SaltStack Pre-Authenticated Remote Root (CVE-2020-16846 and CVE-2020-25592): What You Need to Know
What’s up?

We start the November critical vulnerability season with a pair of CVEs—CVE-2020-16846 and CVE-2020-25592—that, when combined, can result in unauthenticated remote root access on a target system. SaltStack developers disclosed these weaknesses on Nov. 3, 2020 and have released patches for these weaknesses.
Before reading on, Rapid7 advises all SaltStack users to patch their systems as quickly as possible. If at all possible, please don’t wait for your typical patch cycle to apply SaltStack security updates. There are no known mitigations or workarounds as of Nov. 9, 2020. As noted in the aforelinked AttackerKB Rapid7 analysis: “Pre-authenticated remote root is the gold-medal standard for attackers, and it took Rapid7 researchers all of 15 minutes and a single HTTP request to get there.”
SaltStack vulnerability information, exposure details, and attacker activity
SaltStack developers noted that the following versions are affected:
- 3002
- 3001.1, 3001.2
- 3000.3, 3000.4
- 2019.2.5, 2019.2.6
- 2018.3.5
- 2017.7.4, 2017.7.8
- 2016.11.3, 2016.11.6, 2016.11.10
- 2016.3.4, 2016.3.6, 2016.3.8
- 2015.8.10, 2015.8.13
While none of the CVEs have a rating (yet), these combined weaknesses are trivial to exploit and result in complete system compromise, which will happen, since CVE-2020-11651, another SaltStack vulnerability from April 2020, was exploited quickly by threat actors. We fully expect CVEs 2020-16846 and 2020-25592 to follow that same path.
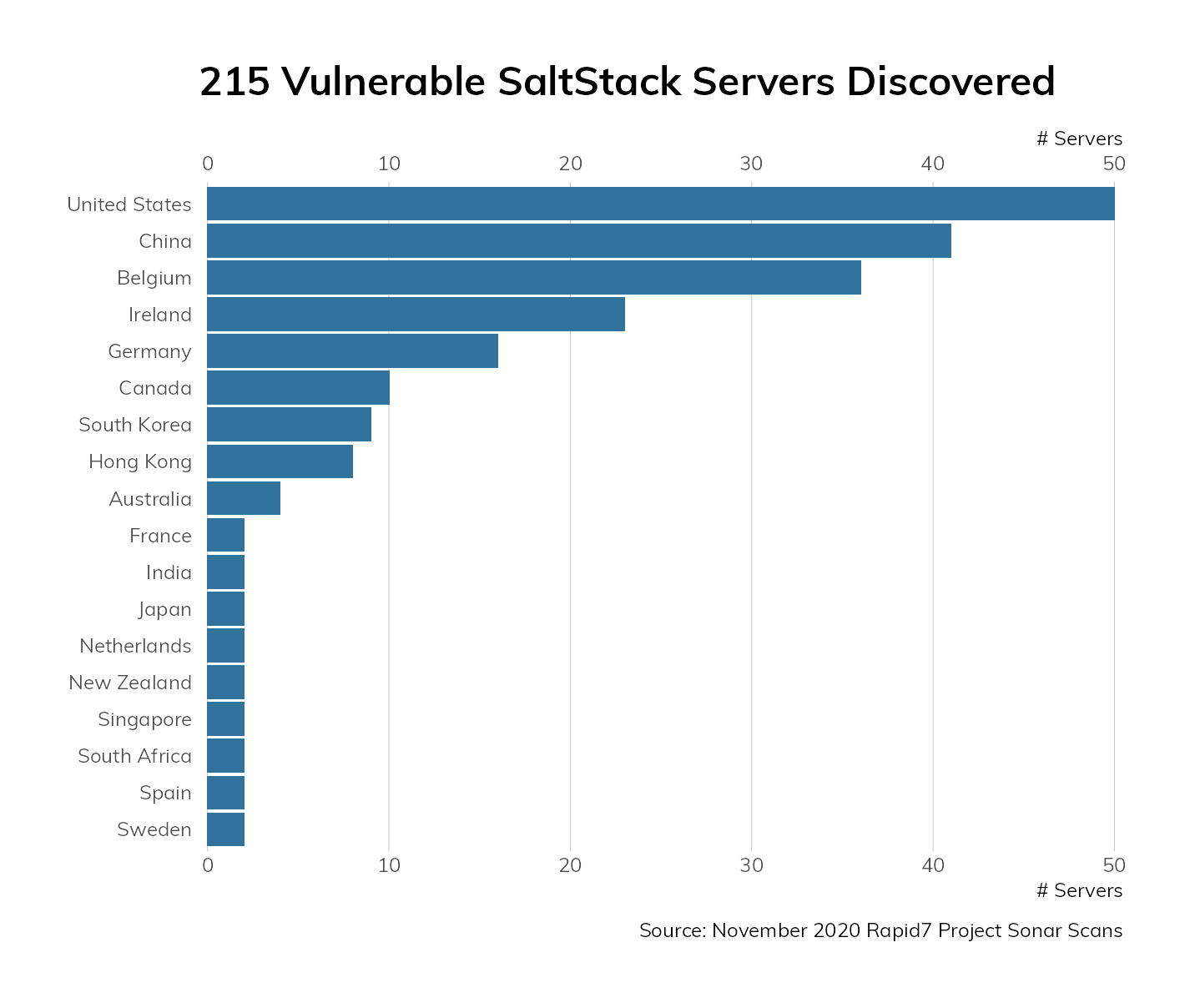
Rapid7 Labs thankfully only discovered 215 vulnerable SaltStack servers in November 2020 scans, but that doesn’t mean your internal SaltStack nodes will not be identified and compromised by attackers who gain footholds as a result of phishing attacks.
There are no mitigations for these vulnerabilities. You must patch your systems to be safe. As of Nov. 9, 2020, Rapid7 Labs Project Heisenberg, our global honeypot network, did not detect any malicious SaltStack activity, but that will likely change very quickly.
Final guidance
Along with patching, organizations should monitor SaltStack API logs very closely for anomalous activity going back to at least Nov. 3, 2020 and until/after affected SaltStack systems are patched.
Given that there have been two severe SaltStack weakness episodes in one calendar year, Rapid7 further suggests organizations increase monitoring for anomalies in general on SaltStack systems and stay on top of vulnerability announcements from the SaltStack developers.
Vulnerable to CVE-2020-16846 and CVE-2020-25592? Scan Your Environment Today to Find Out.
Get Started
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![Cobalt Strike Beacon Detected - 166[.]88[.]2[.]184:80 4 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
