Royal Mail phish deploys evasion tricks to avoid analysis
Royal Mail phish scams are still in circulation, slowly upgrading their capabilities with evasion tools deployed in far more sophisticated malware attacks.
Often, the quality of sites we see varies greatly. Many fake Royal Mail pages are cookie-cutter efforts existing on borrowed time. The operators know their scam is a case of here today, gone tomorrow. These bogus pages are often taken down quickly by hosts. As a result, many exist in an effort-free zone of “graphic design is my passion”.
Sometimes these sites will lift bits and pieces from the official pages they happen to be imitating. This can take the form of stolen image files, and in other cases they’ll simply hotlink the live images or design instead.
But what we haven’t seen while digging into these fake portals is a smattering of what looks to be researcher deterrents. That is until now.
Shutting down the investigation
Malware authors often obscure the inner working of their code, or prevent files from executing inside a virtual machine. A lot of analysis is done inside VMs, because it’s cheaper and less time consuming than infecting a “real” PC and then rolling everything back. This is why malware frequently looks for clues that it’s sitting inside a virtual environment, and then refuses to do anything.
Similarly, malware portals rely on the right kind of traffic. There’s no point spending a fortune on an exploit kit if potential victims aren’t running the outdated software required. Redirection Gates act like a kind of bouncer, making sure the right name is down on the list. Running an old version of Flash? Come on in. A fully patched system running security software? Sorry, this is an exclusive party.
Another similar check made by malware files when sitting in a virtual testing environment is to look for mouse movements and general desktop activity like an absence of PC screens/monitors. If none of that is happening, if no screen displaying the desktop is in evidence, the malware assumes “malware research” and doesn’t come out of its shell.
Finally, we come to phishing pages. Some phishes are aimed at mobile users only, and will check the browser’s referral agent. If it says “Chrome, desktop” the site will send the visitor away. If it says “Chrome, mobile” they’ll be allowed into the heart of the phish. What we have with this Royal Mail fake out, is an added layer of sophistication. This is, in effect, the malware portal bouncer on the door, but now they’re yelling about parcel deliveries.
Shall we take a look?
The Royal Mail phish in action
It begins with the usual SMS message claiming that a parcel has been redirected, and reads as follows:
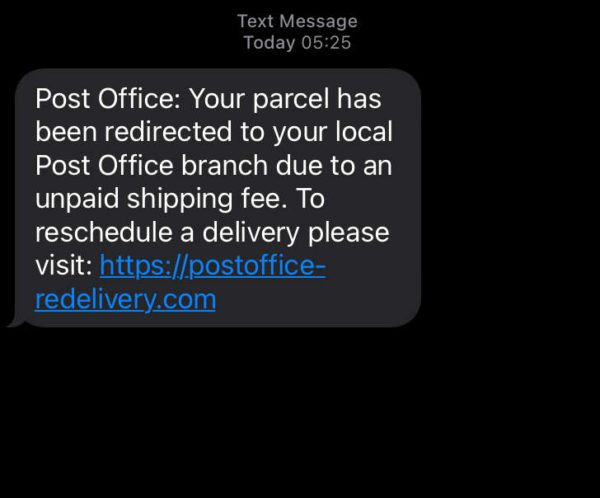
Post Office: Your parcel has been redirected to your local post office branch due to an unpaid shipping fee. To reschedule a delivery please visit: [URL removed]
Something to note here is how much closer this is to actual Royal Mail processes. Our last example from March simply made vague references to parcels waiting for delivery. A lot of people would hopefully suspect something was suspect as a result. Here, parcels with no postage are indeed sent to the nearest Post Office to arrange a collection.
For anyone familiar with the more generic SMS blasts from this attack, this may well be the foot in the door the attacker needs.
A virtual phish? No thank you
Remember what we said about sites filtering you in or out of the scam, depending on your setup? That’s what we have here. When you click the link to visit the fake Royal Mail page, there’s a fair bit of code under the hood sniffing around for potential virtual machine use.
The below code tests for WebGL renders which it may associate with (for example) VirtualBox or RDP (Remote Desktop Protocol). It also wants to know if site visitors have a display or not. Remember, not having a screen is a possible sign of automated research tools in virtual machines. This is a tactic pulled right out of malware analysis evasion land.
