Rhysida ransomware behind recent attacks on healthcare

The Rhysida ransomware operation is making a name for itself after a wave of attacks on healthcare organizations has forced government agencies and cybersecurity companies to pay closer attention to its operations.
Following a security bulletin by the U.S. Department of Health and Human Services (HHS), CheckPoint, Cisco Talos, and Trend Micro have all released reports on Rhysida, focusing on different aspects of the threat actor’s operations.
Previously, in June, Rhysida drew attention for the first time after leaking documents stolen from the Chilean Army (Ejército de Chile) on its data leak site.
At the time, a preliminary analysis of the Rhysida encryptor by SentinelOne showed that the ransomware was in early development, missing standard features seen in most strains like persistence mechanisms, Volume Shadow Copy wiping, process termination, etc.
“This is an automated alert from cybersecurity team Rhysida,” reads the Rhysida ransom note.
“An unfortunate situation has arisen – your digital ecosystem has been compromised, and a substantial amount of confidential data has been exfiltrated from your network.”

Source: BleepingComputer
Rhysida targets healthcare orgs
While some ransomware operations claim not to intentionally target healthcare organizations and even provide free decryption keys if done by mistake, Rhysida does not appear to follow the same policy.
The Rhysida dark web data leak site lists a healthcare organization in Australia, giving them a week to pay a ransom before the stolen data is leaked.
Source: BleepingComputer
A bulletin published by the U.S. Department of Health and Human Services (HHS) last week warned that while Rhysida still uses an elementary locker, the scale of its activities has grown to dangerous proportions, and recently, the threat actors demonstrated a focus on the healthcare and public sector.
“Its victims are distributed throughout several countries across Western Europe, North, South America, and Australia,” reads HHS’s bulletin.
“They primarily attack education, government, manufacturing, and technology and managed service provider sectors; however, there has been recent attacks against the Healthcare and Public Health (HPH) sector.”
