Rudy Giuliani’s Twitter mishaps invite typosquatters and scammers
Former cybersecurity czar Rudy Giuliani has been targeted by typosquatters on Twitter, thanks to copious misspellings and other keyboarding errors made in a number of his public tweets. In a tweet sent out on Sunday, Giuliani meant to send his 650,000-plus followers to his new website, RudyGiulianics.com. Instead, a space added after “Rudy” sent users on a redirection quest that ultimately landed on a web page laced with adware.
Typosquatting has long been used as a way to capitalize on mistakes made by those with clumsy fingers. A mistyped URL, which would normally lead users to a 404 error page, is instead redirected to a completely unrelated site—often one designed for ill intent. For example, let’s say you enter yotube.com into your browser’s address bar instead of youtube.com. Rather than seeing the normal YouTube portal, you will instead be redirected via a few ad networks and most likely end up to a scam page, thanks to the handy work of enterprising typosquatters.
Typosquatting can be a profitable business, as threat actors will register domains lexically close to big brand names or popular websites for heavy traffic gains. The end goal isn’t always to monetize via malvertising redirections—it could be phishing, data theft, or even hacktivism.
In Giuliani’s case, a public political figure has been identified by cybercriminals for his tendency toward typo-laden tweets. In fact, Giuliani’s Twitter account contains numerous tweets with misspellings around his personal website that sometimes lead to trolling attempts or redirect to malvertising schemes. We examine a few of these instances.
Typo leads to political trolling
Here’s a tweet sent from Giuliani’s account using an iPad. Whoever composed that tweet forgot to add a space between the word “Watch” and “rudygiulianics.com”.
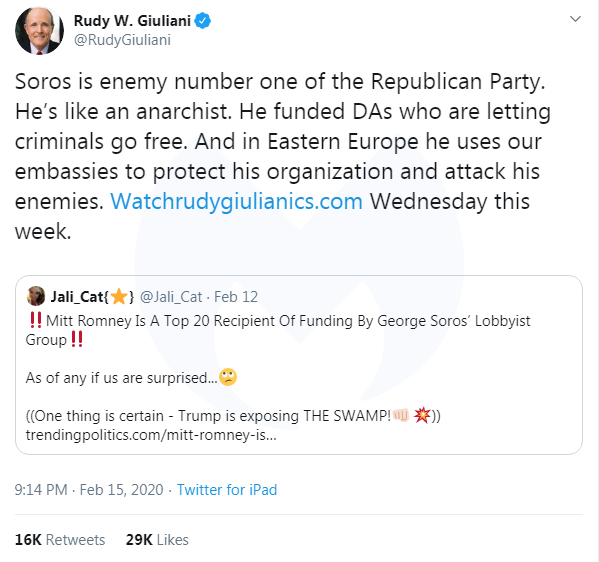
As a result, the website becomes Watchrudygiulianics.com which was registered a day after the tweet:
Domain Name: watchrudygiulianics.com Registrar: GoDaddy.com, LLC Creation Date: 2020-02-16T05:23:50Z
Visiting the site immediately redirects users to https://www.drugrehab.com/treatment/, a site for help with substance abuse.
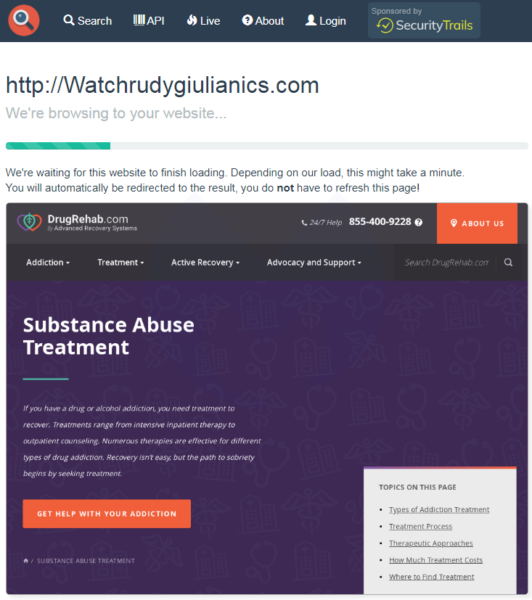
In another example, we see a much more subtle typo for Giuliani’s website, where a single ‘i’ is missing in RUDYGIULIANCS.com (the correct site is rudygiulianics.com).
