ROPDump – A Command-Line Tool Designed To Analyze Binary Executables For Potential Return-Oriented Programming (ROP) Gadgets, Buffer Overflow Vulnerabilities, And Memory Leaks
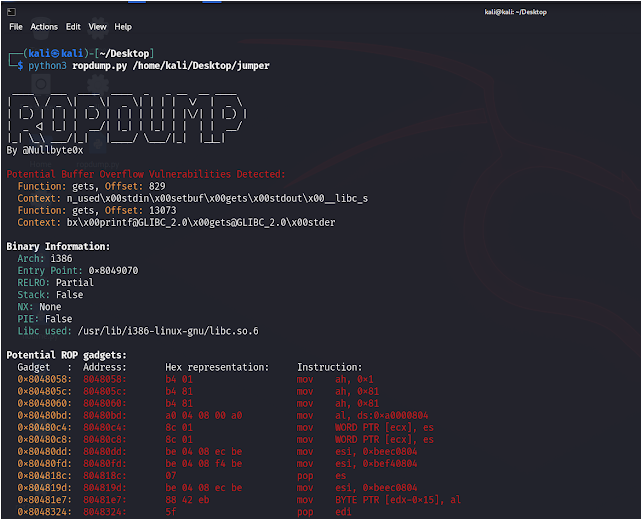
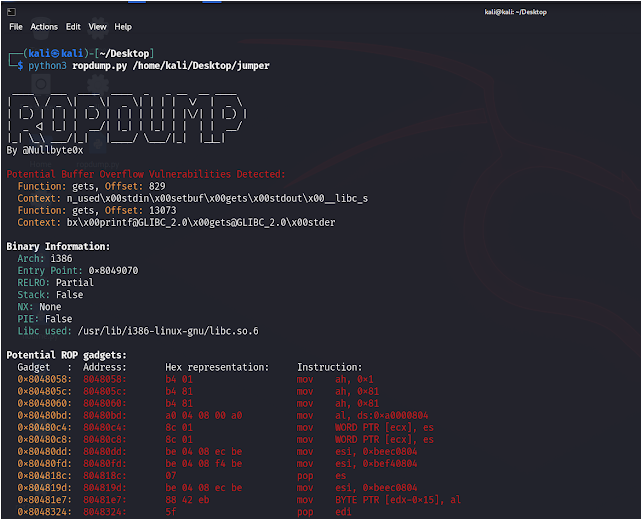
ROPDump is a tool for analyzing binary executables to identify potential Return-Oriented Programming (ROP) gadgets, as well as detecting potential buffer overflow and memory leak vulnerabilities.
Features
- Identifies potential ROP gadgets in binary executables.
- Detects potential buffer overflow vulnerabilities by analyzing vulnerable functions.
- Generates exploit templates to make the exploit process faster
- Identifies potential memory leak vulnerabilities by analyzing memory allocation functions.
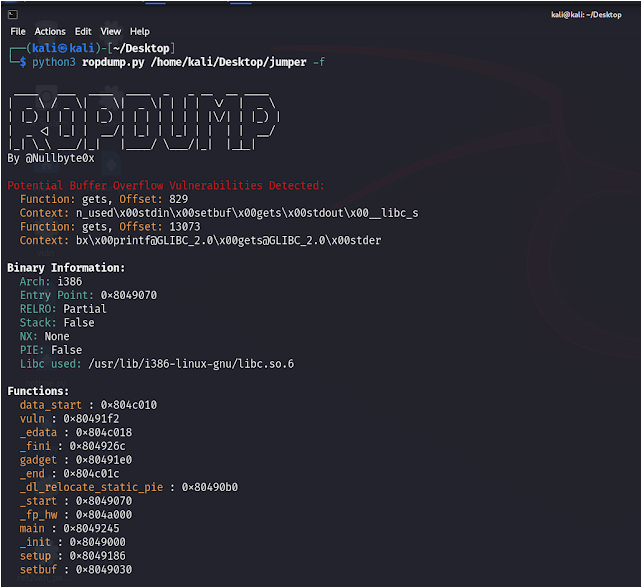
- Can print function names and addresses for further analysis.
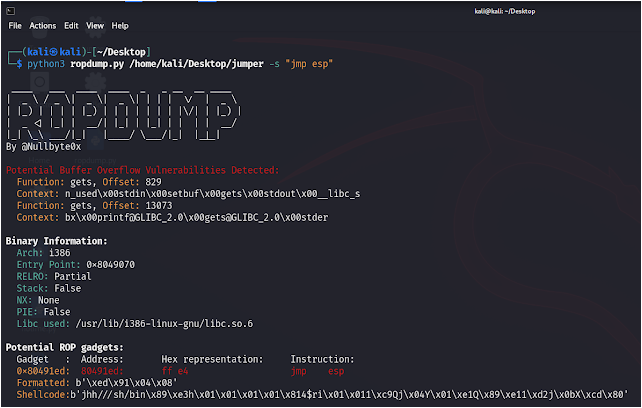
- Supports searching for specific instruction patterns.
Usage
<binary>: Path to the binary file for analysis.-s, --search SEARCH: Optional. Search for specific instruction patterns.-f, --functions: Optional. Print function names and addresses.
Examples
- Analyze a binary without searching for specific instructions:
python3 ropdump.py /path/to/binary
- Analyze a binary and search for specific instructions:
python3 ropdump.py /path/to/binary -s “pop eax”
- Analyze a binary and print function names and addresses:
python3 ropdump.py /path/to/binary -f
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.



![Cobalt Strike Beacon Detected - 119[.]45[.]29[.]172:8089 8 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