Sources have told BleepingComputer that Rhysida is behind a recent cyberattack on Prospect Medical Holdings, which still experiences a system-wide outage impacting 17 hospitals and 166 clinics across the United States.
However, Rhysida has not taken responsibility for the attack yet, and PMH has not responded to emails on whether the ransomware gang is behind the attack.
If you have first-hand information about this or other unreported cyberattacks, you can confidentially contact us on Signal at +16469613731.
A Trend Micro report released today focuses on the most commonly observed Rhysida attack chain, explaining that the threat group uses phishing emails to achieve initial access, then deploys Cobalt Strike and PowerShell scripts, and eventually drops the locker.
An interesting observation from Trend Micro’s analysts is that the PowerShell scripts used by Rhysida operators terminate AV processes, delete shadow copies, and modify RDP configurations, indicating the locker’s active development.
A ransomware encryptor itself usually handles these tasks, but for the Rhysida operation, they use external scripts to achieve the same purposes.
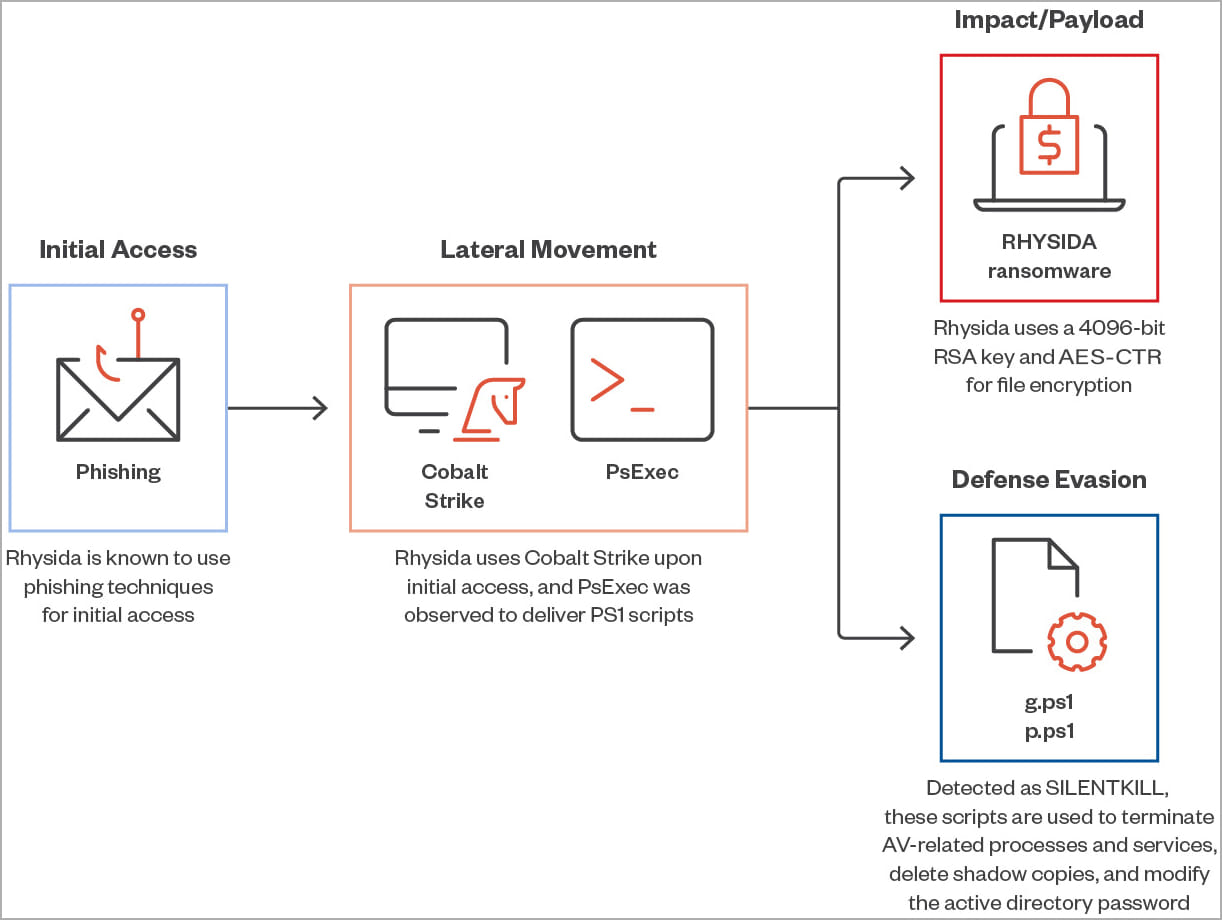
Cisco Talos’ report confirms that the most recent Rhysida locker uses a 4096-bit RSA key with the ChaCha20 algorithm for file encryption and now excludes several directories as well as the following filetypes:
.bat .bin .cab .cmd .com .cur .diagcab .diagcfg, .diagpkg .drv .dll .exe .hlp .hta .ico .lnk .msi .ocx .ps1 .psm1 .scr .sys .ini thumbs .db .url .iso and .cab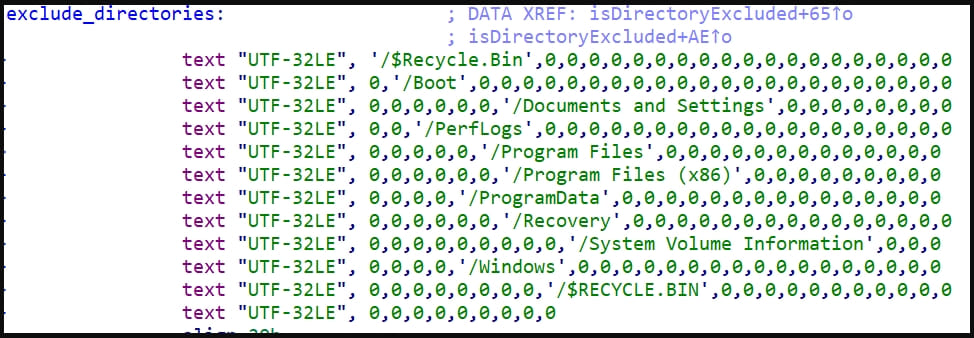
Source: Cisco
CheckPoint’s report goes a step further, linking Rhysida to the now-defunct Vice Society ransomware operation, based on the victim publishing times on the two extortion sites and their similar victim targeting patterns..
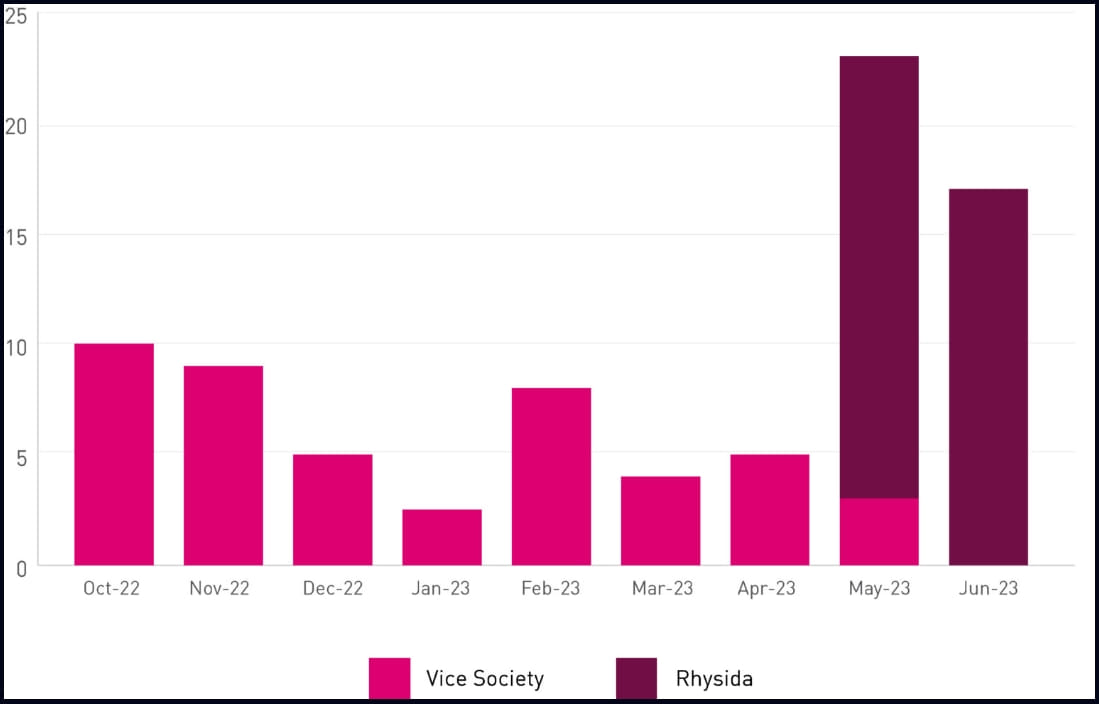
In conclusion, Rhysida has established itself in the ransomware space quickly, targeting organizations in various sectors and showing no hesitation in attacking hospitals.
Although the RaaS appeared to move too quickly in terms of operations while the technical aspect lagged behind, developments on that front show that the locker is catching up.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

