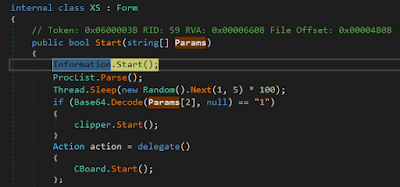 |
| Figure 8: Initialization of the mail module |
The first instruction is “Information.Start()” where all the data about the hardware and software of the host is collected along these lines:
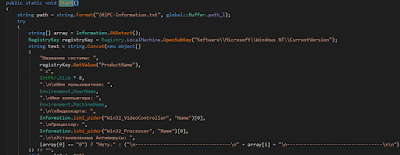 |
| Figure 9: Routine for retrieving the configuration of the victim machine |
It is clearly evident that the malware utilizes both English and Russian dialects to log the data assembled. From that point onward, the stealer turns to count and log all the active processes inside the operative system.
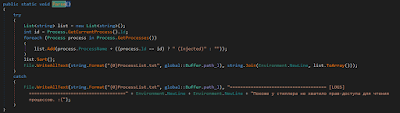 |
| Figure 10: Routine to extract the process list |
Now as seen in figure 8, a ‘check’ on the third parameter is performed. On the off chance that it is equivalent to one; the “clippers” module is executed.
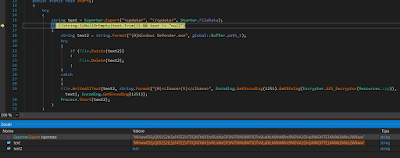 |
| Figure 11: Routine to decode and execute an embedded component |
As show in the above figure, this code can decode a component contained inside the “clbase” tag with the AES key stored within the “update” tag. Be that as it may, in the particular configuration there is no “clbase” field, so we don’t have any other component to install. The last instruction seen in Figure 8 is “CBoard.Start”, which works in the following way:
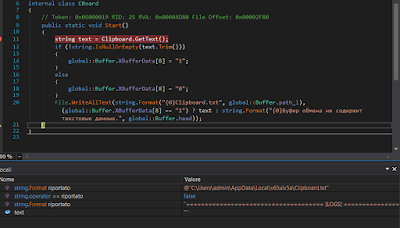 |
| Figure 12: Routine to steal clipboard data |
The subsequent stage is to accumulate all the sensitive data on the victim machine:
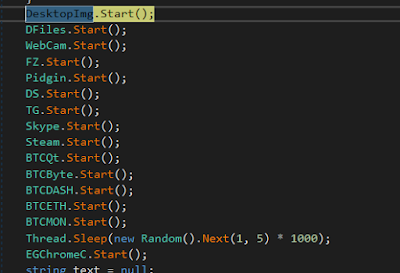 |
| Figure 14: Detail of the stealing modules |
The malware steals an immense amount of data:
- Desktop Snapshot
- Sensitive Documents
- Webcam snapshot
- Filezilla credentials
- Pidgin credentials
- Discord Credentials
- Telegram
- Skype
- Steam
- Crypto Currencies
- Chrome chronology
The most fascinating part is that the module “DFiles” instructed to steal sensitive documents. It begins with looking through the records with one of the accompanying extensions:
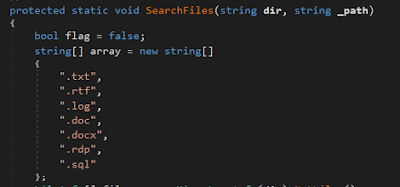 |
| Figure 15: Routine to search the documents with specific extensions |
Within the gathered files, the malware searches for the classic keywords showing that the content of the files conserves some valuable accreditations. The keywords are the accompanying:
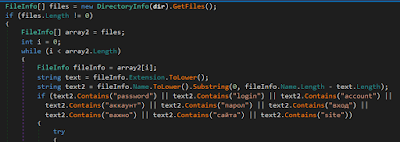 |
| Figure 16: List of keywords searched within the documents |
Then the malware proceeds to gather all the data inside a unique data structure and sends it to the C2 retrieved in another resource named “connect”:
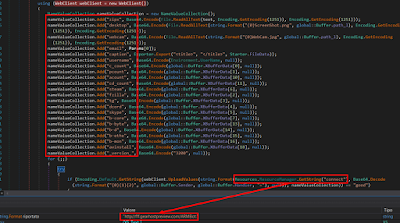 |
| Figure 17: Routine to upload to the C2 the stolen information |
At long last, it downloads and executes various components from the Internet. The parameters are recovered similarly observed in the past segment: a tag named “file” contains the component to download.
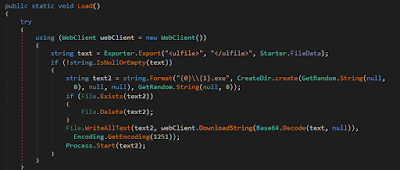 |
| Figure 18: Routine to download other components from the Internet |
Thus there is no doubt in the fact that Poulight stealer has a mind-boggling potential to steal delicate data and it ought not to be disregarded that later on, it may supplant other info stealers like Agent Tesla, remcos, etc.
In any case, the limitation of the embed is the absence of code obfuscation and data protection, however, this could be clarified due to the fact that, possibly, the malware is in its early stages of development.
Since now that the attackers likely will enhance these features, therefore, being aware of them is the best step forward for the users now. RN


