SMS System Now A Long-Gone Era; Google Brings Out A New Update

With the rise of encrypted alternatives of SMS messages, WhatsApp, iMessage, and Signal, the SMS system has become a ‘throwback to a long-gone era’.
But ironically, that same SMS system has additionally been on the rise as the default delivery mechanism for most two-factor authentication (2FA) codes.
The issue is being viewed as a critical one in light of the fact that an SMS is delivered to a phone number with no user authentication—biometric or password security efforts secure our physical devices, not our numbers, they are separated.
What’s more, this explanation alone clears a path for SIM-swapping, social engineering scams to take those six-digit codes, to malware that catches and exfiltrates screenshots of the approaching messages. For each one of those reasons, and a couple of additional, the advice is currently to avoid SMS-based 2FA if feasible for the user.
But still, if the user can tie 2FA to the biometric or password security of a known device, at that point this is a huge improvement. Apple does this splendidly. And Google is quick on making this the default also.
In a blog post on June 16, Google confirmed “Starting on July 7 we will make phone verification prompts the primary 2-Step Verification (2SV) method for all eligible users.”
Their plan fundamentally is to switch Google account holders to this setting, forestalling the majority, essentially defaulting to an SMS message or voice call.
Yet, there’s a drawback with this too , in light of the fact that all devices a user is logged into will receive the prompt, and that will require some rejigging for families sharing devices. Furthermore, users who have security keys won’t see a change.
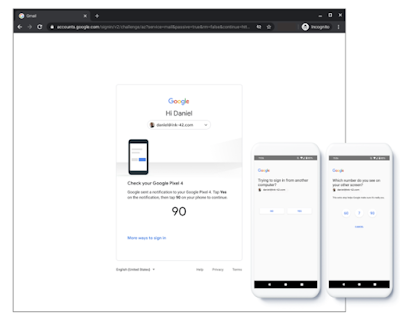 |
| Phone prompt 2FA |
In the event that the phone prompt doesn’t work for the user, they can get away to an SMS during the verification process—however, Google doesn’t recommend this.
Further explaining that this move is both progressively secure and simpler, “as it avoids requiring users to manually enter a code received on another device.”
In taking the decision to make this the “primary technique” for 2FA, Google says “We hope to help [users] take advantage of the additional security without having to manually change settings—though they can still use other methods of 2-Step Verification if they prefer.”
For an attacker to spoof this system they will require physical access to one of the user’s already logged-on devices where they will see the prompt. Users will likewise have the option to audit and remove devices they no longer need to gain access to this security option.
Also, on the grounds that the prompt hits all logged-on, authorized devices all at once—user will straight away know whether an attempt is being made to open their account without their knowledge.
Nonetheles, with the increasing utilization of multi-device access to our various platforms, it is an extraordinary thought to utilize an authentication device to verify another logon and this step by Google has without a doubt emerged as an incredible one in the direction way which should be followed by others as well.


