Shutdown Kaseya VSA servers now amidst cascading REvil attack against MSPs, clients
A severe ransomware attack reportedly taking place now against the popular Remote Monitoring and Management software tool Kaseya VSA has forced Kaseya into offering urgent advice: Shutdown VSA servers immediately.
“We are experiencing a potential attack against the VSA that has been limited to a small
number of on-premise customers only as of 2:00 PM EDT today,” Kaseya wrote on Friday afternoon.
“We are in the process of investigating the root cause of the incident with an abundance of caution but we recommend that you IMMEDIATELY shutdown your VSA server until you receive further notice from us.
It’s critical that you do this immediately, because one of the first things the attacker does is shutoff administrative access to the VSA.”
The attack is reportedly delivered through a Kaseya VSA auto-update that maliciously pushes the Revil ransomware onto victims’ machines. Kaseya is a popular software developed for Managed Service Providers that provide remote IT support and cybersecurity services for small- to medium-sized businesses that often cannot afford to hire full-time IT employees, due to their limited size or budgets.
Complicating the attack is the fact that, according to cybersecurity researcher Kevin Beaumont, the malicious update carries administrator rights for clients’ systems, “which means that Managed Service Providers who are infected then infect their client’s systems.”
For a company that says it has 40,000 customers, this could be a disaster.
During the attack, the cybercriminals reportedly shut off administrative access to VSA, and several protections within Microsoft Defender are disabled, including Real-Time Monitoring, Script Scanning, and Controlled Folder Access.
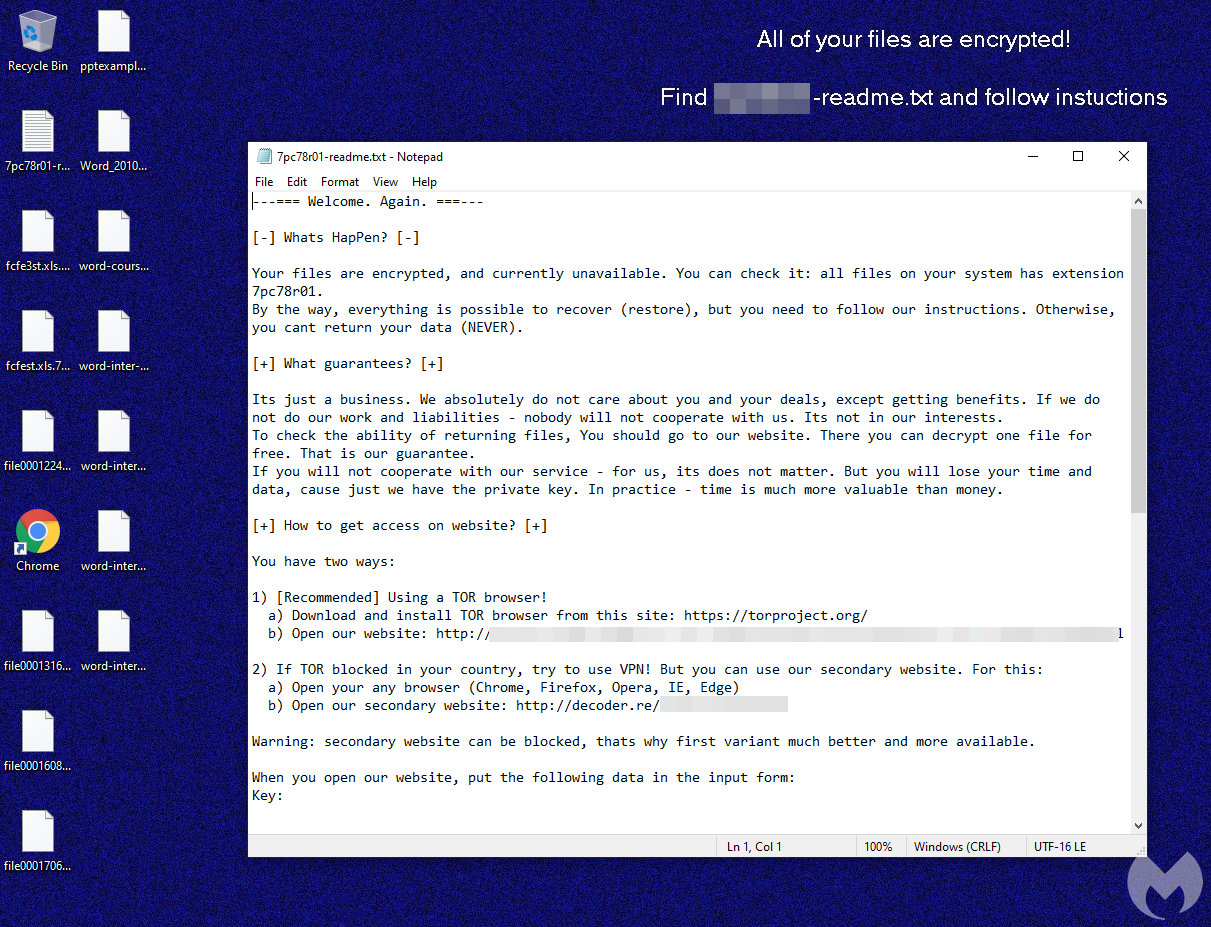
A screenshot from Malwarebytes reveals a ransom note delivered to an infected Windows machine. In the note, attackers warn:
“|—=== Welcome. Again. ===—
[-] Whats HapPen? [-]
Your files are encrypted, and currently unavailable. You can check it: all files on your system has extension 7pc78r01. By the way, everything is possible to recover (restore), but you need to follow our instructions. Otherwise, you can’t return your data (NEVER).”