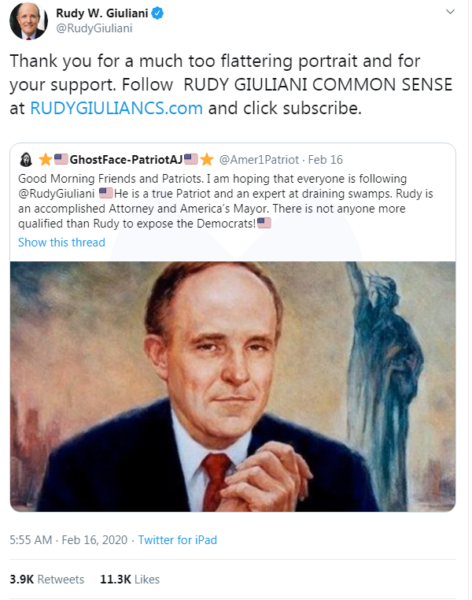
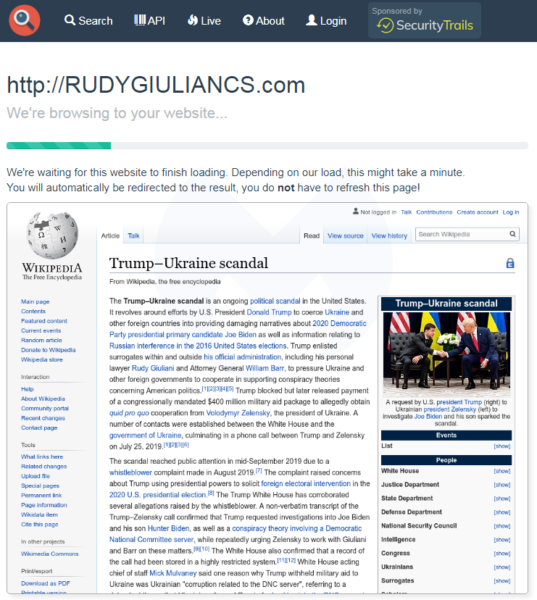
The domain rudygiuliancs.com was also registered recently (but before the tweet came out, so it either was preemptive registration for a forthcoming typo or perhaps the typo had been made already).
Domain Name: rudygiuliancs.com Registrar: Wild West Domains, LLC Creation Date: 2020-02-07T16:30:38Z
This time, visiting this link redirects visitors to a Wikipedia page for the Trump-Ukraine scandal:
Malvertising and other traffic schemes
As mentioned earlier, typosquatters will typically watch popular domain names and register new ones that are likely going to be a result of a typo. Because Giuliani has over 650,000 followers on Twitter and is a well-known political figure regularly in the headlines, scammers know he’s a good source of potential web traffic purely from typosquatting.
In Sunday’s example, a typo led to a malvertising scheme. This time, a space was inserted between “Rudy” and “Giulianics.com”.
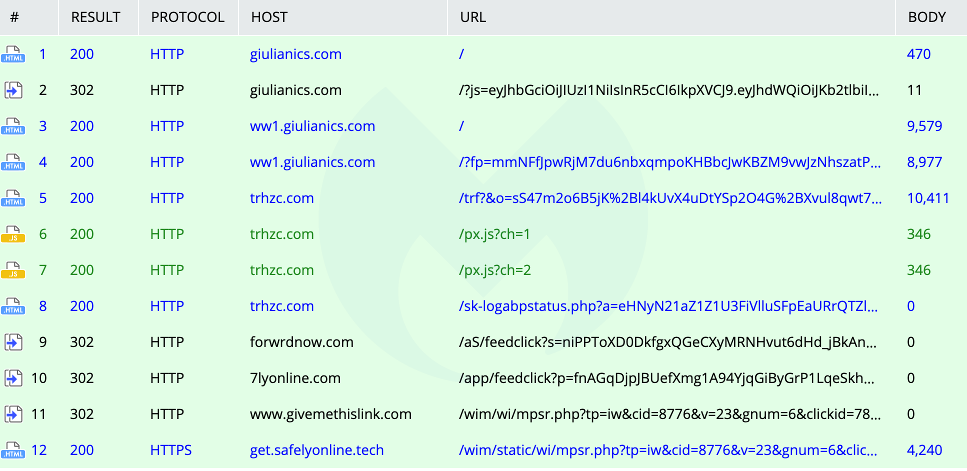
This typo resulted in a link to Giulianics.com, a domain registered at the end of January.