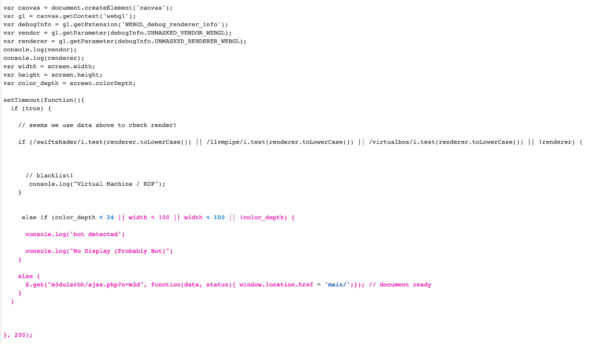
Finally, the site throws a lot of placeholder text into the website’s code. This text seems to cause plenty of errors in Tor browser. Tor is another way for people researching sites to help keep themselves anonymous, so this is a smart move on the phish page creator’s part.
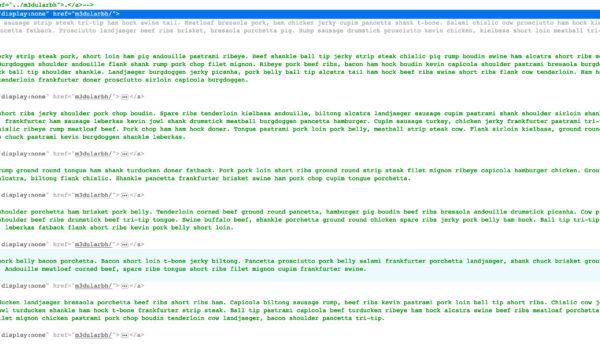
For those curious, the text performs the placeholder function of Lorem Ipsum text. In this case, it’s actually called Bacon Ipsum. While breaking Tor could be accidental, it seems too good to be true given the other measures on display.
Again, this isn’t a level of phish-based paranoia we’ve seen in fake Royal Mail land. Code which breaks Tor, checking for absent computer screens, sniffing for code which may denote a VM or RDP…this is an all new level of the bouncer on the door concept.
What does this Royal Mail phish do?
Assuming the bouncer lets someone in, the flow is a fairly standard Royal Mail phish scenario. The scammers ask for name, DOB, address, mobile number, and email address.
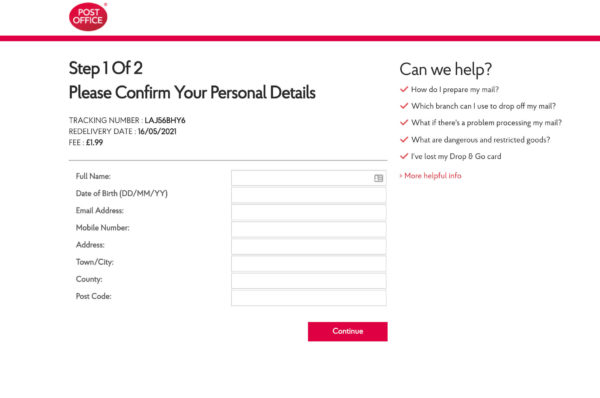
After that, the victim is asked to hand over what are essentially full banking details via the information on their debit card. That’s name, card number, expiry date, security code, account number and sort code.
If payment details are fully entered and submitted, the site pops a message to thank the victim for payment. “Your parcel will be sent out soon, and we will notify you when it is out for delivery”.

At this point, there’s a redirection off to the real Royal Mail website. We’d suggest the only thing left is to call the bank and sort out a replacement card / account block as soon as possible.
Returning a scam to sender
We’ve already looked at how devastating these attacks can be. Attackers are becoming smarter and more selective about who they want to snare in their trap. Making it harder for researchers makes it easier for them, so we all have a vested interest in bypassing these fakes and knowing what to look for. If you or your family members are worried about Smishing, we have just the thing. Fake Royal Mail messages aren’t going away anytime soon, so please keep your guard up and double check those messages. If in doubt, contacting your local depot is likely the best response you can make.
The post Royal Mail phish deploys evasion tricks to avoid analysis appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[Palo Alto Networks Security Advisories] PAN-SA-2025-0016 Chromium: Monthly Vulnerability Update (October 2025) 7 Palo_Alto_Networks_Logo](https://www.redpacketsecurity.com/wp-content/uploads/2025/02/Palo_Alto_Networks_Logo-300x55.png)