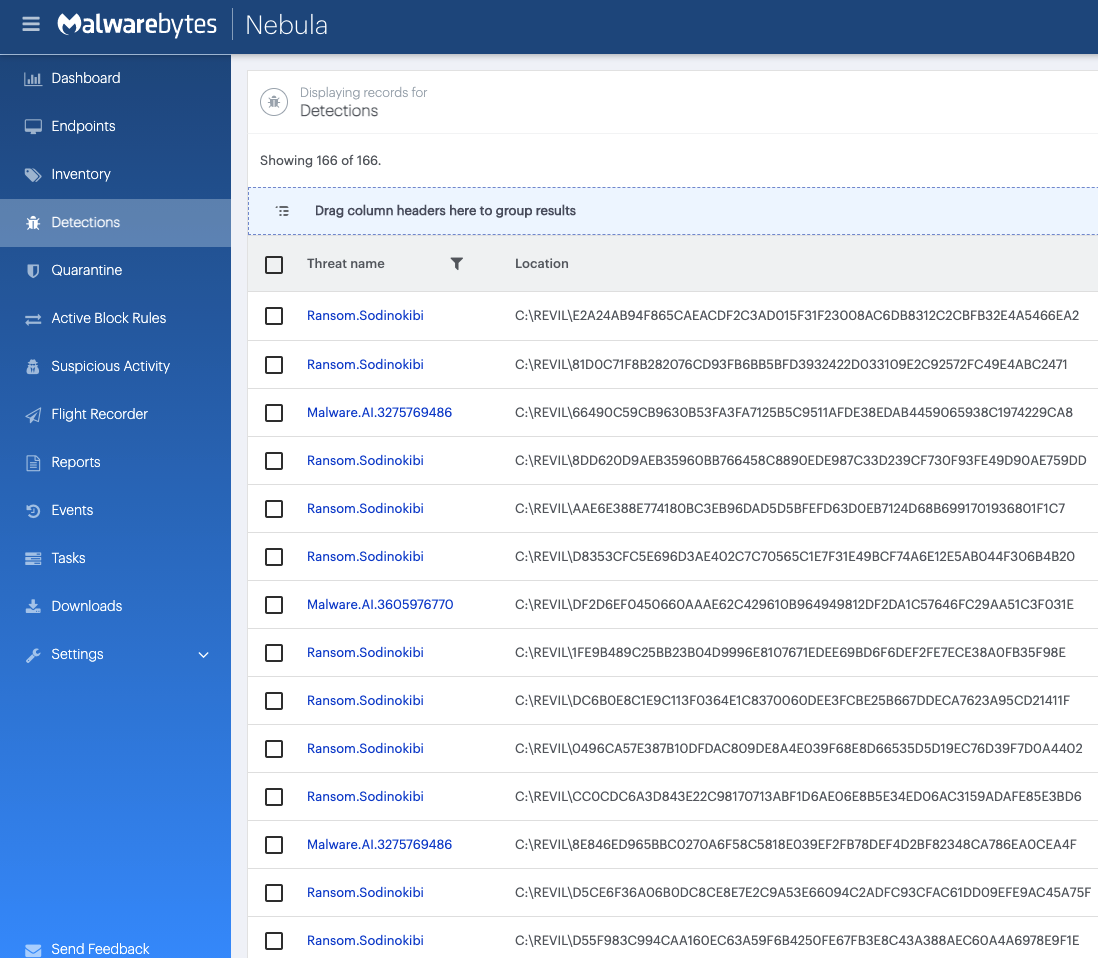
Malwarebytes customers are currently protected from REvil, as shown in the screenshots below, and Malwarebytes is committed to continuing this protection. (Malwarebytes detects REvil as Sodinokibi)
We will update this post with more information as it becomes available, but the immediate guidance from Kaseya cannot be overstated: Shutdown VSA servers immediately.
Indicators of Compromise (IOCs)
Loader
df2d6ef0450660aaae62c429610b964949812df2da1c57646fc29aa51c3f031e
dc6b0e8c1e9c113f0364e1c8370060dee3fcbe25b667ddeca7623a95cd21411f
d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e
aae6e388e774180bc3eb96dad5d5bfefd63d0eb7124d68b6991701936801f1c7
66490c59cb9630b53fa3fa7125b5c9511afde38edab4459065938c1974229ca8
81d0c71f8b282076cd93fb6bb5bfd3932422d033109e2c92572fc49e4abc2471
1fe9b489c25bb23b04d9996e8107671edee69bd6f6def2fe7ece38a0fb35f98e
REvil/Sodinoki DLL
d8353cfc5e696d3ae402c7c70565c1e7f31e49bcf74a6e12e5ab044f306b4b20
d5ce6f36a06b0dc8ce8e7e2c9a53e66094c2adfc93cfac61dd09efe9ac45a75f
cc0cdc6a3d843e22c98170713abf1d6ae06e8b5e34ed06ac3159adafe85e3bd6
0496ca57e387b10dfdac809de8a4e039f68e8d66535d5d19ec76d39f7d0a4402
8e846ed965bbc0270a6f58c5818e039ef2fb78def4d2bf82348ca786ea0cea4f
8dd620d9aeb35960bb766458c8890ede987c33d239cf730f93fe49d90ae759dd
The post Shutdown Kaseya VSA servers now amidst cascading REvil attack against MSPs, clients appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[QILIN] - Ransomware Victim: Long Island Weight Loss Institute 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

![Cobalt Strike Beacon Detected - 20[.]74[.]209[.]192:8081 7 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