Domain Name: giulianics.com Registrar: GoDaddy.com, LLC Creation Date: 2020-01-31T20:29:50Z
As seen in the image above, a series of redirects will happen once you visit that domain. This is typical for malvertising chains that fingerprint your browser and other settings in order to deliver the appropriate payload.
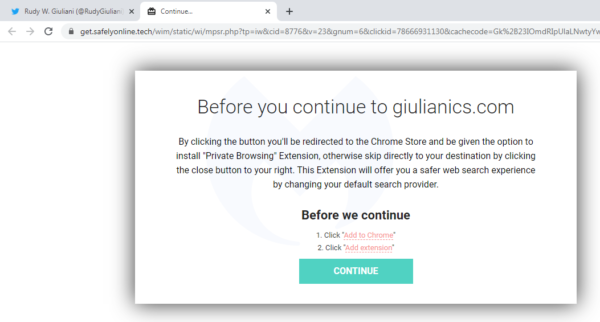
In this instance, visiting from the United States via Google Chrome, we were served a browser extension called Private Browsing:
Although we did not examine the extension in detail, several comments from the Google Play Store say the extension was forced while browsing the web.
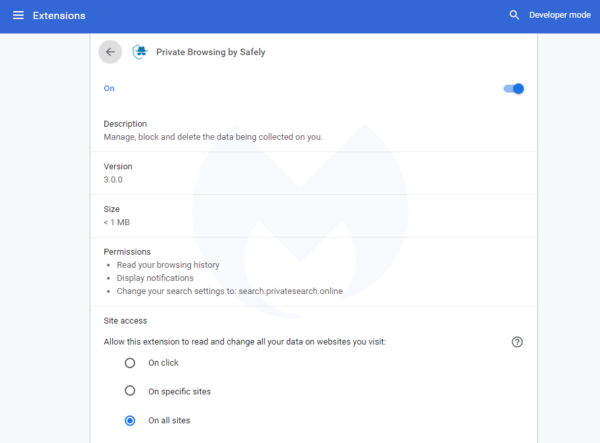
Among other capabilities, it can read your browser history, the data you enter on sites, and can change your default search engine. As a rule of thumb, it is generally recommended to refrain from installing too many browser extensions, especially when they are promoted via unwanted redirects.
In late January, there was a report that visiting Giuliani’s website distributed malware. We weren’t able to confirm it at that time, but in light of the current typo situation, we believe it’s more likely that one of the tweets containing the wrong link led to a malvertising chain, and possibly to a browser locker.
Monitoring popular accounts for mistakes
Many attacks we see in the wild are opportunistic, praying on the latest news or events likely to draw attention. There’s also always been great interest in popular social media accounts, but typically by hacking them directly. In this case, opportunistic actors are waiting for the next typo to happen in order to push out their own message or to monetize on it via malicious redirects.
This serves as a reminder that even well-known or verified social media accounts can send users in unintended directions leading to scams or malware. In a sense, any kind of communication can be abused for an attacker’s own gain by recognizing a pattern of predictable mistakes and immediately acting upon them.
For those wanting protection against such redirections and other malicious website activity, Malwarebytes offers a free browser extension that takes an aggressive stance on blocking malvertising and other dubious schemes.
The post Rudy Giuliani’s Twitter mishaps invite typosquatters and scammers appeared first on Malwarebytes Labs.

