Security researcher stopped at US border for investigating crypto scam

Security researcher Sam Curry describes a stressful situation he encountered upon his return to the U.S. when border officials and federal agents seized and searched his electronic devices.
Curry was further served with a ‘Grand Jury’ subpoena that demanded him to appear in court for testimony.
Why, you ask? All because his IP address landed in the logs of a crypto wallet associated with a phishing scam that Curry had earlier helped investigate as a part of his job—a scam that the feds were now investigating.
The unusual suspects
This week, ethical hacker and security researcher Sam Curry shared how he ended up being investigated by the feds, ironically simply for doing his investigative job.
Curry describes he had just returned to the U.S. from Japan when he was directed towards the secondary inspection area by officials from the IRS Criminal Investigation (CI) division and the U.S. Department of Homeland Security (DHS) that also oversees Customs & Border Protection (CBP).

(BleepingComputer)
Curry further told BleepingComputer that he had arrived at the Dulles International Airport, Virginia, which is in close proximity to Washington, DC. He was, however, served a subpoena issued by the Southern District of New York demanding his appearance at the court for testimony:

“After they’d questioned me, I was asked to leave the room while they sat and searched through my unlocked device for another hour,” the researcher shared on X (Twitter) in a thread that has now been deleted.
“At this point I’d been given almost no information on whether or not I was a subject, witness, or anything related to the case at all.”
“Once they were finished, I was told that I could leave and immediately contacted a lawyer. Over the next few days, the lawyer spoke with the AUSA and also the IRS-CI and DHS agents. They learned that I was the target of the grand jury subpoena and for a really silly reason…”
Researcher’s IP address lands in logs
The reason involved Curry’s role as an investigator of a crypto scam, he explains.
In December 2022, the researcher helped probe into a crypto phishing website that had stolen millions of dollars.
“In the JavaScript of the website, the scammer had accidentally published their Ethereum private key. Sadly, I’d found it 5 minutes too late and the stolen assets were gone.”
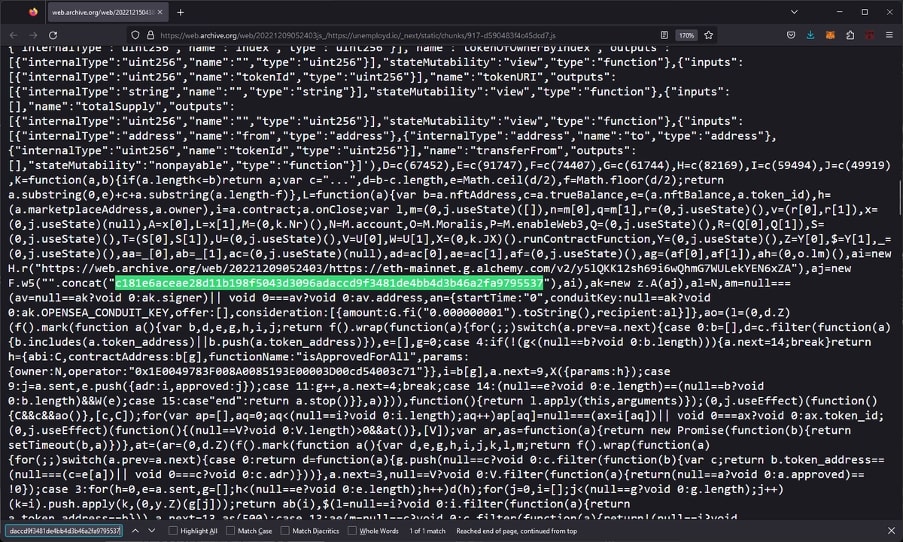
“During this process, I’d imported the private key into my MetaMask and navigated to OpenSea to check if there was anything left in the wallet. When I did this, I was on my home IP address and obviously not attempting to conceal my identity as I was simply investigating this,” wrote Curry.
“The agents had requested the authorization logs of the account from OpenSea and saw that my IP. They subpoenaed the IP, found out who I was, then decided to use immigration as an excuse to ask for my device and summon me to a grand jury, rather than just email me or something.”
Thankfully, Curry’s attorney, after emailing the federal agents back and forth was able to clarify the situation and have the “subpoena completely dismissed” after confirming that all data from the researcher’s device had been deleted.
Could all the trouble and extra time and resources relentlessly spent by the prosecution in this case have been avoided by a simple telephone call? Possibly.
Curry describes that the investigating agents had a “manila folder” with his photo, Twitter, social media, and other details in it, “and I would have assumed that they would have looked into it a little bit… Even just a brief read… just who I am and what I do I feel it would have cleared things up a lot.”
It is worth noting, that Curry is an established web app security researcher in the field who has previously discovered and responsibly reported flaws in the APIs of Toyota, Mercedes, BMW, among other automotive companies.
The researcher has earlier identified security vulnerabilities in airline rewards program systems that allowed snatching “unlimited” air miles. Curry had also disclosed the Uber internal systems breach that involved the theft of the company’s vulnerability reports.
“It’s odd to me that they didn’t see I work as a security engineer who responds to these things regularly,” says Curry.
However, recent occurrences where a (malicious) hacker later claims they were conducting ‘ethical research’ and university researchers circumventing what constitutes ‘ethical’ have made it all a legal gray area for everyone involved, including prosecutors.
In any case, Curry’s motivation to share his story is to spread awareness for defenders and ethical hackers. Merely having the title of a “security researcher” won’t exempt you from the scrutiny of law enforcement agencies should your IP address or system fingerprint get caught up in assets pertaining to criminal activity.
“I’m sharing this because I think it’s something people should be aware of if they’re doing similar work. It was widely shared that the private key was leaked and my background as a security researcher wasn’t enough to dissuade using [Immigration] and a grand jury to intimidate me.”
BleepingComputer contacted the DHS, CBP, and IRS CI with questions well in advance of publishing but we have not heard back.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

